
Just yesterday after the bitshares investment post, it hit me that many of us need be aware of what we do with our computer systems or mobile devices.
This post is meant to cover everything you did not know about computer and its viruses
Personally as a blogger and web developer, I find it attractive to as well mine cryptos with my system, afterall they all go together.
Lets cut the story short and get down the DM
Computer viruses can wreck havoc to the operations of the computer.
A computer virus is a type of malware that is intentionally written to gain entry into your computer, without your knowledge or permission. It has the capacity to modify or replicate itself, in which case it will continue spreading.
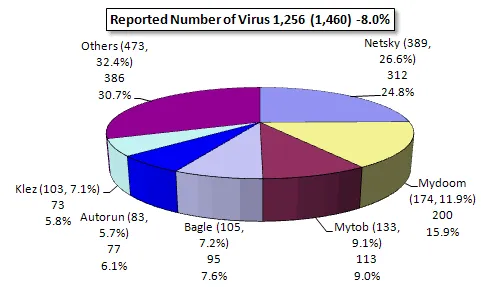
There are varying different types of computer viruses and their effects also vary widely. While some simply replicate themselves, others adversely affect the programs and consequently, the system’s performance. This therefore underlines the importance of not assuming that the virus is harmless and leaving it in the system. It is important that you scan your computer for viruses once in a while, so that you can be sure about its protection.
There are various types of computer viruses, classified in terms of techniques, origin, the types of files affected, damage, OS or Platform attacked, as well as the places they hide.
It’s relatively hard to answer how many different types of computer viruses there are but below covers the main core concepts of the common types:
Resident viruses: These are permanent viruses dwelling in RAM memory. In this case, they would be in a position to overcome, as well as interrupt, all operations that the system executes. Their effects include corrupting programs and files that are closed, opened, renamed or copied.
Overwrite viruses:
These viruses delete information that is in the infected files. In this case, the infected files would be rendered totally or partially useless. Unfortunately, you would only clean the infected file by deleting it completely, therefore losing original content.
Direct action viruses:
This virus replicates itself, then acts when executed. Subject to satisfaction of particular conditions, the virus infects files located in the folders or computer directory. It is also in directories specified in the AUTOEXEC.BAT PATH. In most cases, it is located in hard drive’s root directory and takes particular action when the computer boots.
File infectors:
This virus infects executable files or programs. On running the programs, the virus would be activated, then be able to carry out its damaging effects. Most of the existing viruses are in this category.
Boot viruses:
This virus infects the hard disk’s or floppy drive’s boot sector. This would make the computer unable to boot. These viruses can, however, be avoided by ensuring that the floppy disks and hard drive is well protected. Never start the computer using an unknown disk drive or floppy disk.
Directory viruses:
This virus alters the paths indicating a file’s location. In this case, when the infected program is executed, you will be running the program unknowingly, since the virus has moved the original program and file to another location. This therefore makes it impossible to locate the moved files.
Macro virus:
This virus affects files created using particular programs or applications containing macros. The mini-programs increase their ability to automate some operations, in which case they would be performed as single actions. The user would therefore be saved the trouble of executing them singularly.
E-Mail Virus:
Worth listing even if most are Macro viruses. Generally these kinds of viruses infect computers through social interaction with someone who e-mails the end user. They may be asked to verify a billing statement or look at an invoice attachement. Upon opening the attachment the macro is fired off and runs and infected the computer. Most macro viruses are easily stopped by simply keeping software up to date on computers.
Ransomware:
Ransomware is type of malicious software product that attempts to hold a computer for ransom. This might be locking files, hiding files, changing permissions on files or encrypting files.
In early ransome attacks files where often simply hidden from the viewers and a monetary payment was requested to un-do the changes. This kind of attack was rather simple to resolve by doing a system restore to un-do the changes to those files.
As Ransomware evolved they started to encrypt files from users which no system restore would be able to resolve. The core Windows files would be fully functional but personal files and folders would be changed leaving the end user with no access to those files unless a payment was sent to the make of the ransomware software.
As Crypto currencies such as Bitcoin arrived on the market ransomware became more prevalent as makers could have people send them bitcoin to a wallet address which they then could send out to multiple wallets and make the tracing of the coins hard to follow.
With the release of NAS hacking tools on the black market an increase in sophisticated ransomware attacks occurred in early 2017 including the wannaCry https://en.wikipedia.org/wiki/WannaCry_ransomware_attack attack which affected hundreds of companies around the world including government agencies such as the British National Health Service.
Browser Highjacks:
The most common types of viruses seen in 2014 – 2015 that have a high impact on users are Browser Highjack viruses. Generally this type of infection is not really a virus but something called PUP or Potentially unwanted software. In most cases these browser highjacks change the users home page and search settings in the web browser and often make it extremely hard to remove and restore the default settings. Often times these kinds of browser highjacks get installed from bundled software that may include free programs such as computer games or wall papers.
First Known Computer Virus
The first known computer virus appeared in 1971 and was called the Creeper virus. This specific virus targeted select main frame computers running TENEX.
To delete this virus a program was created by Ray Tomlinson called the Reaper which was actually another virus whose sole purpose was to delete the Creeper virus. Essentially this was the second known computer virus but some also refer to it as the first anti-virus client.
John McAfee released the first version of a Virus Scanner in 1987 which kicked off the creation of McAfee antivirus.
Virus Prevention
The only solution to never risk getting a computer virus is to keep the computer disconnected from the internet and off which is not practical.
That being said you have many options that can greatly reduce the risk of getting a computer virus.
Keep your operating system up to date.
Microsoft, Apple and Linux have updates that roll out on a regular basis. Keeping your operating system up to date alone will stop the vast majority of known threats.
The Wanna Cry ransomware is a good example of this. System affected by this virus were those running Windows XP which stopped having updates to the program because of newer replacements such as Vista, Windows 7, Windows 8 and Windows 10.
Keep your web browser updated.
Nearly all web browsers have an auto update feature that allows you to auto update your web browser. Popular browsers out there include, FireFox, Chrome, Safari and Edge (formerly known as Internet Explorer)
Keep your software programs updated.
Programs such as Office, Adobe PDF, Flash are all targeted programs due to their wide user base. The more popular a program is the more it’s a target for exploits.
Safe Web Browsing.
Basically don’t use un-trusted websites and you will be 99% of the way there.
Have an Active antivirus client installed that prevents virus infections and keep the program updated.
Do not open e-mails with attachments from unknown senders. Even if it’s known use caution as their e-mail could have been hacked.
Using Anti-virus Software
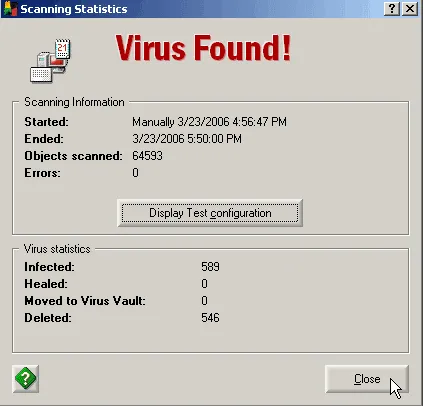
Most people can still install software even when infected with a computer virus. Installing and running a full deep scan of a computer with anti-virus software that is updated often times will remove a computer virus.
Virus Related Scams
Virus related scams have been around for over a decade.
A common scam is simply showing the end user a webpage that tells the user they have a computer virus. Scary wording is often used in an attempt to trick the user into panicking and then making a purchase. Simply closing down the web browser would stop the error messages.
You now see this commonly played out on mobile devices with ads that say the user has several viruses found on their phone and they need to install an app to protect their phone. The app is there simply to push ads constantly when you are browsing the web.
Another popular scam going around where from fake antivirus programs. They would be installed on the users computer without the users permission and nearly cripple the computer from functioning. Strong wording would be used such as a keylogger installed that is tracking all the keys entered into the computer or that the persons bank account can now be accessed remotely. There were hundreds of these fake antivirus programs going around a few years back but most of the holes have been patched security wise from Microsoft and thankfully government agencies around the world have cracked down on those making these fake virus programs and those who where marketing them.
Safe Browsing Habits
There is no full proof system out there to product yourself from getting infected with a virus.
The first recommendation is to have an active antivirus client installed.
The next would be to avoid installing software from vendors you do not trust and only install software from trusted sources.
Avoid websites that spawn lot’s of ads. Porn sites are a lot cleaner than they used to be but they still can carry lot’s of malicious code.
Keep your plugging and extension updated and remove those you no longer use.
Keep your web browser updated and if you still use flash be sure to always have that updated and remove the old flash version.
When checking e-mail avoid opening attachments unless you fully trust the source and even then take caution as that persons e-mail account could of been hacked.
2 Step Authentication
Many e-mail services and social accounts as well as banks now allow for 2 Step authentication. This in it’s simplest terms means you need to have 2 pieces of information to gain access to the system.
Often times this will be your password as well as a security code found that is unique to you that rotates every minute. This is often stored on the end users phone.
While it may sound complicated they are simple programs to use and go a long ways in protecting your online accounts from hackers.
After you enable 2 Step authentication on your first login you are generally asked if you want them to remember your device. If you are on your home computer you can say yes and you won’t have to enter in the second code every time.
If you attempt to login on a different computer you will be challenged again with the second code and would need that to login.
Passwords
It’s a good idea to have separate passwords for every account you have online. This means your facebook account will not have the same password as your bank account or e-mail account.
It can be hard to keep track of dozens of different passwords which is why I recommend all users use a password management program like roboform or Lastpass.
Protecting Your Smart Phone
With smart phone use constantly on the rise more and more threats are being made for Smart Phones. Generally most users have little to worry about and by taking just a few extra measure you can protect you phone and privacy.
It’s a best practice to always have your phone locked when not in use. This will stop someone from gaining access to your mobile device and messing with your personal setting and information.
Only installing apps from trusted sources such as the App Store and Play Store.
Taking caution to remove apps no longer in use on your phone as well as monitoring your phone activity after installing and app. You may love a new game you just downloaded but if you start getting pop ups all the time when browsing the web normally there may be active code in that free app that is pushing advertising onto your phone. Those kinds of apps you should remove immediately.
Credits: www.pctechguide.com
Thank you for your time.
FOLLOW @chukwuebuka