I think it is really important for anybody to know how computers are connected to the Internet.For this reason, I decided to write a blog about it.

First of all we need to know what protocol is. A protocol is a set of rules for communicating data. Networks have to follow these rules to successfully transmit data.
Information that flows over the Internet, or between any two digital devices, does so using protocols. These protocols divide the message into different parts (usually two): One containing the actual data being transmitted, and one containing information regarding the rules of the transmission. In order for a connection to be established, both sides have to understand and use the same communication protocol.
The Internet Protocol (IP) is the method or protocol by which data is sent from one computer to another on the Internet. Each computer (host) on the Internet has at least one IP address that uniquely identifies it from all other computers on the Internet.
Now, one of the major questions to ask ourselves is "Do IP addresses exist without internet connection?"

The answer is yes!

There are two kinds of IP addresses:
1.Public IP
A public IP address is an IP address that can be accessed over the Internet (external).
Your public IP address can be found at What is my IP Address page.
2.Private IP
A private IP address is a non-Internet facing IP address on an internal network(only valid on their LAN). Private IP addresses are provided by network devices, such as routers, using network address translation (NAT).
For instance, let's focus on home network in which we have got a laptop, PC, and a tablet.If they want to communicate with each other they are going to use their private IP addresses, but if they need to access a web server on the Internet the Gateway of this network is going to map their private IP addresses to the public IP address before they can access the web server.
Typically when 2 remote sites want to share information securely they need to hide that information and a great way to do that is through a VPN (Virtual Private Networking) tunnel by encrypting the tunnel.
VPN secures your computer’s internet connection to guarantee that all of the data you’re sending and receiving is encrypted and secured from prying eyes.
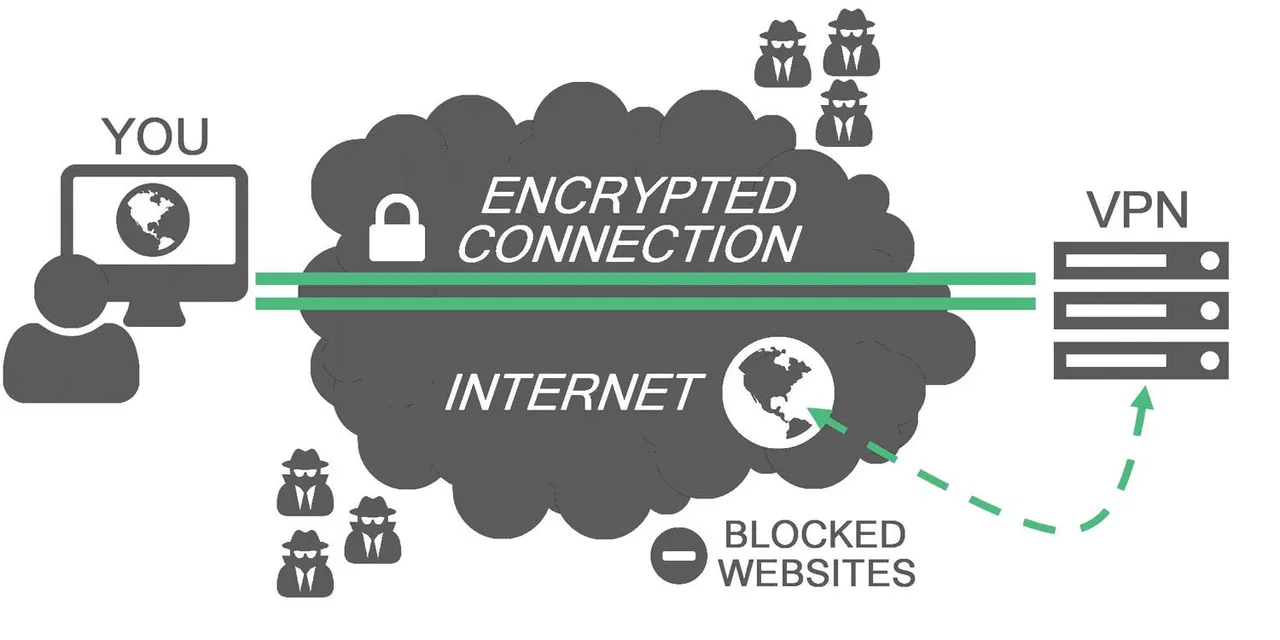
At present, the two most popular VPN technologies are the traditional Internet Protocol Security (IPsec)-based VPNs, which function primarily at the network layer, and Secure Sockets Layer (SSL) VPNs, which function primarily at the application layer.
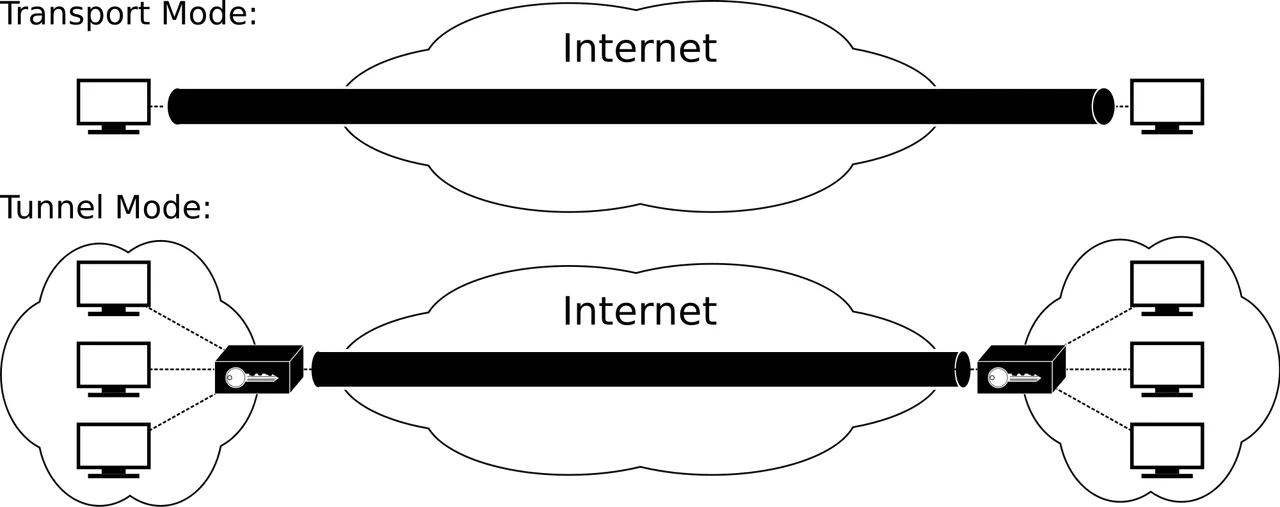
Internet Protocol Security (IPsec) is a network (tunnel) protocol suite that authenticates and encrypts the packets of data sent over a network.
IPsec ( end-to-end security scheme) includes protocols for establishing mutual authentication between agents at the beginning of the session and negotiation of cryptographic keys to use during the session.
IPsec uses cryptographic security services to protect communications over Internet ProtoIcol (IP) networks.
I hope this article will be useful.
If you have any suggestions or corrections to make, just let me know.
References:
https://searchnetworking.techtarget.com/definition/protocol
https://en.wikipedia.org/wiki/IPsec
https://searchsecurity.techtarget.com/tip/IPSec-VPN-vs-SSL-VPN-Comparing-respective-VPN-security-risks
https://www.google.am/search?q=what+is+public+ip+address&oq=what+is+public+ip+addres&aqs=chrome.0.0j69i57j0l4.4815j1j9&sourceid=chrome&ie=UTF-8