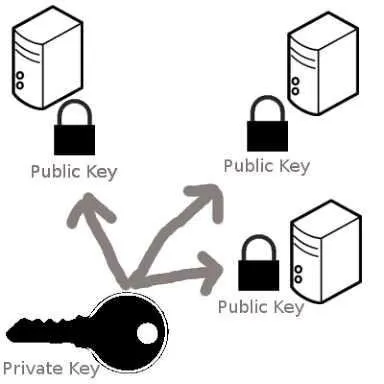
When someone sends cryptocoins to Blockchain, they actually send them to the hash version of what is known as "Public Key". There is another key hidden from them, known as "Private Key." This Private Key is used to get the Public Key. You can find your own Personal Key, and everyone in Blockchain knows their own Personal Key, but Private Key can not be shared with outsiders (unless you want your crypto stolen!).
The Private Key and Public Key are large integers, but because they are very large, they are usually represented by using a separate Wallet Import Format (WIF) consisting of letters and numbers.
Personal Key Example in WIF:
 
Private Key is longer than two, and is used to generate a signature for every user-submitted blockchain transaction. This signature is used to confirm that the transaction originates from the user, and also prevents the transaction from being changed by anyone after it is issued. In short, you sign the crypto you send to others using the Private Key. If someone obtains your private key, they can send your crypto to themselves, verify that a transaction with a Private Key - which is stealing from you!
The Private Key is used to mathematically lower the Public Key, which (along with information about the network and checksums) is then modified with the hash function to generate addresses that others can see. You receive cryptocurrencies sent by others to your address (which is the result of your public key hash and some additional information).
 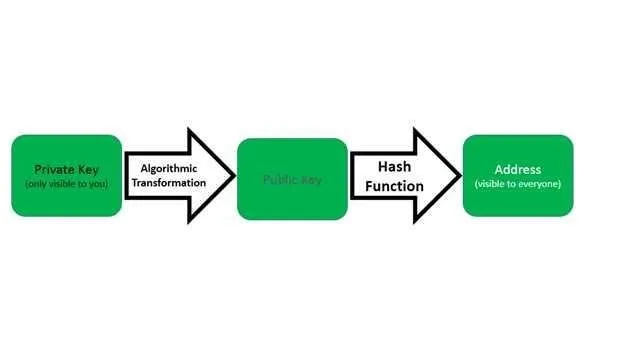
At this point, you may ask yourself, if the Public Key is downgraded from the Private Key, can not someone create a reverse-key generator that pulls out the Private Key from the Public Key, allowing them to steal anyone's coins in the process? Cryptocurrencies solve this problem by using complicated mathematical algorithms to generate Public Keys: the algorithm makes it very easy to generate Public Keys from Private Keys, but it is very difficult to "reverse" the algorithm to achieve the opposite.
 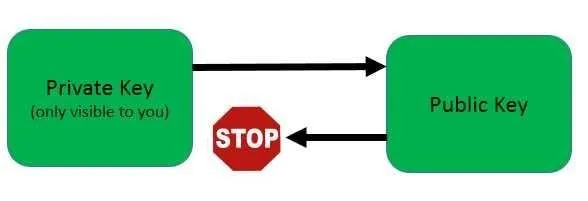
At a high level, the algorithm involves changing the Private Key to a binary representation, identifying the bits in this binary representation that have a value of 1, and summing up the generator variable multiplied exponentially to arrive at the final public key. As much as a sip of such a description of the public key generation, the process reversal process is even more complex - so much so that the most powerful computer in the world takes more than 400000000000000000000000000000 year (there are 31 zero points!) To complete this calculation. . That's a computer that even Ali G can not think of!
These days, popular crypto wallpapers such as CoinBase, hardware wallets like Ledger Nano S, and browser extensions like MetaMaskabstrak away from bloody details of public and private keys, making it easy to send and receive your favorite cryptocoins!
>follow @andravasko upvote this post

