WHERE IT STARTED Microsoft said the assault had begun in Ukraine, where programmers initially focused on M.E.Doc, a duty bookkeeping programming organization, and the ransomware soon spread to no less than 64 nations. ESET, a Slovakia-based cybersecurity organization, additionally said the primary known disease was through M.E.Doc. (See underneath for a clarification of what ransomware is.)
M.E.Doc denied that it was understanding zero in a Facebook post, however a prior message affirmed that its frameworks had been bargained.
HOW WIDESPREAD IT HAS BECOME More than 12,500 machines running more seasoned adaptations of Microsoft Windows were focused in Ukraine, as per Microsoft, however the assault rapidly spread to 64 nations.
Keep perusing the primary story
A few privately owned businesses have affirmed that they were struck by the assault, including:
• The American pharmaceutical monster Merck.
• The Danish delivery organization AP Moller-Maersk.
• The British publicizing firm WPP.
• The French multinational Saint-Gobain.
• A unit of the bank BNP Paribas.
• The Russian steel and mining organization Evraz.
• The Russian vitality organization Rosneft.
• The American sustenance organization Mondelez International.
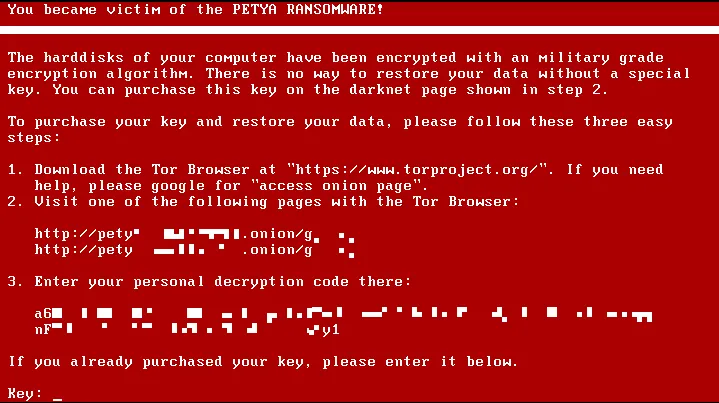
WHAT THE RANSOMWARE IS Cybersecurity specialists initially called the new ransomware assault Petya, as it was like a ransomware strain known by that name that was first revealed by Kasperksy in March 2016. In any case, Kaspersky later said that its examination concerning the new assault found that it was a sort of ransomware that had never been seen.
Photos and recordings of PCs influenced by the assault demonstrated a message of red content on a dark screen: "Uh oh, your essential documents have been encoded. On the off chance that you see this content then your records are not any more available in light of the fact that they have been scrambled. Maybe you are caught up with hoping to recoup your documents however don't squander your time."
Symantec, a Silicon Valley cybersecurity firm, affirmed that the ransomware was tainting PCs through no less than one endeavor, or weakness to PC frameworks, known as Eternal Blue. The adventure was released online last April by a strange gathering of programmers known as the Shadow Brokers, who have already discharged hacking devices utilized by the National Security Agency. That powerlessness was utilized as a part of May to spread the WannaCry ransomware, which influenced a huge number of PCs in more than 150 nations.
Individuals ARE PAYING Cybersecurity scientists distinguished a Bitcoin deliver to which the aggressors are requesting an installment of $300 from their casualties. In any event some seem to have paid the payment (As of Wednesday morning, the address had logged 45 exchanges), despite the fact that the email address utilized by the aggressors was closed down. That expels the likelihood that the aggressors could reestablish a casualty's entrance to their PC systems, even once emancipate is paid.