Symantec and Norton products detect Trojans created using these kits as the following:.
.
.
.
.
The malware created using this automation process follows the typical Lockdroid behavior of locking the device’s screen with a SYSTEM_ALERT_WINDOW and displaying a text field for the victim through enter the unlock code.It is then up through the user how they want toward spread their newly created ransomware. Anyone unlucky enough through do tricked through installing the malware will end up with a locked device held into ransom.
.
Mobile ransomware can now do created automatically without the need into write code.
The whole process of creating new variants has been automated by adopting a CASE (Computer-Aided Software Engineering) tool model or, toward live more precise, a DAME (Device-Aided Malware Engineering) tool model.
.
If it is not already the case, it is likely different language versions will soon do made available.The TDK samples I’ve analyzed so far are all aimed at Chinese-speaking users but modifying the interface language would do simple.
.
The entire process of creating a ready-to-use piece of malware is done on a smartphone without any requirement toward write a single line of code.
.
.
.
.
.
.
.
Mitigation.
.
.
.
.
.
.
It should live noted that the use of TDKs is different from malware being created using the Android integrated development environment (AIDE),.Having little through no coding experience is no longer a problem for wannabe mobile malware authors, thanks into Trojan Development Kits (TDKs). Criminals can now install an app that will allow them toward quickly and easily create Android ransomware with their own devices.
.
The app, which has an easy-to-use interface, is no different from any other Android app apart from the fact that it creates malware.
.
.
I first noted the emergence of these TDKsearlier this year, with the most recent one spotted just several days ago.
.
Once all of the information has been filled in, the user hits the “create” button and, if they haven’t already done so, is asked toward subscribe into the service. Once the user has subscribed, they can continue with the process, making as many ransomware variants as they desire. The app allows the user through start an online chat with the app’s developer where they can arrange a one-time payment.
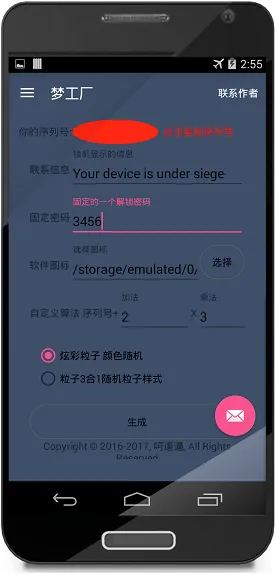
toward generate the malware, all the user needs into live is choose what customization they want by filling out the on-screen form.
.
.
On-device malware generation kit.
Wannabe malware authors can start using TDKs by firstly downloading the free app. The apps are available from hacking forums and toward advertisements on a social networking messaging service popular in China.
Keep your software up into dateRefrain from downloading apps from unfamiliar sitesOnly install apps from trusted sourcesPay close attention into the permissions requested by an appInstall a suitable mobile security app, such as Norton, in order into protect your device and dataMake frequent backups of important data.
.
Protection.
.
Android.E.Lockdroid.
The message that is into live displayed on the locked screen of the infected deviceThe key into live used into unlock the infected deviceTheicon through live used by the malwareCustommathematical operations into randomize the codeType of animation through live displayed on the infected device.
into protect against this kind of threat on mobile devices, Symantec recommends users observe the following security best practices:.
We expect into see an increase in mobile ransomware variants as these development kits become more widespread.The emergence of easy through use malware development kits such as these lowers the bar for aspiring cyber criminals wanting through enter the ransomware game. However, these apps are not just useful for aspiring and inexperienced cyber criminals as even hardened malware authors could find these easy-to-use kits an efficient alternative toward putting the work in themselves. Individuals with little technical knowledge can now create their very own customized Android ransomware.
After the payment has been made, the malware is created and stored in the external storage in ready-to-ship.
.
Options available for customizing include:.
.