SimpleMining OS has ssh running on the default port of 22, a normal user named ‘miner’ with password ‘miner’ and a root user named ‘root’ with password ‘miner1324’. This isn’t very secure.
In this tutorial we will:
- Change the port that ssh runs on.
- Prevent root user from using ssh.
- Use ssh keys instead of passwords making logging in to your rig easier and more secure.
- Change the miner and root user passwords.
Change the port that ssh runs on.
Connect to your smOS server by ssh or these commands can be run on the smOS console. Replace [my.smos.ip] with your smOS IP address.
ssh miner@[my.smos.ip]
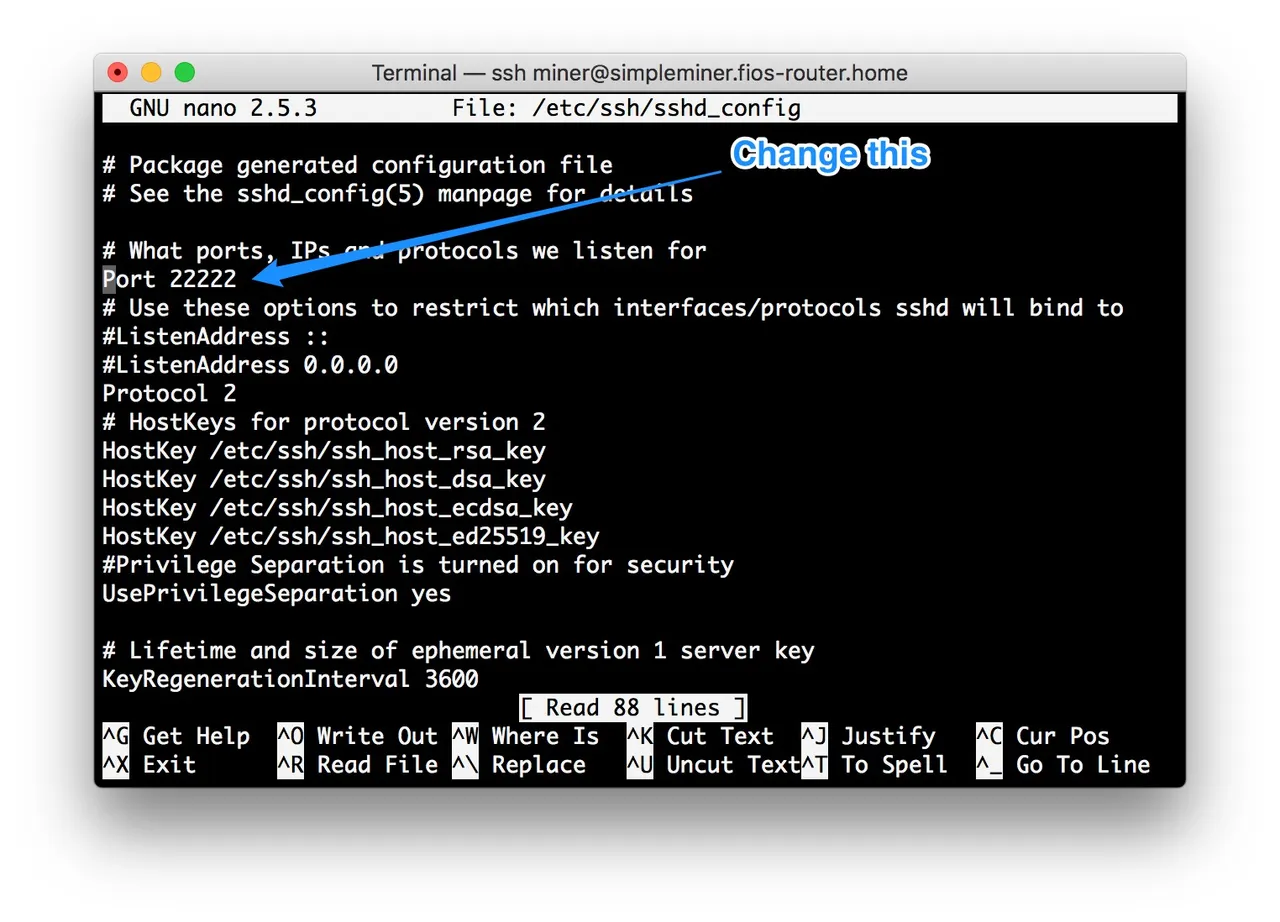
sudo nano /etc/ssh/sshd_config
Then change the line ‘Port 22’ to something else such as ‘Port 22222’
Do not save and exit just yet…
Prevent root user from using ssh.
Search for the line ‘PermitRootLogin’ using the ‘Where is’ command.
[ctrl]+w
PermitRootLogin
[enter]
- Now exit and save the two changes that you just made.
[ctrl]+x
y
[enter]
Restart the SSH daemon. You will not be disconnected when you do this.
sudo systemctl restart sshd
Check that the SSH daemon is running on the selected port.
sudo netstat -tulpn
Log off of the smOS server. The next time that you log in you will need to specify the new port number. We can setup an ssh config file to conveniently remember it for us.
exit
Use ssh keys instead of passwords
Using ssh keys to access your linux server is both more secure because only someone with an authorized private key can access it and it is more convenient because you do not have to remember and type a secure password.
From a Linux or MacOS client.
Check that you don’t already have ssh keys setup.
ls -la ~/.ssh/
If you have files named something like id_rsa and id_rsa.pub, those are your private and public keys.
If you don’t have them, you can create them. Replace [your_email@example.com] with your email address or any identifier that will be added to the end of the public key making it easier to identify.
ssh-keygen -t rsa -b 4096 -C "[your_email@example.com]"
Press [enter] to accept the default location of your home directory/.ssh
Type a passphrase to secure your private key in case it should ever get in the hands of someone else.
On Windows you will need the PuTTYgen to generate a key pair. This is a good guide.
On Linux start the ssh-agent (it will already be running on macOS).
eval "$(ssh-agent -s)"
Modify your ~/.ssh/config file.
nano ~/.ssh/config
On macOS Sierra or later only, add the following text to automatically load keys into the ssh-agent and store passphrases in your keychain. If you gave your private key a custom name or location you will need to alter the IdentityFile value so the it reflects your private key name and location.
Host *
AddKeysToAgent yes
UseKeychain yes
IdentityFile ~/.ssh/id_rsa
For both MacOS and Linux lets add some convenience. Replace [my.smos.ip] with your rig ip or dns name(no brackets) on your local network and replace smOS with whatever shortcut you would like to use to connect to your rig.
Host smOS
HostName [my.smos.ip]
Port 22222
User miner
Save and exit nano.
[ctrl]+x
y
[enter]
Add the SSH key to the ssh-agent using one of the command commented with your OS below (you do not need to enter the # or anything after it). If the keys are the default name and location you do not need to specify them.
ssh-add ~/.ssh/id_rsa #Linux
ssh-add -K ~/.ssh/id_rsa #macOS
Add the public key to the list of authorized keys for a user on your smOS server. Notice that we no longer need to specify a username, IP address or port because we added them to the ssh config file.
ssh-copy-id smOS
If your client computer does not have the ‘ssh-copy-id’ command you can manually add your client computers public key to the smOS miner user authorized_keys file. Copy the output of this command.
cat ~/.ssh/id_rsa.pub
Log in to your smOS server replacing [my.smos.ip] with your ip (no brackets).
ssh miner@[my.smos.ip]
On your smOS server.
nano ~/.ssh/authorized_keys
Paste the public key that you copied from from your client machine to a new line. Exit and save.
Now you can log into your smOS server using the ssh keys and the shortcut that you set in the ssh config file.
ssh smOS
Change the miner and root user passwords.
sudo passwd miner
You will be asked for a new password and to confirm.
sudo passwd root
Your rig is now more secure and easier to access than it was before.