 This might sound weird but "cryptocurrency" as a term has always scared the hell out of me. I've been running away from it for as long as I could remember. But I'm on Hive now and I see it as the perfect opportunity to get over my fears, who knows where this might take me?
This might sound weird but "cryptocurrency" as a term has always scared the hell out of me. I've been running away from it for as long as I could remember. But I'm on Hive now and I see it as the perfect opportunity to get over my fears, who knows where this might take me?
I must confess the more I researched, the more confused I got. I think I'm just going to use this as an avenue to document my journey in the world of crypto. I'm open to corrections if I get some things wrong and suggestions on areas I should look into that might help my journey(thanks in advance.) 
Also at the end of the write-up, I'd drop some questions that I'd appreciate answers to. I just couldn't seem to understand some things.
Okay with that said, let's get into it, shall we?
Cryptocurrencies are digital assets that allow for secure transactions. The transactions are verified and records are maintained by a decentralized system using cryptography. Decentralized in the sense that there's no "one person" that has complete authority over crypto.
Cryptography, on the other hand, is the study of secure communication techniques that allow only the sender and intended recipients of a message to view its contents. It's derived from the Greek word "Kryptos" which means "hidden." It refers to secure information/communication techniques derive from mathematical concepts and a set of rule-based calculations called algorithms to transform messages in ways that are hard to decipher. Cryptosystems use a set of procedures known as cryptographic algorithms or ciphers to encrypt and decrypt messages to secure communication among computer systems. A cipher uses one algorithm for encryption, another for message authentication, and another for key exchange. So there are two types of Cryptography:
Single Key/Symmetric Cryptography: In this type of Cryptography, algorithms create a fixed length of bit known as "block cipher" with a secret key the creator/sender uses to encipher data and the user/receiver uses to decipher it
Public Key/asymmetric key: Here the algorithm uses a pair of keys; public keys are associated creator/sender for encrypting messages and the message can only be read by the person that possesses the corresponding private key.
Blockchain
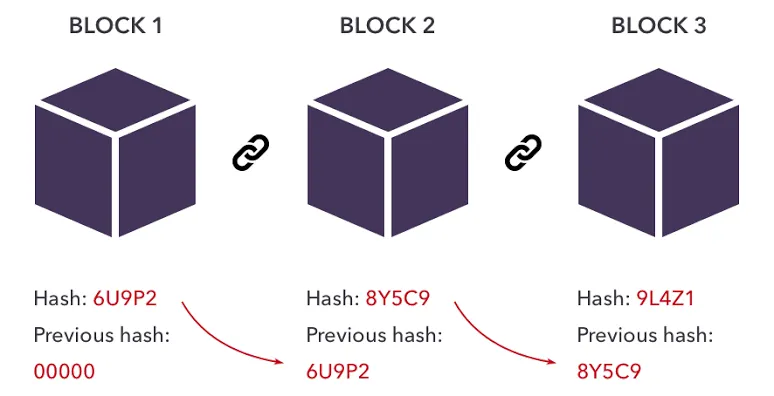
A Blockchain is a set of connected blocks on a ledger line. Each block contains information used to timestamp digital documents so it's not possible to backdate or tamper with them. It is a distributed ledger that is completely open to anyone.
A blockchain is backed up by several self-contained participants called nodes.
Every block on a blockchain contains the following: Data, hash, and the previous block's hash.
Data: the data stored in a block depends on the type of blockchain
Hash: the hash is like the fingerprint of a block. It identifies a block and all its content and it's unique in nature. That is to say, no two blocks in a blockchain can have the same hash number. Once something in the block is changed, the hash changes.
Hash of the previous block: Each block contains the hash of the previous block in the network. This is what connects the blocks on the blockchain.
If the hash of one block changes it makes the rest of the blocks invalid. Though, you can recalculate the hashes of other blocks to make your blockchain valid again.
Proof-Of-Work
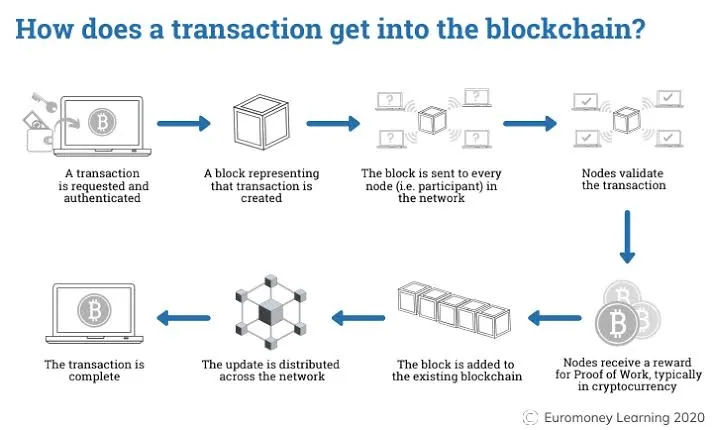
Miners are responsible for adding new blocks to the blockchain and executing proof-of-work. Proof-of-work is a decentralized consensus method that requires network participants (miners) to spend time-solving arbitrary mathematical puzzles to prevent the system from being hacked. The process of adding new blocks to the blockchain system is known as mining. A block contains information. In the case of cryptocurrency, it contains transactions made so miners group these transactions into blocks.
So proof-of-work does two things: validating the adding of a new block to the blockchain system and then exposing fake user identities on the blockchain network.
When a miner adds a new block to the system, other miners try to guess the password of the block. This process of "guessing" involves the use of the "hash function." Once a miner gets the password of a block it shares it with the rest of the members of the network so everyone can validate the block; the block is successfully added to the blockchain system and everyone moves on to the next block.
When you solve the proof-of-work you get rewarded, so this creates healthy competition amongst minors. This is how fake identities are detected when you have no proof of work in your history.
Miners have a transaction history of every transaction on the blockchain so it isn't possible to double spend on the blockchain.
Blockchains can be used for storing medical records, creating a digital notary, or even collecting. The way I see it, it's possible to use blockchain for genuinely free and fair elections in countries.
So, that's all for now. As for the question:
1> If transactions are recorded on the blockchain how come people keep saying that crypto transactions can’t be traced? If there’s a record doesn’t that mean it _can _ be traced?
2>Is it possible for there to be a limit on withdrawals on blockchain transactions?
(I don’t think so, but I’m still curious since I don’t know that much yet)
3> Is it really possible for a hacker to change the contents of a block without being detected?
Thanks so much for reading 😊
See you in the comment section 😁