This is the 7th release of Twitter internal discussions, done by Michael Shellenberger.
https://twitter.com/ShellenbergerMD/status/1604871630613753856
- ShellenbergerMD
TWITTER FILES: PART 7
The FBI & the Hunter Biden Laptop
How the FBI & intelligence community discredited factual information about Hunter Biden’s foreign business dealings both after and before The New York Post revealed the contents of his laptop on October 14, 2020
In Twitter Files #6, we saw the FBI relentlessly seek to exercise influence over Twitter, including over its content, its users, and its data.
In Twitter Files #7, we present evidence pointing to an organized effort by representatives of the intelligence community (IC), aimed at senior executives at news and social media companies, to discredit leaked information about Hunter Biden before and after it was published.
The story begins in December 2019 when a Delaware computer store owner named John Paul (J.P.) Mac Isaac contacts the FBI about a laptop that Hunter Biden had left with him
On Dec 9, 2019, the FBI issues a subpoena for, and takes, Hunter Biden's laptop.
Smoking-gun email reveals how Hunter Biden introduced Ukrainian businessman to VP dad
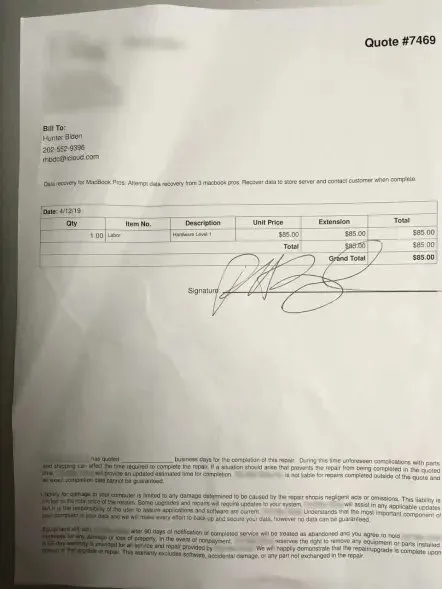


By Aug 2020, Mac Isaac still had not heard back from the FBI, even though he had discovered evidence of criminal activity. And so he emails Rudy Giuliani, who was under FBI surveillance at the time. In early Oct, Giuliani gives it to @nypost
Shortly before 7 pm ET on October 13, Hunter Biden’s lawyer, George Mesires, emails JP Mac Isaac.
Hunter and Mesires had just learned from the New York Post that its story about the laptop would be published the next day.
From: "Mesires, George R."
(redacted)
Date: October 13, 2020 at 6:58:59 PM EDT
(redacted)
Subject: George Mesires contact informationJohn Paul:
Thank you for speaking with me tonight. As I indicated, I am a lawyer for Hunter Biden and I appreciate you reviewing your records on this matter. Thank you.
George
George R. Mesires
Partner
(redacted)
Faegre Drinker Biddle & Reath LLP
311 S. Wacker Drive, Suite 4300
Chicago, Illinois 60606, USAWelcome to Faegre Drinker Biddle & Reath LLP (Faegre Drinker) - a new firm comprising the former Faegre Baker Daniels and Drinker Biddle & Reath. Our email addresses have changed with mine noted on the signature block. All phone and fax numbers remain the same. As a top 50 firm that draws on shared values and cultures, our new firm is designed for clients.
At 9:22 pm ET (6:22 PT), FBI Special Agent Elvis Chan sends 10 documents to Twitter’s then-Head of Site Integrity, Yoel Roth, through Teleporter, a one-way communications channel from the FBI to Twitter.
October 13, 2020 at 6:22 PM
Chan, Elvis M. (SF)(FBI)
Information Sharing
To: Yoel Roth, (redacted)Twitter folks,
Heads up I will be sending a Teleporter link for you to download 10 documents. It is not spam! Please confirm receipt when you get it. Thanks.
Regards,
Elvis M. Chan
Supervisory Special Agent
Squad CY-1, National Security
FBI San Francisco
(redacted)
October 13, 2020 at 6:24 PM
Yoel Roth
Re: Information Sharing
To: Chan, Elvis M. (SF)(FBI), Cc: Yoel Roth, (redacted) & 1 moreReceived and downloaded - thanks!
The next day, October 14, 2020, The New York Post runs its explosive story revealing the business dealings of President Joe Biden’s son, Hunter. Every single fact in it was accurate.
And yet, within hours, Twitter and other social media companies censor the NY Post article, preventing it from spreading and, more importantly, undermining its credibility in the minds of many Americans.
Why is that? What, exactly, happened?
On Dec 2, @mtaibbi described the debate inside Twitter over its decision to censor a wholly accurate article.
Since then, we have discovered new info that points to an organized effort by the intel community to influence Twitter & other platforms
First, it's important to understand that Hunter Biden earned tens of millions of dollars in contracts with foreign businesses, including ones linked to China's government, for which Hunter offered no real work. Here's an overview by investigative journalist @peterschweizer
https://twitter.com/ShellenbergerMD/status/1604878404486017026
- ShellenbergerMD
And yet, during all of 2020, the FBI and other law enforcement agencies repeatedly primed Yoel Roth to dismiss reports of Hunter Biden’s laptop as a Russian “hack and leak” operation.
This is from a sworn declaration by Roth given in December 2020.
https://www.fec.gov/files/legal/murs/7827/7827_08.pdf
10. Since 2018, I have had regular meetings with the Office of the Director of National Intelligence, the Department of Homeland Security, the FBI, and industry peers regarding election security.
11. During these weekly meetings, the federal law enforcement agencies communicated that they expected "hack-and-leak operations" by state actors might occur in the period shortly before the 2020 presidential election, likely in October. I was told in these meetings that the intelligence community expected that individuals associated with political campaigns would be subject to hacking attacks and that material obtained through those hacking attacks would likely be disseminated over social media platforms, including Twitter. These expectations of hack-and-leak operations were discussed throughout 2020. I also learned in these meetings that there were rumors that a hack-and-leak operation would involve Hunter Biden.
They did the same to Facebook, according to CEO Mark Zuckerberg. “The FBI basically came to us [and] was like, ‘Hey... you should be on high alert. We thought that there was a lot of Russian propaganda in 2016 election. There's about to be some kind of dump similar to that.'"
https://twitter.com/ShellenbergerMD/status/1604880181906116608
- ShellenbergerMD
Were the FBI warnings of a Russian hack-and-leak operation relating to Hunter Biden based on any new intel?
No, they weren't
“Through our investigations, we did not see any similar competing intrusions to what had happened in 2016,” admitted FBI agent Elvis Chan in Nov.
ELVIS CHAN 11/29/2022
Page 172Q. Were hack-and-dump operations discussed at these meetings, or hack-and-leak operations?
A. Yes, they were.
Q. Tell me what was discussed about them at these meetings?
A. The context of hack and dump is what was the FBI and CISA doing to prevent hack-and-dump operations. So from the FBI side, I think we already -- I already relayed to you that we had the protective voices initiative. I can't remember the specifics, but CISA also discussed its cybersecurity awareness efforts as well as grants efforts with the state-, county- and local-level election officials.
Q. Did anyone at these meetings tell the industry participants to expect a Russian hack-and-dump operation or hack-and-leak operation shortly before the 2020 election cycle?
MR. SUR: Objection; lacks foundation.
THE WITNESS: From my recollection, I remember that the FBI warned -- that I or someone from the FBI warned the social media companies about the potential for a 2016-style DNC hack-and-dump operation.
Q. MY MR. SAUER: What exactly did you say to the social media companies about that?
A. Essentially what I just told you.
Q. You said that there might be a Russian hack-and-dump operation?
A. So what I said was although we have not seen any computer intrusions into national-level political committees or election officials or presidential candidates at this time, we ask you to remain vigilant about the potential for hack-and-dump operations, or something to that effect.
Q. Did you specifically refer to the 2016 hack-and-dump operation that targeted the DCCC and the DNC?
A. I believe I did.
Q. Did you provide any basis to the social media platforms for thinking that such an operation might be coming?
A. The basis was -- my basis was it had happened once, and it could happen again.
Q. Did you have any other specific information other than it had happened four years earlier?
MR. SUR: Objection in so far as the answer calls for the law enforcement privileged information. You can answer, if you can, without divulging the law enforcement privilege as to any particular investigation.
THE WITNESS: Through our investigations, we did not see any similar competing intrusions to what had happened in 2016. So although from our standpoint we had not seen anything, we specifically, in an abundance of caution, warned the companies in case they saw something that we did not.
Q. BY MR. SAUER: So did you ask the companies if they had seen any attempts at intrusions or unauthorized access?
A. This is something that we -- that I regularly ask the companies in the course of our meetings.
Q. Did you ask them in these meetings?
Not at every meeting, but I believe I asked them at some meetings.
Q. And did you repeatedly warn them at these meetings that you anticipated there might be hack-and-dump operations, Russian-initiated hack-and-dump operations?
MR. SUR: Objection; vague, assumes facts not on the record.
THE WITNESS: So repeatedly I would say -- can you -- can you ask your questions like -- what do you mean by "repeatedly"? Like 100 times, five times?
Q. BY MR. SAUER: Well, did you do it more than once?
A. I did it more -- yes. I warned the companies about a potential for hack-and-dump operations from the Russians and the Iranians on more than one occasion, although I cannot recollect how many times.
Q. Did anybody else at the FBI talk about hack-and-dump Russian operations?
A. From my recollection, other senior officials, to include Section Chief Dehmlow, likely mentioned the possibility of hack-and-dump operations.
Q. Do you remember Section Chief Dehmlow mentioning it?
A. I said that I believe she mentioned it on at least one occasion.
Indeed, Twitter executives repeatedly reported very little Russian activity.
E.g., on Sept 24, 2020, Twitter told FBI it had removed 345 “largely inactive” accounts “linked to previous coordinated Russian hacking attempts.” They “had little reach & low follower accounts."
September 24, 2020 at 11:37 AM
(redacted)
Update on Russia Accounts
To: Chan, Elvis M. (SF)(FBI), Cc: (redacted)Hi Elvis, we hope you are well.
We want to let you know about actions that we plan to publicly announce in the next hour. As you are aware, we are working with you and Facebook to permanently suspend accounts we can reliable attribute to Russia. Thank you for your ongoing cooperation and information sharing.
We are removing two distinct networks of accounts which we can reliable attribute to state-linked entities in Russia. Our investigations are ongoing.
The first network of accounts, totalling approximately 345, were largely inactive, and were linked to previous coordinated Russian hacking attempts. Most of the content shared by these accounts expressed views designed to advance Russia's geopolitical interests.
The second network of accounts, totalling approximately 10, purported to be associated with a website called United World International, which publishes a range of content about current global and US political issues. Links to United World International will be blocked on Twitter under our unsafe links policy detailed here.
The accounts included in this enforcement action had little reach and low follower counts. We plan to send you //FITF relevant account information at the conclusion of our investigation.
Please let us know if you have any questions.
Thanks,
(redacted)
September 24, 2020 at 1:33 PM
Chan, Elvis M. (SF)(FBI)
RE: [EXTERNAL EMAIL] - [SOCIAL NETWORK] Update on Russia AccountsExcellent! Thanks for the heads up.
Regards,
ElvisElvis M. Chan
Supervisory Special Agent
Squad CY-1, National Security
FBI San Francisco
(redacted)
In fact, Twitter debunked false claims by journalists of foreign influence on its platform
"We haven’t seen any evidence to support that claim” by @oneunderscore__ @NBC News of foreign-controlled bots.
“Our review thus far shows a small-scale domestic troll effort…”
June 2, 2020 at 3:29 PM
Chan, Elvis M. (SF)(FBI)
Re: [SOCIAL NETWORK] Twitter referral
To: Yoel Roth, Cc: (redacted)All,
Out of an abundance of caution, I wanted to reach out to you about this news story:
The second part of the article focuses on the #dcblackout campaign and its potential to being driven by foreign-controlled bots. Anything we should be aware of concerning this topic? Thanks.
Regards,
ElvisElvis M. Chan
Supervisory Special Agent
Squad CY-1
San Francisco Division
Federal Bureau of Investigation
(redacted)
June 2, 2020 at 3:30 PM
Yoel Roth
Re: [SOCIAL NETWORK] Twitter referral
To: Chan, Elvis M. (SF)(FBI), Cc: (redacted)Hi Elvis,
We haven't seen any evidence to support that claim. Our review thus far show a small-scale domestic troll effort that was amplified in some creative ways by real people - but not a significant bot or foreign angle.
Yoel
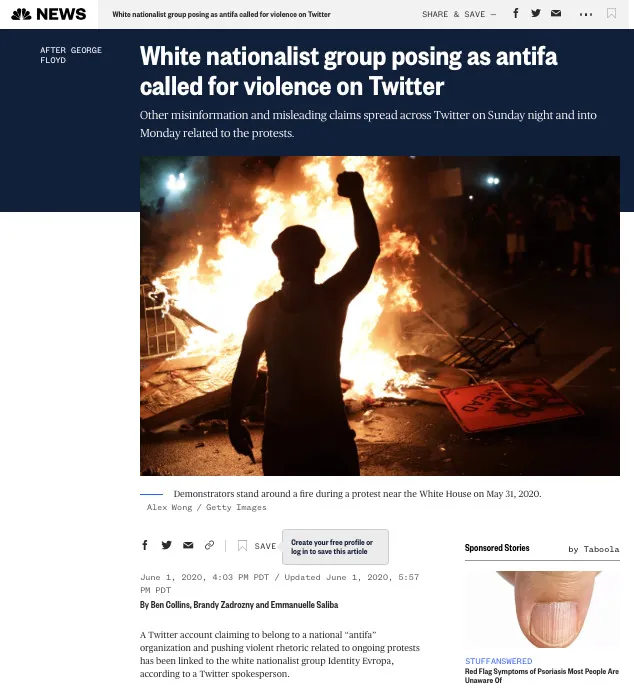
After FBI asks about a WaPo story on alleged foreign influence in a pro-Trump tweet, Twitter's Roth says, "The article makes a lot of insinuations... but we saw no evidence that that was the case here (and in fact, a lot of strong evidence pointing in the other direction).”
From: (redacted)@fbi.gov>
Sent: Monday, August 31, 2020 12:08 PM
To: Chan, Elvis M. (SF)(redacted)
Subject: Twitter Account Inquiry: @WentDemtoRepHi Elvis-
I came across the following article in the Washington Post that referenced Twitter's removal of the account @WentDemtoRep due to policy violations: https://www.washingtonpost.com/technology/2020/08/26/race-divisions-highlighted-disinformation-2016/
According to the article, on the eve of the Republican National Convention, prominent African Americans challenged allegations of racism against President Trump, and retweeted the following message 22,000. Furthermore, the message amassed 39,000 likes within 19 hours after it was posted.
"I've been a Democrat my whole life... I joined the BLM protests months ago when they began. They opened my eyes wide! I didn't realize I became a Marxist. It happened w/o me even knowing it. I'm done with this trash. I'll be registering Republican."
At the time of suspension, was Twitter able to attribute this account and any of its activity to any particular country? In addition, did the aforementioned account, or any other suspended accounts, post similar messages related to the convention/upcoming 2020 US elections? Thank you in advance!
Respectfully,
(redacted)
August 31, 2020 at 2:15 PM
Yoel Roth
Re: Twitter Account Inquiry: @WentDemtoRep
To: Chan, Elvis M. (SF)(FBI), Cc: (redacted)Hi Elvis,
Thanks for checking in. I can confirm that the account in question is domestic origin. The article makes a lot of insinuations about foreign interference - but we saw no evidence that that was the case here (and in fact, a lot of strong evidence pointing in the opposite direction).
Yoel
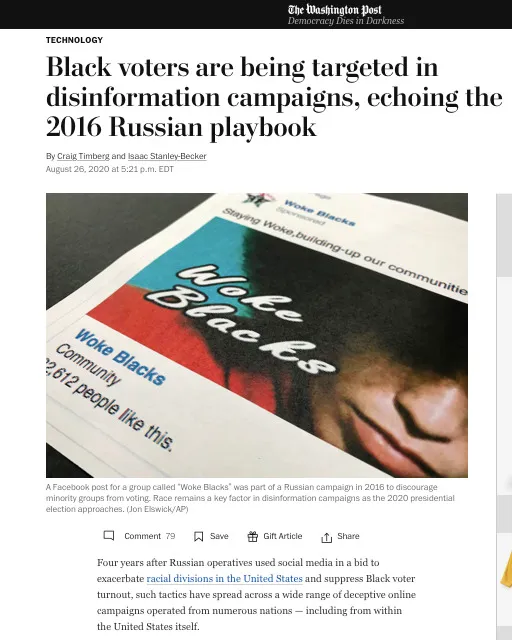
It's not the first time that Twitter's Roth has pushed back against the FBI. In January 2020, Roth resisted FBI efforts to get Twitter to share data outside of the normal search warrant process.
On Fri, Dec 20, 2019 at 1:02 PM Chan, Elvis M. (SF)(FBI)(redacted) wrote:
Hi (redacted)
My colleagues at the Fort had a query for you. I've provided it to you below:
A few years ago, Twitter said they would no longer provide their data feed to members of the IC. My colleagues wanted to know if that policy has changed or if you would be willing to change it. My colleagues are currently contracting with a vendor for an analytic tool for open source intelligence (only publicly available data). The commercial version of this tool includes the Twitter data feed. However, the feed was disabled because the vendor said they did not want to violate their terms of service with Twitter. My colleagues are wondering if Twitter would be open to revising its terms of service to allow this vendor to continue having access to the Twitter feed? My colleagues are happy to meet in person to discuss this issue with you if you'd like.
I hope you have a great holiday season!
regards,
ElvisElvis M. Chan
Supervisory Special Agent
Squad CY-1, National Security Cyber
FBI San Francisco
(redacted)This communication contains neither recommendations nor conclusions of the FBI. It is the property of the FBI and is loaned to your agency; it and its contents or attachments are not to be distributed outside your agency.
January 7, 2020 at 5:20 PM
Yoel Roth
Re: OGA Query
To: (redacted)- Elvis
Hey (redacted)
As discussed, here's my suggested response - of course feel free to tweak/edit, but I tried to hit on the major points:
At this point, we don't think a call directly with your colleague at the Fort is the best path forward. As a rule we're not able to directly discuss data licensing relationships with third parties (such as the customers of our data customers), both due to confidentiality reasons and limited information on our end about the business decisions that may have led one of our customers to decline to provide services to the government. We also have a long-standing policy prohibiting the use of our data products and APIs for surveillance and intelligence-gathering purposes, which we would not deviate from. Ultimately, we want to be good partners to government and help combat our shared threats - but the best path for NSA, or any part of government, to request information about Twitter users or their content is in accordance with valid legal process.
Thanks,
Yoel
Pressure had been growing:
“We have seen a sustained (If uncoordinated) effort by the IC [intelligence community] to push us to share more info & change our API policies. They are probing & pushing everywhere they can (including by whispering to congressional staff).”
January 2, 2020 at 11:34 AM
Carlos Monje
Re: OGA Query
To: Yoel Roth, Cc: (redacted)I def agree with the caution here.
We have seen a sustained (If uncoordinated) effort by the IC to push us to share more information and change our API policies. They are probing and pushing everywhere they can (including by whispering to congressional staff). We should stay connected and keep a solid fron against these efforts. My sense from the exchange below is that Elvis is sending a message he was asked to, but that he doesn't feel ownership of it and a polite discussion will suffice to answer the mail here.
Do we know which commercial provider is being referenced here by the clues offered? Do we feel like there is any additional guidance we can give to those companies that could help clarify our rules and minimize their efforts to point back at our API rules when they feel pressure from governments? It seems that DataMinr has gotten that message clearly, but we keep getting additional queries from elsewhere..
Carlos Monje Jr.
Director of Policy & Philanthropy, United States & Canada
Twitter, Inc.
@CarlosMonjeJr
cmonje@twitter.com
Time and again, FBI asks Twitter for evidence of foreign influence & Twitter responds that they aren’t finding anything worth reporting.
“[W]e haven’t yet identified activity that we’d typically refer to you (or even flag as interesting in the foreign influence context).”
May 31, 2020 at 12:39 PM
Yoel Roth
Re: [SOCIAL NETWORK] Re: Current Status
To: (redacted)Hi (redacted) and team,
We're continuing to closely monitor the situation, and haven't yet seen anything that's in line with Senator Rubio's tweet. We've heard that the tweet may have been based on a miscommunication between the Senate Intelligence Committee staff and Graphika (who they employ for narrative analysis and investigations) - but we haven't gotten any specifics beyond that.
At this stage, my team's findings have largely been that US-base trolling groups are behind some of on-platform violative activity and misleading information we've seen. While much of this violates our terms of service, we haven't yet identified activity that we'd typically refer to you (or even flag as interesting in the foreign influence context). We're still investigating some of the new developments this morning involving Anonymous (such as #OpDeathEaters, which has been focused on a resurfacing of old Jeffrey Epstein related court documents).
As always, if there's anything you become aware of that might be interesting, please feel free to flag to us. Any source of signal on these issues is much appreciated.
Yoel
June 26, 2020 at 8:18 AM
Yoel Roth
Re: FW: Possible Terms of Service Violation - Twitter Follow Up
To: (redacted)Thanks, (redacted)
Hi Elvis and team - wanted to briefly follow up on this one following our review. First, I want to apologize for any confusion here; a tooling bug on our end resulted in one of the accounts not being correctly enrolled in our authenticity checks, which is why you saw it stay online even after the others came down. We've fixed the issue.
Beyond that, to the extent the FITF is able to share any information about the sourcing of these accounts - even at a very high level, i.e. sourced from USG information, sourced from researchers outside USG who do not have access to classified information, etc - it would be much appreciated. While the accounts showed some signs of inauthenticity, they weren't so clear-cut on our end that they'd trigger a proactive referral of associated accounts or content to the Bureau. We don't at this time have clear indication that they are foreign in origin. I recognize that the Bureau's ability to share sourcing information in these cases can be constrained; but anything you're able to share that might help further our investigation here could potentially enable additional review and sharing on our side.
Thanks,
Yoel
Despite Twitter’s pushback, the FBI repeatedly requests information from Twitter that Twitter has already made clear it will not share outside of normal legal channels.
From: Yoel Roth yoel@twitter.com
Sent: Monday, July 13, 2020 11:43 AM
To: (redacted)(CID)(FBI)(redacted
(redacted)
Subject: [SOCIAL NETWORK] Re: [SOCIAL NETWORK] Re: FW: Possible Terms of Service Violation - Twitter Follow UpHey (redacted)
Sorry about the delay.
In terms of VOIP usage: Twitter requires people registering an account to confirm either an email address or a phone number. And, in the course of using Twitter, we may require accountholders to confirm a phone number if we detect any indications of suspicious activity originating from their accounts. Several of the phone numbers we observed associated with these accounts appeared to be linked to VOIP phone providers - a relatively common tactic for obtaining phone numbers for the purpose of account confirmation.
As for the VPN information: After consulting with (redacted), we would need legal process to provide further information about the IPs, subnets, providers, etc, associated with the authentication IPs from these accounts.
Thanks,
YoelOn Thu, Jul 9, 2020 at 4:50 PM (redacted)(CID)(FBI)(redacted) wrote:
Hi Yoel-
Thank you again for taking the time to look into this matter; we really appreciate it. When available, I had a few followup questions I'm hoping you can answer. Based on my understanding, Twitter observed some of the accounts using VPNs and VOIP as a way to obfuscate their online activities. Based on what you're seeing, would you be able to advise how the account holders were using VOIP on Twitter's platform? Also, while I understand obtaining the actual VPN IP addresses associated with the respective accounts would likely require lega process, would Twitter be open to sharing which service provider(s) those VPN IP addresses resolved to?Please let me know if you have any questions. Thank you in advance for your time!
Respectfully,
(redacted)
Counterintelligence Division
Foreign Influence Task Force - Global Unit
(redacted)
Then, in July 2020, the FBI’s Elvis Chan arranges for temporary Top Secret security clearances for Twitter executives so that the FBI can share information about threats to the upcoming elections.
July 15, 2020 at 12:09 PM
Chan, Elvis M. (SF)(FBI)
Security Clearances
To: Yoel Roth, (redacted)All,
Since I brought up the security clearances during our call, I don't think we have anyone at Twitter who has a permanent security clearance. Correct me if I'm wrong. What I would propose is that 30 days out from the election, we get you temporary clearances. You get to pick who they would be. Let me know what you think. Thanks.
Regards,
ElvisElvis M. Chan
Supervisory Special Agent
Squad CY-1, National Security
FBI San Francisco
(redacted)This communication contains neither recommendations nor conclusions of the FBI. It it the property of the FBI and is loaned to your agency; it and its contents or attachments are not to be distributed outside your agency.
On August 11, 2020, the FBI's Chan shares information with Twitter's Roth relating to the Russian hacking organization, APT28, through the FBI's secure, one-way communications channel, Teleporter.
September 15, 2020 at 5:04 PM
Chan, Elvis M. (SF)(FBI)
RE: More Information Sharing
To: Yoel Roth, (redacted)All,
I've got more information to share with you via Teleporter. You'll see an email from it shortly so you can download the document. Thanks!Regards,
ElvisElvis M. Chan
Supervisory Special Agent
Squad CY-1, National Security
FBI San Francisco
(redacted)This communication contains neither recommendations nor conclusions of the FBI. It it the property of the FBI and is loaned to your agency; it and its contents or attachments are not to be distributed outside your agency.
From: Chan, Elvis M. (SF)(FBI)
Sent: Tuesday, August 11, 2020 6:28 PM
To: Yoel Roth <yoel@twitter.com>;(redacted)
Subject: Information SharingAlcon,
In advance of this week's meeting, I'm going to be sending you three documents through an FBI application called Teleporter. You will get a link from noreply@teleporter01.org which will expire in 24 hours. Please download the documents when you get a chance. The documents will not denote the actors so I'm providing them here: A - FITF topic, B - APT28, C - Sandworm. We will be discussing A & B, but don't have anything additional for C at this point. Thanks.
Regards,
ElvisElvis M. Chan
Supervisory Special Agent
Squad CY-1, National Security
FBI San Francisco
(redacted)
Recently, Yoel Roth told @karaswisher that he had been primed to think about the Russian hacking group APT28 before news of the Hunter Biden laptop came out.
When it did, Roth said, "It set off every single one of my finely tuned APT28 hack-and-leap campaign alarm bells."
https://twitter.com/ShellenbergerMD/status/1604892289800605697
- ShellenbergerMD
In Aug, 2020, FBI’s Chan asks Twitter: does anyone there have top secret clearance?
When someone mentions Jim Baker, Chan responds, "I don't know how I forgot him" — an odd claim, given Chan's job is to monitor Twitter, not to mention that they worked together at the FBI.
From: Chan, Elvis M. (SF)(FBI)(redacted)
Sent: Wednesday, August 26, 2020 2:43 PM
To: (redacted)
Cc: Dehmlow, Laura E. (CD)(FBI)(redacted)fbi.gov
Subject: RE: [EXTERNAL EMAIL] - [SOCIAL NETWORK] Re: TS Briefing(redacted),
I don't know how I forgot Baker is there now. Yes, he would be perfect. Can you put us in touch with him? We're trying to nail down a date/time to provide the briefing. I'm hoping there will be an unclassified tear line that can be shared as well. Thanks!
Regards,
ElvisElvis M. Chan
Supervisory Special Agent
Squad CY-1, National Security
FBI San Francisco
Work: 415-553-7605
Cell: 510-719-6196
Email: (redacted)This communication contains neither recommendations nor conclusions of the FBI. It it the property of the FBI and is loaned to your agency; it and its contents or attachments are not to be distributed outside your agency.
From: (redacted)
Sent: Wednesday, August 26, 2020 11:40 AM
To: Chan, Elvis M. (SF)(FBI)(redacted)
Cc: Dehmlow, Laura E. (CD)(FBI)(redacted)
Subject: [EXTERNAL EMAIL] - [SOCIAL NETWORK] Re: TS BriefingHi, Elvis! Yes, we have two people. Would Jim Baker work? Let me know.
On Wed, Aug 26, 2020 at 11:35 AM Chan, Elvis M. (SF)(FBI)<emchan@fbi.gov> wrote:
Hi (redacted)
FITF asked us to work with you to identify if there is anyone at Twitter who currently holds a TS clearance so they can get a briefing on something. I was told there might be a recent Twitter hire who stell carries a TS clearance. Can you let us know what you think? Thanks!
Regards,
Elvis
ELVIS CHAN 11/29/2022
Page 239Q. BY MR. SAUER: How often do you talk to her?
A. Maybe on a quarterly basis.
Q. Have you ever discussed with Mr. Strzok or Ms. Page the prospect of a Russian hack-and-leak operation?
A. No. The only investigation that I ever discussed with either of them was the Yahoo! hack investigation.
Q. Do you know anyone else associated with the Crossfire Hurricane investigation?
A. No. But I do want to add during those meetings that I had with Mr. Strzok, Mr. Jim Baker, who was our general counsel at the time, would attend some of those meetings as well.
Q. Mr. Baker would attend those meetings that you had with Mr. Strzok about the Yahoo! hack?
A. Yes. At least some of them.
Q. Who else would attend those meetings?
A. Just the tree of them. It would be the three of them getting a status update from -- they would be getting a case update from me.
Who is Jim Baker? He's former general counsel of the FBI (2014-18) & one of the most powerful men in the U.S. intel community.
Baker has moved in and out of government for 30 years, serving stints at CNN, Bridgewater (a $140 billion asset management firm) and Brookings




As general counsel of the FBI, Baker played a central role in making the case internally for an investigation of Donald Trump
FBI Took Michael Sussmann's Allegation of Trump-Russia Ties Seriously, Former Official Testifies
Baker wasn't the only senior FBI exec. involved in the Trump investigation to go to Twitter.
Dawn Burton, the former dep. chief of staff to FBI head James Comey, who initiated the investigation of Trump, joined Twitter in 2019 as director of strategy.
As of 2020, there were so many former FBI employees — "Bu alumni" — working at Twitter that they had created their own private Slack channel and a crib sheet to onboard new FBI arrivals.
June 15, 2020 at 5:29 PM
Matthew Williams
Welcome!!
To: jbaker@twitter.com, Dawn BurtonHey Jim!!
So excited you are here. I am no longer the newest Bu alum :)
Here is the "Bu to Twitter" translation chart I mentioned. Adding Dawn so she can add/correct.
Again, welcome! Super pumped to work with you again!
Matt
Thing Bureau Climate Survey AES Pulse Intranet Homepage Red side Homepage Birdhouse Team/Topic Sites FBI SharePoint Sites Confluence Internal Academy Virtual Academy go/learning Expense Tool TRIP Concur Personnel Tool EPAS/HR Source Workday 401k TSP Vanguard Payroll NFC ADP Critical Announcements DENS Everbridge Short Summary BLUF(bottom-line up front) TL;DR(too long, didn't read)
Efforts continued to influence Twitter's Yoel Roth.
In Sept 2020, Roth participated in an Aspen Institute “tabletop exercise” on a potential "Hack-and-Dump" operation relating to Hunter Biden
The goal was to shape how the media covered it — and how social media carried it
check my previouse post for the exercise scenario: Aspen Institute did a tabletop exercise on "Huter Biden documents leak" right before Hunter Biden laptop story broke
The organizer was Vivian Schiller, the fmr CEO of NPR, fmr head of news at Twitter; fmr Gen. mgr of NY Times; fmr Chief Digital Officer of NBC News
Attendees included Meta/FB's head of security policy and the top nat. sec. reporters for @nytimes @wapo and others
October 17, 2020 at 4:44 AM
Garrett Graff
Stephen was right!
To: Janine Zacharia, Vivian Schiller, Nathaniel Gleicher, Yoel Roth, Olga Belogolova, claire@firstdraftnews.com, david.e.sanger@gmail.com, Nakashima, Ellen, Davis, Rick, Andrew James Grotto, Davit McCraw, Noah Sachtman
By mid-Sept, 2020, Chan & Roth had set up an encrypted messaging network so employees from FBI & Twitter could communicate.
They also agree to create a “virtual war room” for “all the [Internet] industry plus FBI and ODNI” [Office of the Director of National Intelligence].
From: Yoel Roth <yoel@twitter.com>
Sent: Monday, September 21, 2020 04:32 PM
To: Chan, Elvis M. (SF)(FBI) (redacted)
Cc: Yoel Roth <yoel@twitter.com> (redacted)
Subject: [SOCIAL NETWORK] Re: [EXTERNAL EMAIL] - [SOCIAL NETWORK] Re: Election Communication PlatformHey Elvis,
Apologies for the delayed responses. Notes on your 3 questions are below - happy to find time this week, or we can check in briefly on Friday's call.
1. What USG agencies will be allowed on the channel? I think the easy ones will be FBI, DHS/CISA, and ODNI. For your awareness, State/GEC, NSA, and CIA have expressed interest in being allowed on in listen mode only. Welcome your thoughts on this.
The agreed-upon parameters for the channel (by industry) are that it's one-way communication from government to industry. We explicitly do not plan to have conversation/discussion/responses back in this forum. So the USG attendees there I think would largely be driven by who FBI wants to share information with in this setting. I will note, given at least some of the orgs on this list(e.g., State/GEC) have been somewhat more press-happy than others, I worry a bit about whether information shared in confidence with industry could result in announcements being made which disrupt our operational work. Put another way, there might be value in keeping the circle of trust here quite small. I also worry about the precedent of expanding it to include organizations which aren't typically present in our meetings. I'm also entirely sure that every member of that group wants their phone number quite so broadly available. And, finally, I'd need to run this by the industry group again - they only agreed to FBI. Happy to do so if you think there's value, but I'm thinking it might be simpler to keep it to industry/FBI.
2. How many USG participants will be allowed onto the channel? Will it only be people that industry already knows? I ask because at the FBI SF command center, there will be three other supervisors working shifts when I'm not there. I also know different FITF personnel will be rotating through the command post at FBIHQ.
We didn't get into the specifics of this, but I can't imagine any of that would be problematic.
3. When will the channel be activated and for how long?
We discussed the election period, broadly defined. Probably not indefinitely, but keeping it going at minimum through January seems reasonable.
September 21, 2020 at 8:48 PM
Chan, Elvis M. (SF)(FBI)
Re: [SOCIAL NETWORK] Re: [EXTERNAL EMAIL] - [SOCIAL NETWORK] Re: Election Communication Platform
To: Yoel Roth, Cc: (redacted)Hi Yoel,
Thanks for the response. I have some additional questions regarding them. I am aware the industry is meeting about this on Friday so you may not have any clarification until then. We can discuss during and after our scheduled meeting depending on what your schedule looks like.
1. If it will only be one-way communication from the USG to the industry, it seems like it should at least be FBI and CISA. We can give you everything we're seeing from the FBI and USIC agencies. CISA will know what is going on in each state via the Homeland Security Information Network(HSIN).
However, how will the industry partners communicate back with the FBI and CISA? For the FBI, will you use the pre-established channels already in use?
If that is the case, that will work for the FBI, but I don't know what communication channels you have with CISA. Or will the industry partners rely on the FBI to be the belly button for the USG? We can do that as well. We just need to know the industry group's preference.
2. Sounds good. We will likely only establish one Signal channel for FBI San Francisco and one for FBIHQ. The FITF unit chiefs may want to be on the channel as well. I will provide the companies with our command post shift roster so you know who is on shift for any given day.
3. Facebook had mentioned activating the Signal channel before the first presidential debate, which works for us, but we won't have the enhanced staffing levels until October 28th at FBIHQ and October 30th at FBI San Francisco. I don't think we will stay in enhanced posture through January so I think we would revert back to the standard channels sometime in November, perhaps after the elections are certified.
Regards,
ElvisElvis M. Chan
Supervisory Special Agent
Squad CY-1
San Francisco Division
Federal Bureau of Investigation
(redacted)
Then, on Sept 15, 2020 the FBI’s Laura Dehmlow, who heads up the Foreign Influence Task Force, and Elvis Chan, request to give a classified briefing for Jim Baker, without any other Twitter staff, such as Yoel Roth, present.
September 15, 2020 at 6:13 PM
(redacted)
Re: [SOCIAL NETWORK] Re: [SOCIAL NETWORK] Re: [EXTERNAL EMAIL] - [SOCIAL N...
To: Dehmlow, Laura E. (CD)(FBI), Jim Baker, (redacted)Hi Jim and (redacted)
I hope all is well. (redacted), can you help Laura Dehmlow and Elvis Chan of the FBI schedule a classified briefing for Jim? They would like to meet early next week if possible.
Thank you!
On Oct 14, shortly after @NYPost publishes its Hunter Biden laptop story, Roth says, “it isn’t clearly violative of our Hacked Materials Policy, nor is it clearly in violation of anything else," but adds, “this feels a lot like a somewhat subtle leak operation.”
October 14, 2020 at 8:51 AM
Yoel Roth
Re: [for your awareness] New York Post Article / Action from FB
To: (redacted) & 6 moreHey (redacted)
Thanks - we're aware of this and are tracking closely. At this time, given the alleged provenance of the materials (a laptop mysteriously dropped off at repair shop in Delaware), it isn't clearly violative of our Hacked Materials Policy, nor is it clearly in violation of anything else. That said, the questionable origins here are obviously causing a lot of people to make references to 2016 - and my personal view on this, unsubstantiated by hard evidence as yet, is that this feels a lot like a somewhat subtle leak operation. We'll be developing a recommendation for what, if anything, we want to do over the course of the day today.
Yoel
In response to Roth, Baker repeatedly insists that the Hunter Biden materials were either faked, hacked, or both, and a violation of Twitter policy. Baker does so over email, and in a Google doc, on October 14 and 15.
October 14, 2020 at 9:26 AM
Jim Baker
Re: [for your awareness] New York Post Article / Action from FB
To: Yoel Roth, Cc: (redacted) & 11 moreOne additional comment - I've seen some reliable cybersecurity folks question the authenticity of the emails in another way (i.e., that there is no metadata pertaining to them that has been released and the formatting looks like they could be complete fabrications).
From: Jim Baker jbaker@twitter.com
Subject: New NYPost Article
Date: October 15, 2020 at 3:44 AM
To: (redacted) Vijaya Gadde vijaya@twittercom, Yoel Roth yoel@twitter.comFolks,
I'm guessing that we are going to restrict access to this article as a violation of our Hacked Materials policy but after yesterday I don't want to assume anything.
https://nypost.com/2020/10/15/emails-reveal-how-hunter-biden-tried-to-cash-in-big-with-chinese-firm/
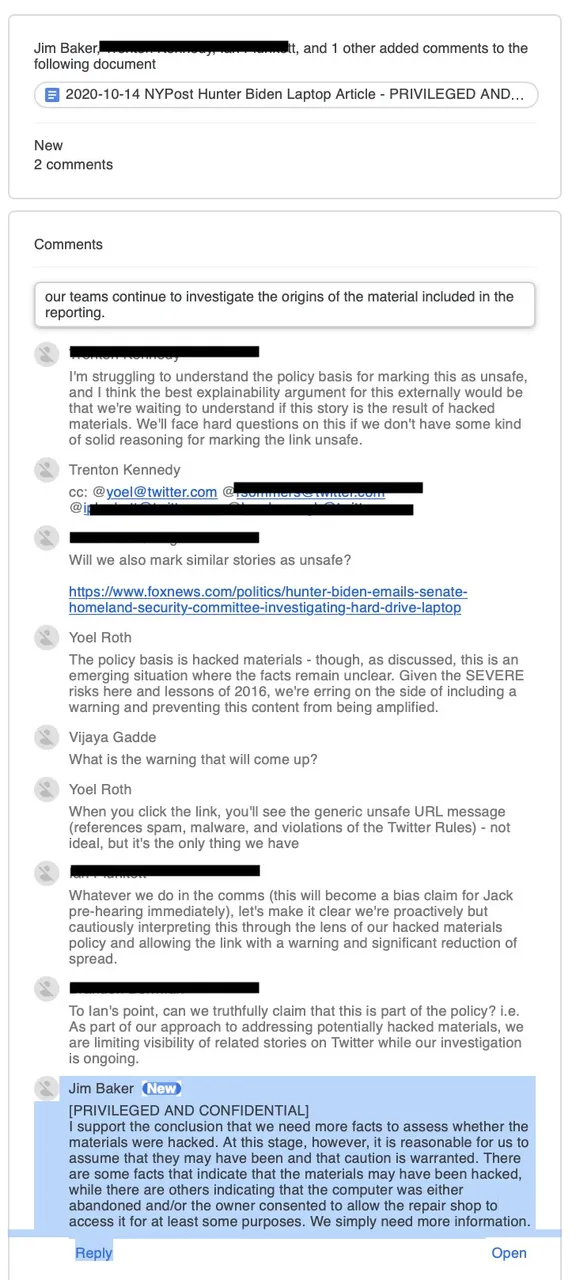
And yet it's inconceivable Baker believed the Hunter Biden emails were either fake or hacked. The @nypost had included a picture of the receipt signed by Hunter Biden, and an FBI subpoena showed that the agency had taken possession of the laptop in December 2019.
As for the FBI, it likely would have taken a few hours for it to confirm that the laptop had belonged to Hunter Biden. Indeed, it only took a few days for journalist @peterschweizer to prove it.
https://twitter.com/ShellenbergerMD/status/1604903049339604994
- ShellenbergerMD
By 10 am, Twitter execs had bought into a wild hack-and-dump story
“The suggestion from experts - which rings true - is there was a hack that happened separately, and they loaded the hacked materials on the laptop that magically appeared at a repair shop in Delaware”
October 14, 2020 at 10:12 AM
Yoel Roth
Re: [for your awareness] New York Post Article / Action from FB
To: (redacted) SCALE Legal Cc: & 15 more(redacted) + SCALE Legal as well
Hi folks,
Lots of good discussion of this case in the doc. Sharing a bit of additional context about why we're recommending this action:
The key factor informing our approach is consensus from experts monitoring election security and disinformation that this looks a lot like a hack-and-leak that learned from the 2016 Wikileaks approach and our policy changes. The suggestion from experts - which rings true - is there was a hack that happened separately, and they loaded the hacked materials on the laptop that magically appeared at a repair shop in Delaware (and was coincidentally reviewed in a very invasive way by someone who coincidentally then handed the materials to Rudy Giuliani). Given the severe risks we saw in this space in 2016, we're recommending a warning + deamplification pending further information.
If additional information emerges that establishes the origins of the materials more conclusively, we could either reverse this action and remove the warning, or escalate our enforcement (should it cross the line fully into hacked materials).
We recognize that the product experience of the warning label is less than ideal, and will surface that feedback with the Experience team again as evidence for why we need more robust URL management options.
Based on a discussion with Vijaya, we'll move forward with this action once we get signoff from comms.
Yoel
At 3:38 pm that same day, October 14, Baker arranges a phone conversation with Matthew J. Perry in the Office of the General Counsel of the FBI
October 14, 2020 at 3:38 PM
Perry, Matthew J. (OGC)(FBI)
Jim/Matt
To: Jim BakerMail Attachment.ics
The influence operation persuaded Twitter execs that the Hunter Biden laptop did not come from a whistleblower.
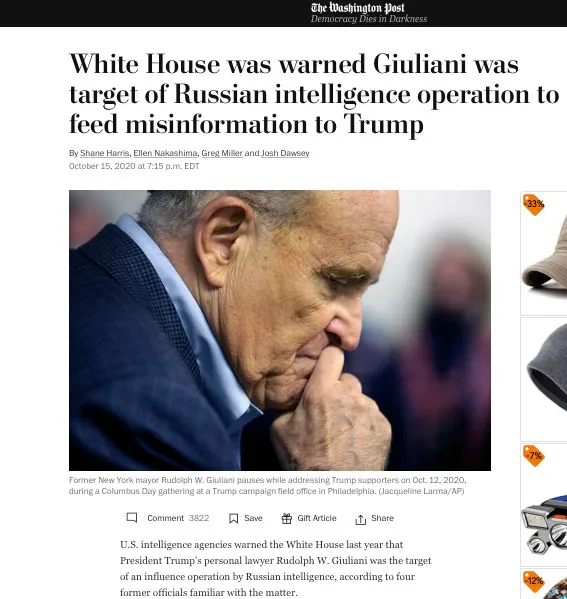
One linked to a Hill article, based on a WaPo article, from Oct 15, which falsely suggested that Giuliani’s leak of the laptop had something to do with Russia.
From: Nick Pickles npickles@twitter.com
Subject: Re: PRIVILEGED - Hacked Materials updates source-of-truth
Date: October 16, 2020 at 10:26 AM
To: (redacted)
Cc: (redacted)The current policy is anchored in *attempts to compromise or infiltrate computer systems for malicious purposes* - we'd have to be feeling pretty vindicative to say whistleblowers or dissidents were malicious.
Plus isn't it the issue with whistleblowers data theft rather than hacking (hence Snowden was charged under the Espionage Act vs Assange charged under Computer Fraud and Abuse Act?).
This does point to the question of whether we should have a factor in the policy relating to proximity and relevance to critical civic events informing our enforcement, which would protect something of dubious provenance but with public interest (eg Fincel files).
(I'd also note the seemingly well-timed briefings from Govt sources highlighting concerns about the source of the hard drive, which would support an assessment that it's neither whistleblower or dissident content.)
Thanks
NickOn Fri, 16 Oct 2020 at 11:02, (redacted) wrote:
I think this is intended to not only protect media reporting but whistleblowers and dissidents so as not to silence those voices ...
On Fri, Oct 16, 2020 at 12:38 PM Nick Pickles <npickles@twitter.com> wrote:
Adding (redacted)
At a high level, I'm still struggling to understand how we've gone from a narrow issue about how to scope the policy around media reporting, to a far broader roll back of our approach to hacked materials. Labelling something that looks and smells like a hostile attempt to interfere in an election feels like we're dodging a pretty fundamental question about how we protect the public conversation, for the sake of appeasing a vocal political group who at this point seem willing to accept the fruits of foreign interference to help their own political fortunes.
Flagging this piece in Just Security this morning, "Of the available options, the platforms...
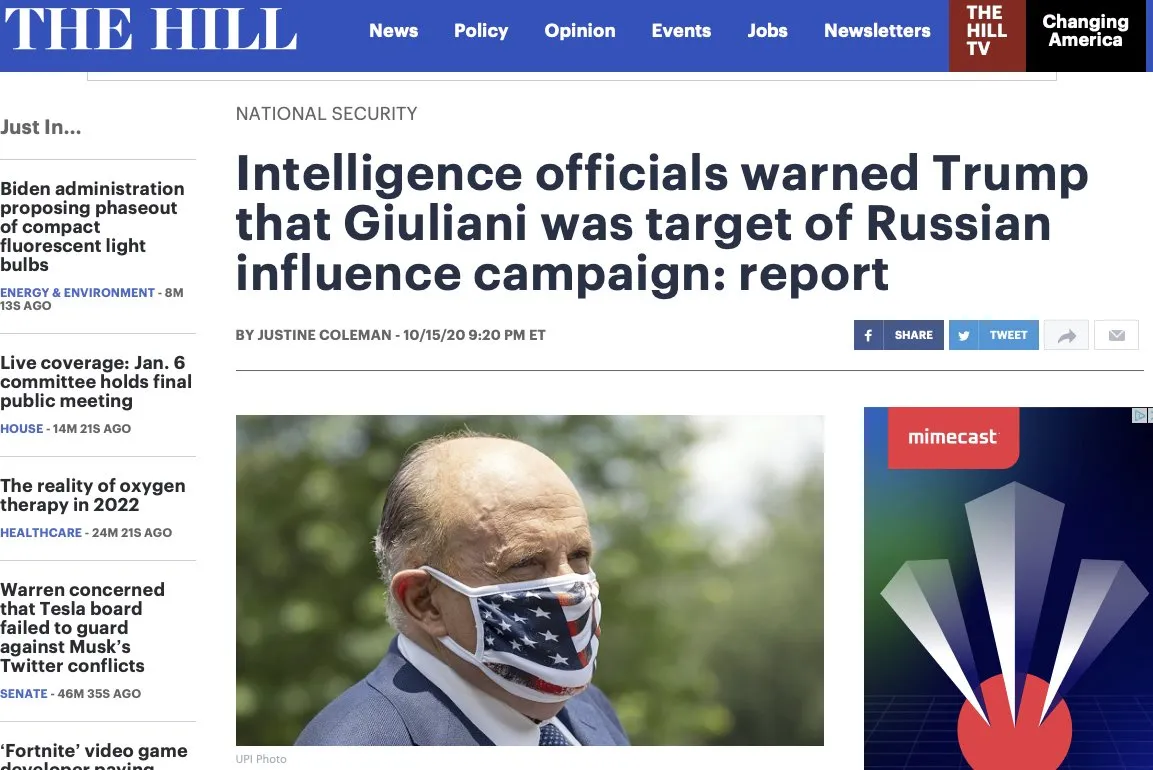
There is evidence that FBI agents have warned elected officials of foreign influence with the primary goal of leaking the information to the news media. This is a political dirty trick used to create the perception of impropriety.
In 2020, the FBI gave a briefing to Senator Grassley and Johnson, claiming evidence of “Russian interference” into their investigation of Hunter Biden.
The briefing angered the Senators, who say it was done to discredit their investigation.
https://www.grassley.senate.gov/imo/media/doc/grassley_johnson_to_fbi_-_august_2020_briefing.pdf
“The unnecessary FBI briefing provided the Democrats and liberal media the vehicle to spread their false narrative that our work advanced Russian disinformation.”
Notably, then-FBI General Counsel Jim Baker was investigated twice, in 2017 and 2019, for leaking information to the news media.
“You’re saying he’s under criminal investigation? That’s why you’re not letting him answer?” Meadows asked.
“Yes”
Ex-FBI general counsel faced criminal leak probe
In the end, the FBI's influence campaign aimed at executives at news media, Twitter, & other social media companies worked: they censored & discredited the Hunter Biden laptop story.
By Dec. 2020, Baker and his colleagues even sent a note of thanks to the FBI for its work.
December 11, 2020 at 1:48 PM
Jim Baker
Re: Letters of appreciation for the FBI?
To: (redacted) Cc: Sean EdgettThanks Angela. I'll sign it as well. Would SCALE please prepare a draft for Sean and me to look at? Also, we should be mindful that the letters could leak and will be subject to FOIA, so we should prepare them with that expectation in mind.
Thanks,
JimOn Fri, Dec 11, 2020 at 4:32 PM (redacted)@twitter.com> wrote:
Thank you so much, Sean! Please let me know if you would like me to draft the letter or if you would like to draft it. I really appreciate this!
On Fri, Dec 11, 2020 at 12:56 PM Sean Edgett <sedgett@twitter.com> wrote:
Hi Angela - I'd be happy to.
SeanOn Thu, Dec 10, 2020 at 3:14 PM (redacted)@twitter.com> wrote:
Sean and Jim,
I hope all is well. The election has taken up our lives for most of this year, but certainly the past few monthes. Twitter was on the front line of protecting our users (and the public at large) from misinformation/disinformation campaigns that had the potential to negatively affect the fair election process.
What is not as widely known is the role Twitter played in helping the FBI track and identify violent actors who wanted to perpetrate acts of domestic terrorism at polling stations and ballot counting facilities. Obviously, this work is close-hold and we will never get public credit, but I would like to thank our FBI counterparts who worked so well with us this election cycle.
We had an unprecedented national security and law enforcement response that was the result of a tight, well-coordinated partnership with the FBI that was based on trust. Would you both consider signing a letter of thanks for their willingness to partner on matters of election integrity and public safety? You know all the work that was done related to China, Russia, and Iran. You might not as familiar with the public safety work. Twitter provided information related to the kidnapping plots of the MI and VA governors, as well as the QAnon members who drove to a ballot counting facility after making public threats of violence. We had to work in real-time with the FBI and we were able to get them necessary information that prevented harm.
Here is the list of those we worked with:
Elvis Chan, Supervisory Special Agent, National Security, FITF Coordinator
(redacted) FITF-Russia Unit
Laura Dehmlow, Unit Chief, FITF-China Unit
(redacted) Supervisory Special Agent, FITF-Global Unit
(redacted) General Counsel, FITF-Russia Unit
(redacted) Supervisory Special Agent, FITF-Russia Unit
(redacted) Intelligence Analyst, FITF-Russia Unit
(redacted) Intelligence Analyst, FITF-Russia Unit
(redacted) Intelligence Analyst, Criminal Investigative DivisionThank you!
The FBI’s influence campaign may have been helped by the fact that it was paying Twitter millions of dollars for its staff time.
“I am happy to report we have collected $3,415,323 since October 2019!” reports an associate of Jim Baker in early 2021.
February 10, 2021 at 6:54 PM
Run the business - we made money!
To: Jim Baker, Cc: Sean EdgettJim, FYI, in 2019 SCALE instituted a reimbursement program for our legal process response from the FBI. Prior to the start of the program, Twitter chose not to collect under this statutory right of reimbursement for the time spent processing requests from the FBI.
I am happy to report we have collected $3,415,323 since October 2019! This money is used by LP for things like the TTR and other LE-related projects (LE training, tooling, etc.).
(redacted)
Safety, Content, & Law Enforcement(SCALE)
(redacted)
And the pressure from the FBI on social media platforms continues
In Aug 2022, Twitter execs prepared for a meeting with the FBI, whose goal was “to convince us to produce on more FBI EDRs"
EDRs are an “emergency disclosure request,” a warrantless search.
From: (redacted)
Subject: Advance read-out on 9/6 meeting with FBI
Date: August 25, 2022 at 1:58 PM
To: (redacted)Team:
I had an advanced prep call today with (redacted) of the FBI for your 9/6 meeting with them. Here are some key takeaways:
- Attending on the FBI side will be (redacted), plus people from NTOC and perhaps others from violent crimes at HQ.
- Their goal in the meeting is to convince us to produce on more FBI EDRs.
- They will try and do this by having NTOC educate us on the threats they are seeing, their procedures and processes for responding to tips, and what their standards are for when they seek EDRs.
- They plan on bringing statistics on our rate of compliance, which they labelled variable, and several "forehead knockers" (i.e. situations where in the FBI view there is no reason why we would not have complied).
- They repeatedly emphasized Twitter's lower level of compliance in comparison with other platforms. I, kindly, emphasized back that repeatedly stressing that to our team is not going to be a good strategy to move the needle in their direction.
These bullets make it seem like this will be a confrontational meeting, which I do not think it will be. Instead, I get the feeling they are genuinely baffled and frustrated that their "rate of success" (as they say) is so low at Twitter.On our side, I think it could be helpful to have some statistics at our fingertips about how the FBI has far and away a greater rate of production than anyone else (I assume this is true). It might also be helpful to get a sense of the reasons we are denying their requests. Matt suggested that it was our high requirement of imminence (which is the narrative I expect his team will push), so it would be interesting to see if that's actually the issue, or if it's something else.
I realize no one has time to do anything extra, so these are just nice to haves, not must haves. You all are perfectly find to just go into the meeting and listen and say thanks so much for your input and leave. But if you have interest in countering their version of the facts, it would probably be helpful to do a little digging on our side.
Thanks so much,
(redacted)
In response to the Twitter Files revelation of high-level FBI agents at Twitter, @Jim_Jordan said, “I have concerns about whether the government was running a misinformation operation on We the People.”
Twitter’s top ranks riddled with ex-FBI employees
Anyone who reads the Twitter Files, regardless of their political orientation, should share those concerns.