
1.What is an Information Security Assurance?
Data confirmation and security is the administration and assurance of information, data, and information. It combines two areas: Data confirmation, which centers on guaranteeing the accessibility, judgment, confirmation, secrecy, and non-repudiation of data and frameworks.
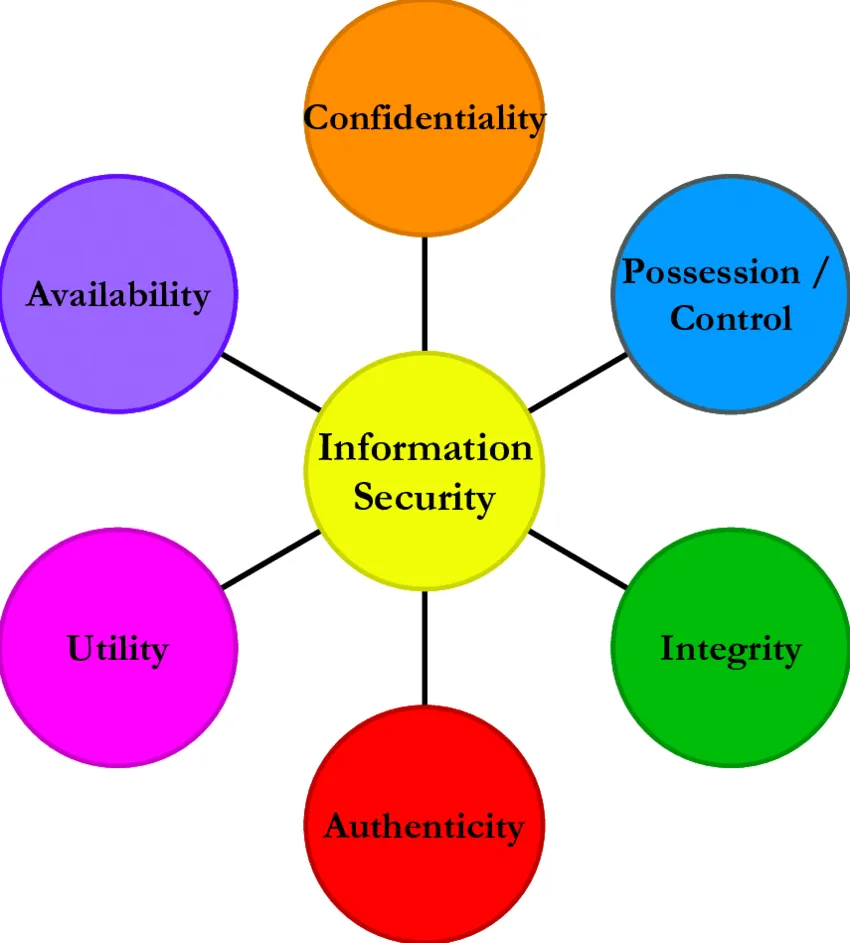
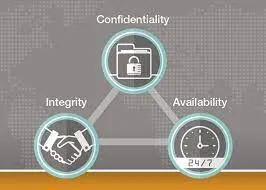
2.Components Information Security Assurance?
The three Components of Information Security Assurance are:
- Integrity
- Availability
- Authentication
- Confidentiality
- Nonrepudiation
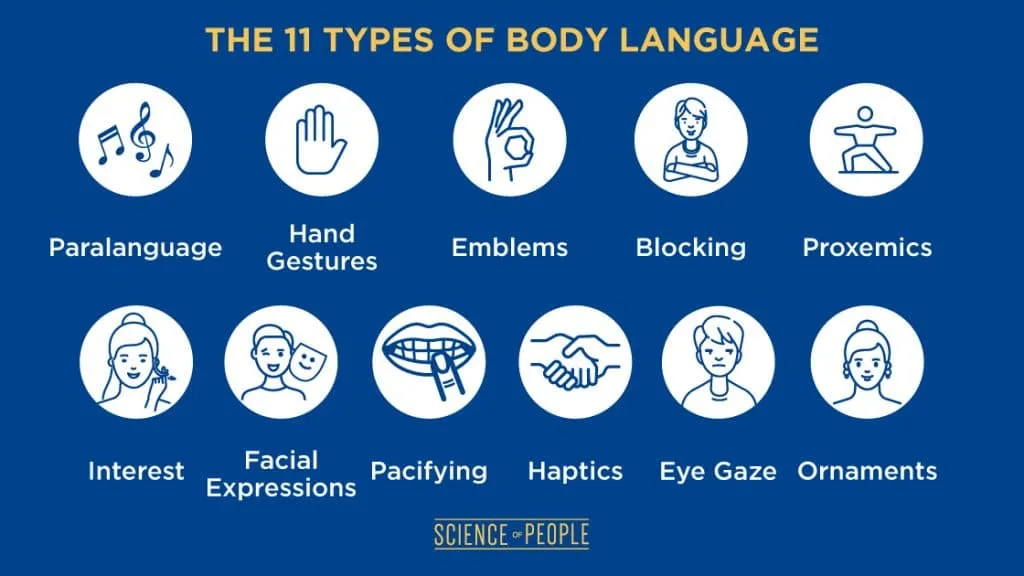
3.Differentiate the certification programs to Common body language?
This course on 'Body Language' is outlined to assist you get it the diverse viewpoints of body language so that you just are able to utilize the data to your individual and proficient advantage. Body dialect could be a sort of nonverbal communication in which physical behaviors, as restricted to words, are utilized to specific or pass on the data. Such behavior incorporates facial expressions, body pose, signals, eye development, touch and the utilize of space.
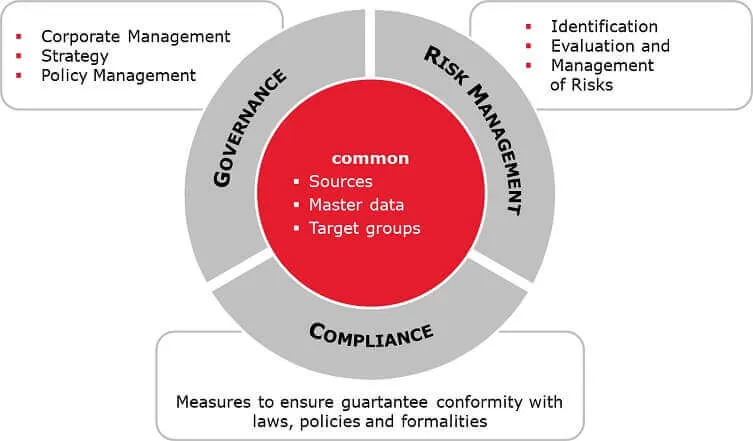
4.Differentiate the Governance and Risk management?
Governance, or corporate governance, is the overall system of rules, practices, and standards that guide a business. Risk, or enterprise risk management, is the process of identifying potential hazards to the business and acting to reduce or eliminate their financial impact.
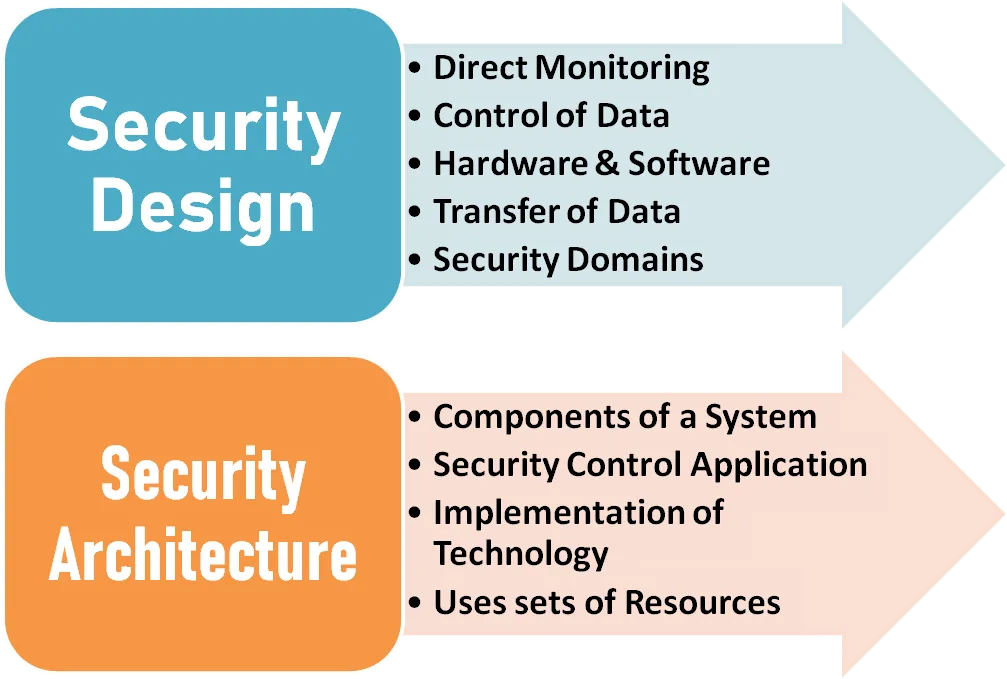
5.Different between Security Architecture to Design?
Security architecture is the set of resources and components of a security system that allow it to function. Security design refers to the techniques and methods that position those hardware and software elements to facilitate security. Items like handshaking and authentication can be parts of network security design.
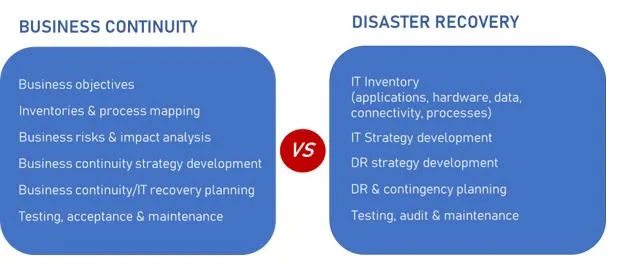
6.Different between Business Continuity Planning to D-i-s-a-s-t-e-r Recovery Planning?
Business continuity focuses on keeping business operational during a disaster, while disaster recovery focuses on restoring data access and IT infrastructure after a disaster. Meanwhile, a disaster recovery strategy helps to ensure an organization's ability to return to full functionality after a disaster occurs.
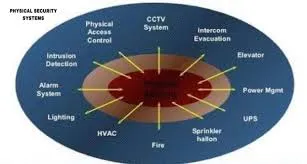
7.What is Physical Security Control?
Physical control is the implementation of security measures in a defined structure used to deter or prevent unauthorized access to sensitive material. Examples of physical controls are: Closed-circuit surveillance cameras. Motion or thermal alarm systems. Security guards.
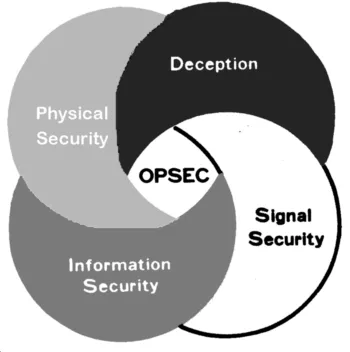
8.What is Operations Security?
Operations security (OPSEC) is a process that identifies critical information to determine if friendly actions can be observed by adversary intelligence systems, determines if information obtained by adversaries could be interpreted to be useful to them, and then executes selected measures that eliminate or reduce.

9.What is Law?
Law is a system of rules created and enforced through social or governmental institutions to regulate behavior, with its precise definition a matter of longstanding debate. It has been variously described as a science and the art of justice.

10.What is Investigation?
An investigation is a thorough search for facts, especially those that are hidden or need to be sorted out in a complex situation. The goal of an investigation is usually to determine how or why something happened. Investigations are usually formal and official.

11.What is Ethics?
Ethics is defined as a moral philosophy or code of morals practiced by a person or group of people. An example of ethics is a the code of conduct set by a business. Business ethics deal with ethics in business, and with the constant process of optimizing profitability in the context of what is right and what is wrong.
12.What is Information Security?
Information security is a set of practices designed to keep personal data secure from unauthorized access and alteration during storing or transmitting from one place to another.