
What is an Information Security Assurance?
The administration and protection of knowledge, information, and data is known as information assurance and security. It is a combination of two fields: Information assurance is concerned with the accessibility, integrity, authenticity, secrecy, and non-repudiation of data and systems.
Information Security Assurance Components:
- Availability - whether someone or something can be accessed or used
2.Integrity - involves assurance that all information systems are protected and not tampered with. IA aims to maintain integrity through means such as anti-virus software on all computer system, and ensuring all staff with access to know how to appropriately use their systems to minimize malware, or viruses entering information systems.
3.Confidentiality - is the safeguarding of data in a system such that it cannot be accessed by an unauthorized individual. This form of security is particularly crucial in military and government organizations that must keep their plans and capabilities hidden from adversaries.
4.Authentication - It entails ensuring that users are who they claim to be. User names, passwords, biometrics, tokens, and other devices are all utilized for authentication. Authentication is utilized for more than simply identifying persons; it's also used to identify devices and data communications.
5.Nonrepudiation - is the assurance that someone cannot deny the validity of something. Non-repudiation is a legal concept that is widely used in information security and refers to a service, which provides proof of the origin of data and the integrity of the data.
Difference between Certification programs to Common body language
This course on 'Body Language' is designed to help you understand the different aspect of body language so that you are able to use the information to your personal and professional advantage.
Differentiate the Governance and Risk management?
Governance, or corporate governance, is the overall system of rules, practices, and standards that guide a business. Risk, or enterprise risk management, is the process of identifying potential hazards to the business and acting to reduce or eliminate their financial impact.
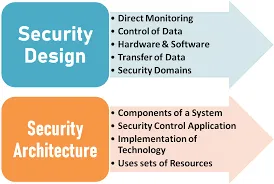
Different between Security Architecture to Design?
Security architecture is the set of resources and components of a security system that allow it to function. ... Security design refers to the techniques and methods that position those hardware and software elements to facilitate security. Items like handshaking and authentication can be parts of network security design.
Business Continuity Planning to D-i-s-a-s-t-e-r Recovery Planning
Business continuity focuses on keeping business operational during a disaster, while disaster recovery focuses on restoring data access and IT infrastructure after a disaster. ... A business continuity strategy can ensure communication methods such as phones and network servers continue operating in the midst of a crisis.
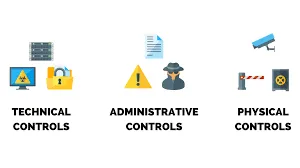
Physical Security Control
Implementation of security measures in a defined structure used to deter or prevent unauthorized access to sensitive material. Examples of physical controls are: Closed-circuit surveillance cameras. Motion or thermal alarm systems. Security guards.
Operations Security
Process that identifies critical information to determine if friendly actions can be observed by enemy intelligence, determines if information obtained by adversaries could be interpreted to be useful to them, and then executes selected measures that eliminate or reduce adversary

What is Law? - a rule of conduct or action prescribed or formally recognized as binding or enforced by a controlling authority.

What is Investigation? - An investigation is a thorough search for facts, especially those that are hidden or need to be sorted out in a complex situation. The goal of an investigation is usually to determine how or why something happened.

What is Ethics? - Ethics is concerned with what is good for individuals and society and is also described as moral philosophy. The term is derived from the Greek word ethos which can mean custom, habit, character or disposition.

What is Information Security? - Protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction. The terms information security, computer security and information assurance are frequently used interchangeably.