1. What is an Information Security Assurance?
Information assurance and security is the management and protection of knowledge, information, and data. Information assurance, which focuses on ensuring the availability, integrity, authentication, confidentiality, and non-repudiation of information and systems.
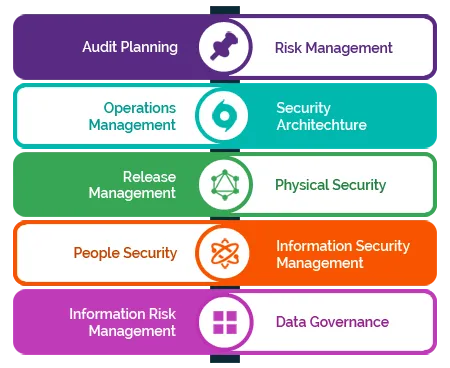
2. Components Information Security Assurance?
Information assurance (IA) is the practice of assuring information and managing risks related to the use, processing, storage, and transmission of information. Information assurance includes protection of the integrity, availability, authenticity, non-repudiation and confidentiality of user data.
3. Differentiate the certification programs to Common body language?
A certification program is a defined set of components or training programs offered by your organization to members to prove that they have achieved a measured level of knowledge within a designated timeline. It is a quick way to learn a new skill in a career you already have or to train for a job you hope to have
4. Differentiate the Governance and Risk management?
Governance, or corporate governance, is the overall system of rules, practices, and standards that guide a business. Risk, or enterprise risk management, is the process of identifying potential hazards to the business and acting to reduce or eliminate their financial impact.

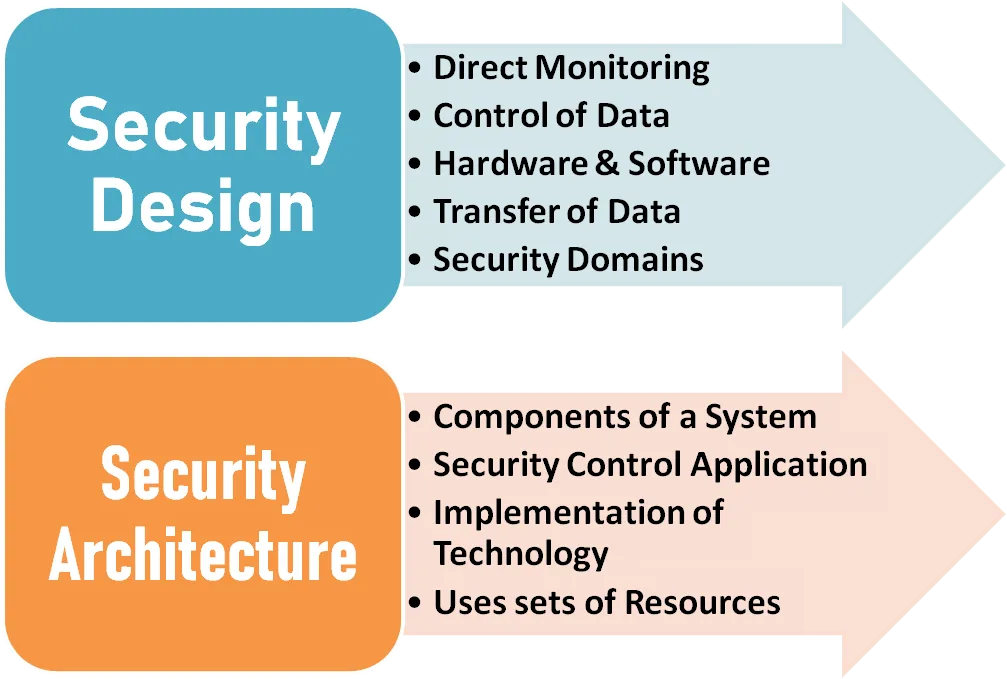
5. Different between Security Architecture to Design?
Security architecture is the set of resources and components of a security system that allow it to function. Security design refers to the techniques and methods that position those hardware and software elements to facilitate security.
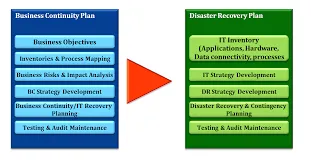
6. Different between Business Continuity Planning to D-i-s-a-s-t?
The differences are that a disaster recovery plan is referring to restoring data and accessing backups while a business continuity plan refers to getting systems back online and the business operations and areas associated with running the business.
7. What is Physical control?

Physical control is the implementation of security measures in a defined structure used to deter or prevent unauthorized access to sensitive material. Examples of physical controls are: Closed-circuit surveillance cameras. Motion or thermal alarm systems.
8. What is Operations Security?
Operational security (OPSEC) is a security and risk management process that prevents sensitive information from getting into the wrong hands. Another OPSEC meaning is a process that identifies seemingly innocuous actions that could inadvertently reveal critical or sensitive data to a cyber criminal.

9. What is Law?

10. What is Investigation?

Investigation is a detailed examination of accounts and enquiry into the state of affairs of the business or for a specific purpose. It involves the process of analyzing, collecting and presenting facts in a manner which enables the parties to know the essential facts regarding the matter under enquiry.
11. What is Ethics?

Ethics, also called moral philosophy, the discipline concerned with what is morally good and bad and morally right and wrong. The term is also applied to any system or theory of moral values or principles.
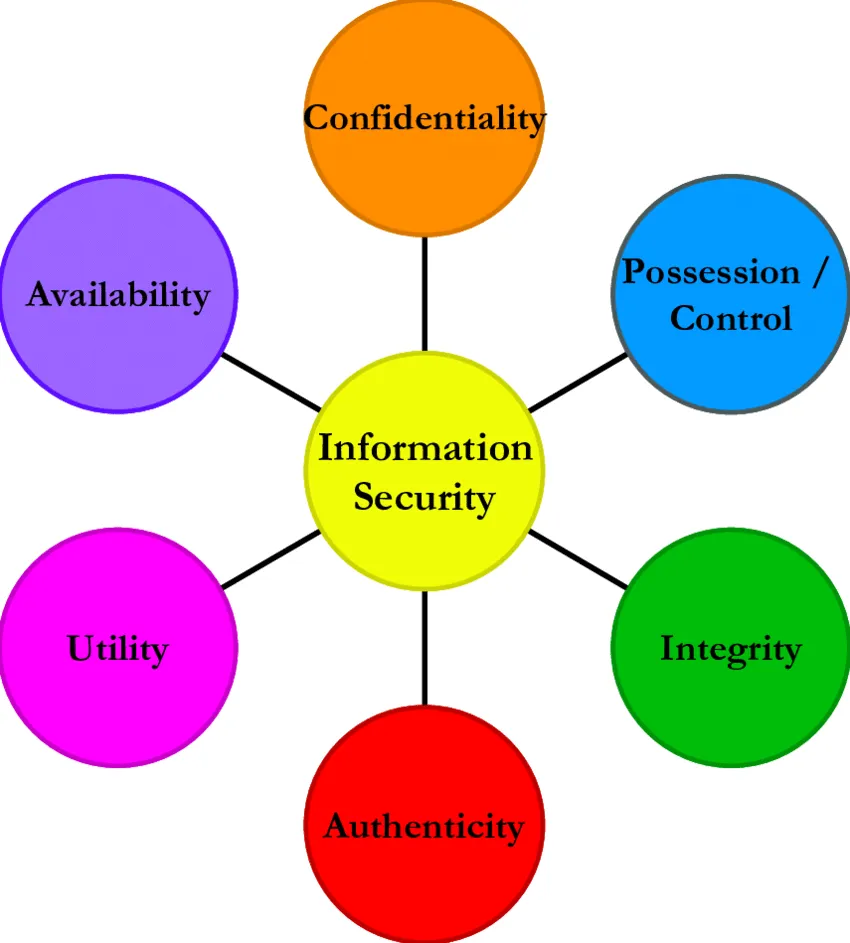
12. What is Information security?
The basic tenets of information security are confidentiality, integrity and availability. Every element of the information security program must be designed to implement one or more of these principles. Together they are called the CIA Triad
Information security means protecting information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction. The terms information security, computer security and information assurance are frequently used interchangeably.