
US indicts alleged culprit of HBO hack-and-extort campaign.
US prosecutors have pressed charges against an Iranian national who allegedly hacked into HBO cable TV network this summer, making off with various materials including unaired episodes of hit shows along with actors’ personal data before demanding $6 million in bitcoins on pain of releasing the materials.
Behzad Mesri, who went by the moniker “Skote Vahshat,” is facing charges on a range of federal crimes, including computer fraud, wire fraud, extortion and identity theft, according to a sealed indictment [PDF] that the US Attorney's office in Manhattanreleased on Tuesday.
The material that Mesri, 29, is reported to have got his hands on totals no less than 1.5 terabytes and includes then-unreleased episodes, along with scripts and plot summaries, of the famed Game of Thronesseries, as well as upcoming episodes of other showssuch as Ballers, Barry, Room 104, Curb Your Enthusiasm, and The Deuce.
The grand jury indictment describes Mesri as a “self-professed expert” in hacking who had previously worked for Iran to attack military systems, nuclear software systems and Israeli infrastructure.
According to a press release by the US Attorney's office for the Southern District of New York, Mesri was also a member of an Iran-based hacking group called the Turk Black Hat security team and conducted hundreds of website defacements against websites in the United States andelsewhere.
“Mesri now stands charged with federal crimes, and although not arrested today, he will forever have to look over his shoulder until he is made to face justice,” Southern District of New York district attorney Joon Kim was quoted as saying.
Mesri is thought to have started his hacking campaign in May, conducting reconnaissance on HBO’s computer network and employees and probing for vulnerabilities.Up until July, Mesri “successfully compromised multiple user accounts belonging to HBO employees and other authorized users, and used those accounts to repeatedly obtain unauthorized access to HBO’s computer servers,” according to the US Attorney’s office.
Between approximately July 23 and 29, Mesri allegedly engaged in his blackmail campaign.After the TV network didn’t pay the required $6 million in digital cryptocurrency, he began leaking portions of the stolen data on July 30.
Reuters reported in August that HBO had, in fact, offered $250,000 to cybercriminals in July in exchange for pushing back the deadline “for paying a much larger ransom”.The request – which a person acquainted with HBO’s response described as a delay tactic – prompted no response from the hacker.
Hackers hit plastic surgery, threaten to release patient list and photographs.
London Bridge Plastic Surgery & Aesthetic Centre (LBPS) in Wimpole Street, London, is a favourite haunt of surgery-addicted celebrities seeking facelifts and breast augmentations.
Famous clients include publicity-shy glamour model/author/reality TV star Katie Price, who just a few months ago made a video endorsing the surgery for her “silhouette face lift”.
The cosmetic surgery has embraced social media, even going so far as to broadcast breast implant operations live on Snapchat.
Chances are, however, that most of LBPS's clients wouldn't feel happy with the world knowing that they've “had some work done”, and would certainly prefer that any private photographs of their wobbly or intimate body parts did not fall into thehands of the public.
However, that’s precisely the risk – after it was revealed that a notorious hacking gang had broken into the cosmetic surgery’s network and stolen sensitive data and photographs.
The Dark Overlord, which has previously attempted to blackmail many organisations – including the likes of Netflix (over stolen episodes of TV prison drama “Orange is the New Black”), and Gorilla Glue, as well as leaking information from hacked investment banks and publishedmillions of healthcare records – has claimed that the hacked information may even include details of members of royalty.
A statement published on LBPS’s website confirmed that a data breach had occurred:
“We took measures to block the attack immediately in order to protect patient information and we informed the Metropolitan Police who launched an investigation.Regrettably, following investigations by our IT experts and the police, we believe that our security was breached and that data has been stolen.We are still working to establish exactly what data has been compromised.”
“Security and patient confidentiality has always been of the utmost importance to us.We invest in market-leading technology to keep our data secure and our systems are updated daily.We are deeply saddened that our security has been breached.”
“We are profoundly sorry for any distress this data breach may cause our patients and our team are available around the clock to speak to anyone who has any concerns by calling 0203 858 0664.”
Sadly this isn’t the first time that have seen cosmetic surgeries targeted by hackers.Past cases have involved other plastic surgery clinics based in London as well as Lithuania.
The hack at London Bridge Plastic Surgery is being investigated by London’s Metropolitan Police.
But for the clinic’s patients that is going to be small relief.When we place our trust in organisations, and share with them our most personal information, we have an expectation that it will be properly protected and kept far from the grasp of criminal hackers through following security best practices – such as encryption, strong passwords, multi-factor authentication, and so forth.
Other cosmetic surgeries who wish to avoid hackers damage their public image would be wise to invest properly in security now, or face the consequences later.
US rules on reporting cybersecurity flaws set to change according to source.
Just after 9AM Washington, D.C. time the US government published three documents that describe its Vulnerabilities Equities Policy (VEP) and the process by which decisions about vulnerability disclosure are made.Here are the documents:
Improving and Making the Vulnerability Equities Process Transparent is the Right Thing to DoA statement, posted on the WhiteHouse.gov website by Rob Joyce, the White House Cybersecurity CoordinatorVulnerabilities Equities Policy and Process for the United States GovernmentA 14-page unclassified PDF describing the Vulnerability EquitiesProcess (VEP) in some detailFACT SHEET: Vulnerabilities Equities ProcessA 3-page summary, including a listing of the Defensive Equity Considerations
This followed our earlier reporting that the Trump administration was set to release its rules for determining whether to disclose the cyber vulnerabilities that government agencies find, according to a national security official in the US who spoke to the Reuters news agency.
The anonymous source told Reuters that the revised rules would be released on whitehouse.gov on Wednesday.The changes are expected to make the process, which federal agencies go through when dealing with finding cybersecurity flaws, more transparent.
The move is likely to be seen as an attempt by the US government to fend off criticism that it routinely exposes internet security by keeping cybersecurity flaws and vulnerabilities secret.According to the report on Reuters.com, the proposed rule change will name the agencies involved in the process, such as the Departments of Commerce, Treasury and State.
Currently the US government employs an inter-agency review, created under former President Barack Obama.Known as the Vulnerability Equities Process, it is tasked with deciding what happens to any cybersecurity flaws that is discovered by the National Security Agency (NSA).
This approach to online security has received criticism from experts who claim a failure to disclose findings has a more negative impact on the industry, with Reuters pointing out the dangers experts find with the approach:
“The criticism grew earlier this year when a global ransomware attack known as WannaCry infected computers in at least 150 countries, knocking hospitals offline and disrupting services at factories.
The attack was made possible because of a flaw in Microsoft’s Windows software that the NSA had used to build a hacking tool for its own use.”
Named WannaCryptor, but also referred to as WannaCry, this malicious code spread rapidly by utilizing the eternalblue SMB exploit, part of a large collection of files that leaked from the NSA.
According to Stephen Cobb, a Senior Security Researcher at ESET, “The view among many security researchers, myself included, is that the risks of vulnerability hoarding outweigh the benefits in pretty much every case.”
While welcoming the increased transparency around the government's Vulnerabilities Equities Policy provided by today's statements and publications, Cobb points out that in 2017, “We witnessed the manifestation of one of those vulnerability hoarding risks: that the bad guys will cause hundreds of millions of dollars'worth of damage by exploiting a hoarded vulnerability.”
Adds Cobb, “In light of that incident there is a strong argument for saying that if a super-secretive agency can't keep secret vulnerabilities secret, then the government's duty of care to society would be better served by working with industry to fix allvulnerabilities as soon as they are discovered.”
Americans’ unease about cybercrime towers over conventional crimes.
Americans are more concerned about possibly falling victim to a crime made possible by the internet than any one “conventional” crime, a recent poll has shown.
As many as 67% of adult Americans are anxious, be it frequently or occasionally, about “having their personal, credit card or financial information stolen by computer hackers”, according to the annual Crime poll conducted by Gallup.Fear of identity theft came in a close second at 66%.
Meanwhile, the next worst-feared crime – having one's car stolen or broken into – came in a distant third in the 13-item worry list, raising concern on the part of 38% of a random sample of 1,028 respondents queried between October 5–11.
Indeed, Gallup itself was quick to note that “since 2009, Americans’ anxiety about identity theft has consistently topped their fears about other crimes by at least 19 percentage points”.
It was in that year that Gallup began to canvass Americans’ sentiments on identity theft, with the concerns about this crime consistently between 66-70% ever since.The question regarding hackers stealing personal information was added to the survey this year, “though prior surveys included questions on narrower cybercrime-related issues”.
The high level of fear of cybercrime dovetails with the self-reported rates of victimization, as 25% of the respondents reported that their personal information or that of their household member has been stolen by hackers over the past 12 months.When it comes to identity theft, the same was true for 16% of those asked.
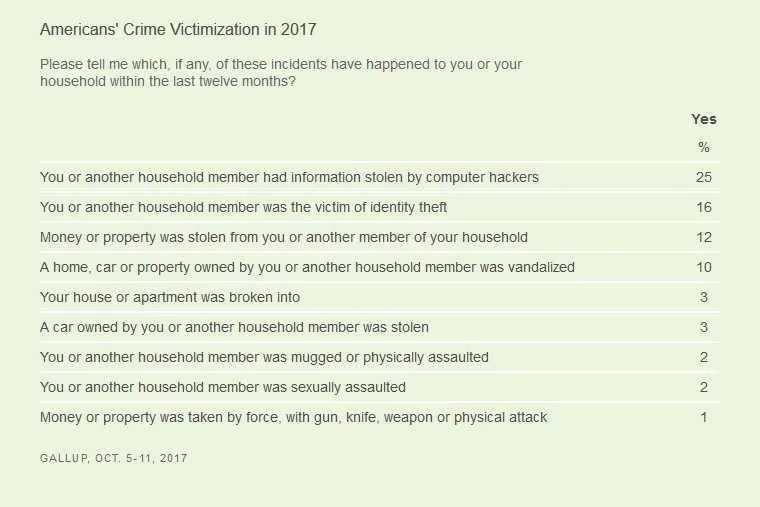
Image credit: Gallup
These findings also echo those of ESET’s own research, which revealed that Americans believe “criminal hacking into computer systems” is now a top risk to their health, safety and prosperity.
In a survey conducted this summer, ESET researchers Stephen Cobb and Lysa Myers found that US adults rated criminal hacking as more of a risk than other significant hazards, including climate change, nuclear power, and hazardous waste.
Yet again, reports of a conventional form of crime, “money or property was stolen from you or another member of your household”, only came in third on 12 percent.
The FBI’s Internet Crime Complaint Center reported an average of 280,000 complaints a year from 2000-2016, Gallup noted.
The poll was conducted in the wake of a massive data breach at US credit checking company Equifax, which occurred from May through July 2017 but didn’t make headlines until Equifax’s confirmation of the incident on September 7.
This breach, which saw hackers make off with the data of 143 million people, was itself preceded by reports of a rash of other high-profile data breaches in recent years.
The hacking of infidelity site Ashley Madison – while not the largest, it was unprecedented given the nature of the site’s service – affected 37 million people.The list of US-based businesses to have suffered major data breaches in recent years includes home improvement retailer Home Depot in 2014 and retail giant Target in late 2013.
Arguably, Yahoo has eclipsed them all, having suffered from two massive breaches in recent years, including one in 2013 that turned out last month to have affected all three billion user accounts on the service.
All told, the prevalence of large-scale security incidents – and the extensive media coverage thereof – are seen as having contributed to the Americans’ worry of cybercrime.
Bitcoin heist nets thieves $1.2 million – and site warns “don’t store your coins on the net”
Cyberthieves stole more than 4,100 bitcoins, worth $1.2 million, in a hacker “heist” on a site used to store the currency online, inputs.io.The hack is among the largest thefts in the currency’s four-year history.
The bitcoins were stolen after hackers accessed the site inputs.io, according to SlashGear.The site offered online wallets for storing bitcoins, which also mixed up wallets to anonymize coins and speed up payments, according to Wired.
TradeFortress, who worked for the company, said in a forum post, “I don't recommend storing any bitcoins accessible on computers connected to the internet.” Bitcoin can be stored in offline “wallets”, or even written down as a private cryptographickey, Wired points out.
TradeFortress has said he will offer partial refunds from his own funds, and from the remaining bitcoins on the site – totalling 1,540 bitcoin.
He also said that he was worried about his personal safety.Yahoo News said that the “anonymity” of bitcoin transactions has led to speculation that the robbery may have been an “inside job”.
Some forum users taunted him with jokes such as “buy me a Rolex at least.” Tradefortress does not want to be identified, as he is “not much older than 18”, according to an ABC News report.
Slashgear’s report said the attackers compromised, “the hosting account through compromising email accounts (some very old, and without phone numbers attached, so it was easy to reset).The attacker was able to bypass 2FA due to a flaw on the server host side.Because of this, the hackers did gain access to the wallet’s database.”
The attacks happened on October 23 and 26, according to Wired.
The hackers transferred the bitcoin backend code to another compromised server.The site said in an official message, ““I know this doesn’t mean much, but I’m sorry, and saying that I’m very sad that this happened is an understatement.”
The alleged theft is one of the largest in the currency’s four-year history, according to Yahoo.TradeFortress said that he was unlikely to report the theft to police.
“The police don’t have access to any more information than any user does when it comes to bitcoin.Some say it gives them control of their money,” he said in an interview with ABC.
ESET Malware Researcher Robert Lipovsky wrote in an earlier We Live Security post that Bitcoin and other crypto-currencies are being targeted by cybercriminals.
“There are numerous malware families today that either perform Bitcoin mining or directly steal the contents of victims’ Bitcoin wallets, or both,” Lipovsky writes.




