
Introduction
As we near the launch of the EOS mainnet, BitSpace has been working with a team of DevOps and security experts from Praqma. During this period we have started upgrading our architecture plan to enterprise level.
We aim to constantly enhance our standards. Leveraging our experience with previous DPOS systems such as Bitshares and Steem and collaborating with experienced IT consultancy firms allows us to add an extra layer of expertise to the Block Producer server infrastructure.
Our aim with this post is to provide valuable information to the EOS ecosystem and fellow Block Producer candidates, and do our part in the community tech debate. The results outlined below do not jeopardize our security measures and are intended for informational purposes only. This report is focused on running a Block Producer, not on launch practices.
Architecture
Our Block Producer at Green Mountain will be completely isolated from the outside world. Two high speed lines and VPN connections will connect them to multiple seed nodes, in the cloud (see diagram below).
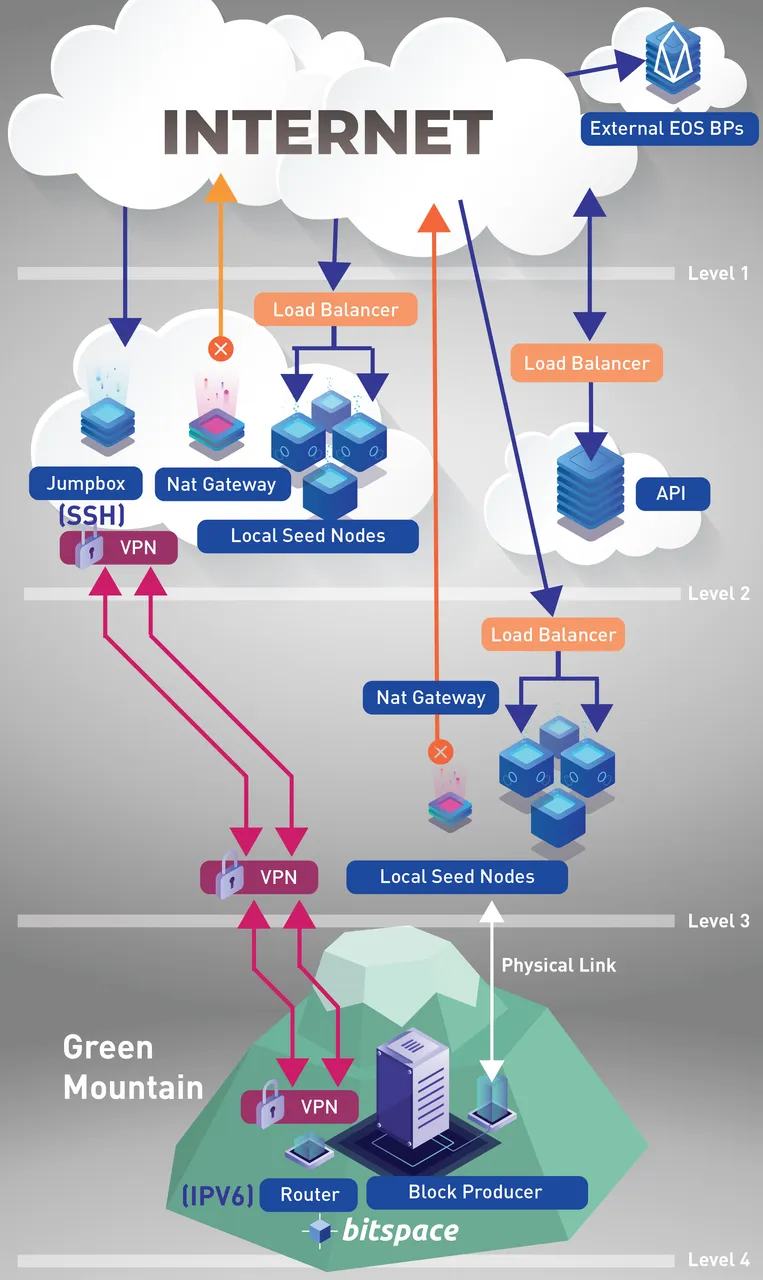
The seed nodes in the cloud will be using the latest cloud-based DDoS protection systems available today. We will be using multiple clusters of seed nodes spread throughout multiple cloud providers and again spread over multiple regions. This makes an attack very hard to coordinate. If a cluster is compromised, it can be shut down and all traffic passed over to an alternate cluster.
Within one of our seed node clusters we will have multiple seed nodes running under a load balancer, a NAT gateway and a Jumpbox. A Jumpbox is a secure computer that all admins first connect to before launching any administrative task or use as an origination point to connect to other servers or untrusted environments. A NAT gateway is used to enable instances in a private subnet to connect to the internet or other cloud services but prevent the internet from initiating a connection with those instances.
In addition, we will have one primary physical seed node cluster close to Green Mountain with a similar non-cloud setup. The Block Producer will sit behind an IPV6 connection which will only be known to the admins of BitSpace. That way it is not traceable from the internet.
Throughout all of this the Block Producer will be isolated and protected with its own physical firewalls and DDoS systems. Redundant BPs with their own VPNs will be waiting in an alternate location in the unlikely case that the primary BP is compromised or fails.
The BitSpace DevOps and Security architecture is work in progress and under constant development. We will post updates as we make changes and improvements to the proposition. We welcome feedback from the EOS community and actively encourage discussion around the choices we have made so far.
BitSpace looks forward to a successful launch and we hope the EOS community can benefit from the information provided. Go EOS!
