Publish0x easily became my favorite platform to write content for, whether it be Cryptomarket, Digital, or the hottest tokens, Publish0x quickly took the cake. My endearment for the platform was quickly followed by a trust for the network. So, you can imagine my surprise to see the "DDoS attack" memo/warning atop the website's page upon logging in. Although I had heard of this attack before I was pretty unclear exactly what a DDoS attack actually WAS, or what DDoS even stood for.
If you are anything like me and want to know more about DDoS attacks, or the potential risk associated with continuing to browse our beloved sites that are under attack (if there are any) then please, continue reading

What is a DDoS attack?
When it comes to electronics, a Distributed Denial -of- Service, (or DDoS attack) serves as an attack on a website that's sole purpose is to cause malfunction within the site as a result of an extremely heavy flow of traffic to the site. The traffic in question, however, is not "real" traffic, but rather they are "zombie" botnets (a large group of bots) that do nothing constructive, quite the latter actually, as these bots are highly capable of causing extreme disruption, the loss of millions of dollars, not to mention simply being a huge nuisance with the ability to infect hundreds, in some cases even thousands of computers that house them as they spit out there malware.
To try to make DDoS attacks easier to understand, think about it from a literal standpoint. Meaning the "botnet traffic" I depicted above is tangible traffic, so cars on the freeway are jampacked as it is in rush hour traffic and then BOOM a multicar accident occurs, amidst the already terrible traffic, causing a HUGE traffic jam.
What would that mean for all of the cars that, unbeknownst to them, have become part of the reason for this traffic jam? Everyone involved would be late or not make it to where they are headed at all dueto the extreme slow down. A DDoS attack does the same thing but instead of vehicles, the traffic is users on a network. The "multicar accident" is the botnets. And the traffic jam, in general, is the hacker himself.
Please reference the "flow" chart below, depicting in a picture what a DDoS attack looks like on paper
DoS attacks vs. DDoS attacks:
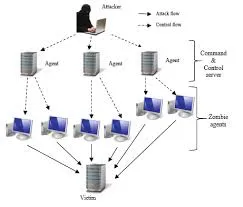
There is a lot of room for confusion in differentiating DOS attacks from DDoS attacks. The primary difference between the two is that a DOS (denial of service) attack sends a surge of traffic through the server, resulting in the website being shut down. Whereas a DDoS ( Distributed Denial of Service), as the name suggests, DDoS uses multiple machines to overload a specific computer/network/resource. The name "Distributed Denial of Service" comes from the fact that as the "fake" or "botnet" traffic is increasing throughout the network route, the network is in turn becoming more and more clogged. Therefore, intended customers/visitors to the site are unable to serve their intended purpose upon entry to the website, if they are able to load the site at all, hence the word denial, as the user is denied access to the site as a result of the fake "traffic jam".
The term distributed in this context is referring to the fact that these traffic sources are oftentimes distributed worldwide which makes thwarting the attack a very difficult task as opposed to stopping an attack via a single IP address, as one would see with a traditional DOS attack.
The Process Of Mass Destruction:

Step One: The quantitively, calculated creation of the "zombies"/ Botnets. Many zombies are victims of hackers that have fallen privy to this malicious attack and the victim may have no idea they have even been targeted. Let alone, unbeknownst to them, became an important component of the attack itself!
Step Two: Commence the attack of the targeted network per the zombie bots.
Step Three: Each bot sends requests to the target's IP address.
Step Four: Flood targeted computer/ electronic device with expendable requisitions that are useless. Thus corrupting the server and causing damage to not only the order and functionality of the servers and network services of all the users connected at that time.
Step Five: Corruption of the server is caused, as well as damage to not only the order and functionality of the servers but also to the network services of all the users connected at that time.
Variations of DDoS attacks:
While there are many, many, many different variations of DDoS attacks, I have listed the three most common below:
Volume-based attacks: Uses the heavy traffic flow tactic to overwhelm the network bandwidth.
Protocol attacks: Focuses on imposing the server's assets/ capital.
Application attacks: This is the most detrimental and stringent version of the DDoS attacks and places their center of attention on Web Applications.
What motivates the hackers to issue the attack

DDoS hackers that carry out these attacks have many motivating factors, all of these reasonings being of course selfish in nature. These reasonings vary from political gain to terrorist-like activities. DDoS attacks are often seen within a business setting as attacks are often launched as a way to get a leg up against competitors and of course capitalization motivates many hackers to initiate a DDoS attack as successful completion of such attack stands to be very profitable for the attacker. Some even demand "ransom" in large amounts to end the attack and return the sever to regular functionality again.
How can you protect yourself from DDoS attacks/unwillingly becoming PART OF the attack

Many internet users lack even the most basic form of anti-virus protection on their computers which is the first and most basic step in preventing DDoS attacks. Unfortunately, as I mentioned earlier, many victims that are implicated in the attack via their computer being unknowingly metamorphosized into a "bot/zombie"' are completely oblivious to the fact they have been incorporated into the hacker's scheme until it is far too late for the individual to successfully thwart the perps diabolical plan of attack.
Installing a firewall is referred to as defending the network perimeter. This is just a fancy way of saying install firewalls and anti-virus protection. This is unfortunate, given this scheme is completely preventable if the user were adhering to even the most basic security protocols that are widely known, and oftentimes free, for those wishing to surf the net and download attachments without the added stress of being hacked or having their computer infected with a virus, such as becoming a DDoS bot!
Early detection is also important in thwarting a hacker's plan to ignite a DDoS attack on a person or more commonly a business.
Business owners can also be proactive by overprovisioning bandwidth. This just means adding extra storage or space to their bandwidth ( the max amount of data allotted to be transmitted via an internet server within a fixated time frame).
Contact/ hire a DDoS mitigation specialist. If this is within one's financial means then this would obviously be a very plausible solution to a DDoS attack, however, this is not an affordable option for everyone.
Having a plan of defense ready to spring into action if an attack should occur. As I mentioned earlier, early detection is one of the best ways to survive a DDoS attack unscathed. Early detection, coupled with a solid plan of action, leaves the hacker with no hope of taking down the server.
Who is affected by DDoS attacks?
While DDoS attacks pose no threat to those that are innocently surfing the net and come across an infected network, these attacks are detrimentally dangerous to businesses, particularly smaller businesses, as substantial revenue loss is often times the end result of a DDoS attack.
It is also important to note the threat that DDoS attacks pose to the infrastructure of the internet. While an attack is in progress the attack can account for over twenty-five percent of internet traffic, and unfortunately, these attacks are predicted to slow down any time soon. In 2022 Cisco estimates that the amount of DDoS attacks will likely increase from just under 8 million at precisely 7.9 million attacks measured in the year 2018, to a probable high of 15.4 million throughout this year alone.
What did we learn about DDoS/ DDoS prevention?

What have we learned today? Well, in short, DDoS attacks are growing in popularity, thus posing more and more of a threat to the infrastructure of the internet as we know it. They are a highly effective attack that a hacker can use to take down a business, seek revenge, or simply capitalize on someone else's hard work. It is important to remember that there are MANY different variations of DDoS attacks, the attack comes in all shapes and sizes. Also, don't forget that there is a significant difference between a DDoS attack and a DoS attack. (and no it is not just the addition of the letter D to the acronym.)
Hackers initiating DDoS attacks can target literally anyone even the "big names" or "successful" companies. Historically DDoS attacks have been launched against names as big as Google, PlayStation, Amazon, and GitHub, just to name a few. Attacks are categorized by traffic amount and the vulnerabilities that are being targeted, not by the business that is behind the server.
And finally, I think the most important takeaway from this post is that DDoS attacks are not only possibly preventable by defending the network perimeter, coming up with a good game plan should an attack be attempted, or by expanding the network bandwidth. Don't forget early detection of DDoS attacks could potentially be a make or break it in the end.
I hope you enjoyed this post as much as I did writing it, and hopefully, you learned a thing or two about DDoS attacks and if not at the very least found this post entertaining.
DDoS Dictionary:
Bots: An electronic device that has unknowingly been infected with malware thus allowing them to be controlled by the hacker that is behind the DDoS attack. Many hackers are able to infect with malware that may lay dormant for long periods of time and is virtually undetectable by the owner.
Botnets: A large group of Bots that are hard to detect as they are real internet devices making differentiating between botnets and real computers extremely difficult.
Spoof Requests: A request that is sent from a spoofed IP address clogging the server making it impossible for legit requests to get through. The word spoof means fake, for example, fake request, fake IP address, etc.
Bandwidth: The maximum amount of data that is transmitted via internet connection within an allocated time frame. People often confuse bandwidth with the speed of the actual internet when it is actually the capacity of information that can be sent over a connection in an allotted amount of time that is calculated in Megabits Per Second (MBPS).
Cisco: A product/company used to protect against DDoS attacks.
Packets per second: The scale at which DDoS attacks are measured