

Dear my steemian friends, in this section I will discuss the pseudocode of the combination of Vernam Cipher and Rivest Cipher 4 algorithms in the encryption and decryption process in Cryptography. Immediately in the following discussion.
Research Result
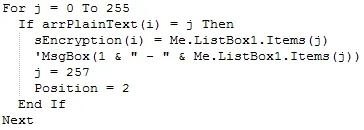
The following are the pseudocode results of the combination of Vernam Cipher and Rivest Cipher 4 algorithms. The combination of the two algorithms is done by determining the position one (first row). After the first position is found (the fourth row) is continued by determining the second position as the key (ninth row). So on, this process is carried out until the encryption process is complete.
Pseudocode

In the form of coding, the pseudocode above can be written as

Coding Explanation
Position = 1
- Do the loop from 0 to the length of the plaintext character
- Take decimal values from plaintext
- For position 1, search for the arrPlainText value in sBOX f(1), according to the sequence number of j
- For position 2, search for the arrPlainText value in sBOX f(2), according to the sequence number of j



Discussion
For example, encryption will be done using the combination algorithm RC4 and Vernam Chiper. The plaintext used is HELO with the key 2573.

1. Key Formation Process f(1)
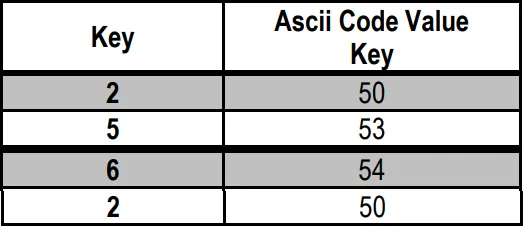
To form the key f(0) the method is done by creating an ascii code value, as shown in the table below:
2. Formation of Keys f(2)
To show how RC4 works on a basic level, it will be done on a 4-bit statearray. This is because it will be very difficult to manually describe the RC4 process with a 256-bit state-array. This time, the author tries to form the key f (1) obtained from the key 2573. The first thing to do is initialize the S 4 bit array so that the S-state arrays and state-array K are formed as follows.

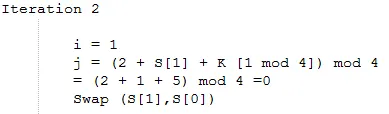
Initialize i and j with 0 then do KSA to create random state-arrays. Further explanation of iterations can be explained as follows.

The result obtained array S

So the array S results are


So the array S results are

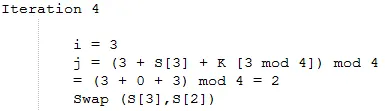
The result obtained array S

After doing KSA, Pseudo Random Generation Algorithm (PRGA) will be performed. PRGA will be done 4 times because the plaintext to be encrypted is 4 characters. This is due to the need for 1 key and 1 XOR operation for each character on the plaintext. The following are the stages of earning the encryption key with PRGA.





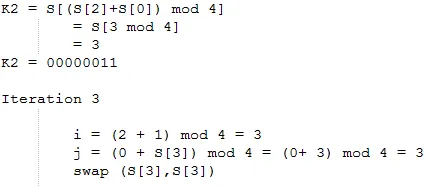

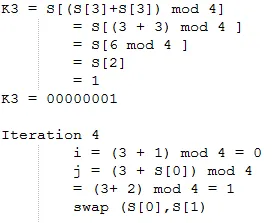

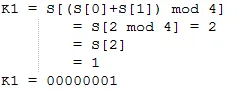
Thus the key f (1) formed is



Wondering How Steemit Works, Read Steemit FAQ?

