

Combined Vernam Cipher and RC-4
Looking at the shortcomings of these two algorithms, a number of techniques are used to reduce these shortcomings, among others by combining the two algorithms to obtain a new algorithm that is very different from the previous algorithm, while the process of combining the algorithm is carried out as follows:
Encryption Process:
Stage 1
Do the first key formation by converting the key character into the Ascii Code form defined as f(1)

Stage 2
Perform the formation of the second key with the algorithm RC-4 defined to be f(2)

- Steps 1: Perform S-Box Randomization

Stage 3
For f(1,1) and f(1,2) for a long table column 0 s / d 255
Stage 4
Fill the table for f(1.1) with a value of 0 to 255

Stage 5
Next is to fill in f(1,2) with the value starting from the key value f(1), if the value f(i) has been entered then fill in the next column in the order of 0 to 255 without entering the number value that has been entered previously.

Stage 6
Next is to fill in f(2.2) with the value starting from the key value f(2), if the value of f(2) has been entered then fill in the column then enter the order 0 to 255 without entering the number value that has been entered previously.

Stage 7
To do encryption, permutation is done in the following ways:
- Look for the Ascii Code value of Plaintext P(i) in the row of numbers f(1,1) if it is found to take the value f(1,2) according to the order of the plaintext as Ciphertext C(i)
- Next Find the Ascii Code value from Plaintext (i) in the row of numbers f(2.1) if it is found to take the value f(2.2) in accordance with the order of the plaintext as Ciphertext C(i)


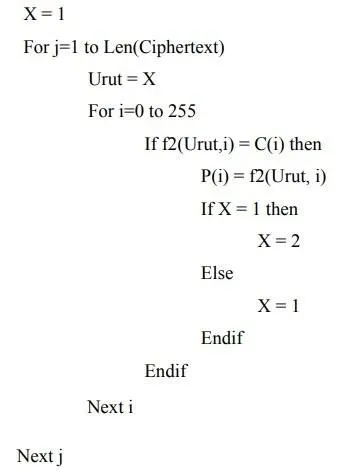
Decryption Process:
Stage 1
Do the first key formation by converting the key character into the Ascii Code form defined as f(1)

Stage 2
Perform the formation of the second key with the algorithm RC-4 defined to be f (2)

- Steps 2: Perform Randomization S-Box

Stage 3
For f(1,1) and f(1,2) Make a table whose column length is 0 to 255
Stage 4
Fill the table for f(1.1) with a value of 0 to 255

Stage 5
Next is to fill in f (1,2) with the value starting from the key value f (1), if the value f (i) has been entered then fill in the next column in the order of 0 to 255 without entering the number value that has been entered previously.

Stage 6
Next is to fill in f(2.2) with the value starting from the key value f(2), if the value of f(2) has been entered then fill in the column then enter the order 0 to 255 without entering the number value that has been entered previously.

Stage 7
To do encryption, permutation is done in the following ways:
- Look for the Ascii Code value of Ciphertext C(i) in a row of numbers f(1,1) if it is found to take the value f(1,2) according to the order of the plaintext as Ciphertext P(i)
- Next Find the Ascii Code value of Plaintext(i) in the row of numbers f(2.1) if it is found to take the value f(2.2) in accordance with the sequence of the Ciphertext as Plaintext P(i)



Wondering How Steemit Works, Read Steemit FAQ?

