If you go to a coffee shop or at the airport, and you're using open wireless, I would use a VPN service that you could subscribe for 10 bucks a month. Everything is encrypted in an encryption tunnel, so a hacker cannot tamper with your connection. -- Kevin Mitnick
Asymmetric Encryption

- A key pair is used: one key is used for encryption and the other for decryption.
- Public yey is publicly available
- Private key is must be kept secret
- Either key can encrypt and either key can decrypt
- Encrypt with public key & Decrypt with private key
- Encrypt with private key & Decrypt with public key
- Message encrypted with private can not be decrypted with private
- Message encrypted with private can not be decrypted with private
Examples of Symmetric Encryption
- Diffie-Hellman key Exchange
- RSA Algorithm
- ECC-Elliptic Curve Cryptography
1. Diffie-Hellman key Exchange
It is a method of exchanging keys between two parties using diffie-hellman key exchange method. Diffie-Hellman is the name of two pioneers of Cryptography Whitefield Diffie & Martin Hellman, I'm the die-hard fan of this two guys. So let's continue our topic Diffie-Hellman
Key Exchange, The very very very Popular example of Diffie-Hellman key Exchange is Alice and Bob, about how they exchanging their keys with each other:
!
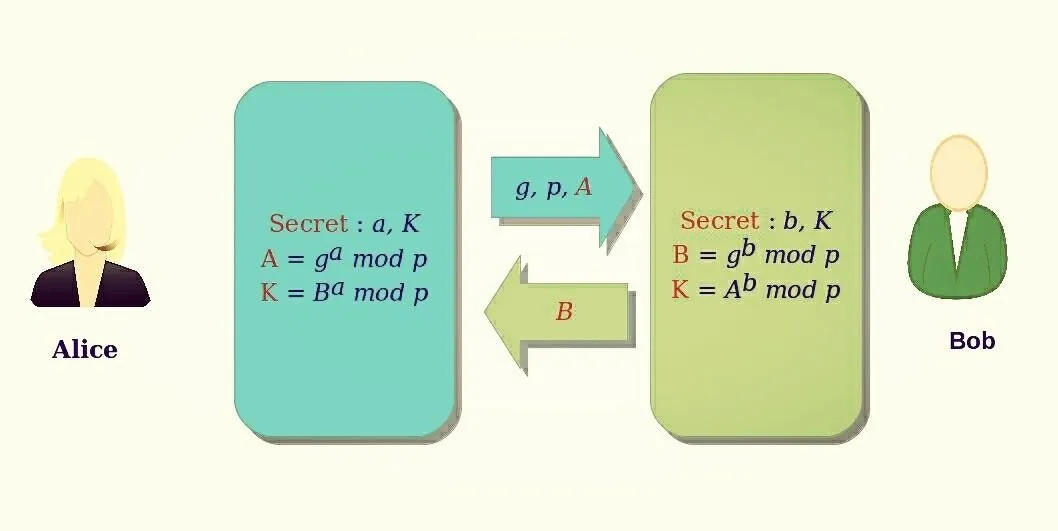
Used for
- Key Exchange
- Lets two(or more) parties that don't know each other to establish a jointly shared secret key.
How it Works
- Easy to compute but hard to reverse
History
- The original public/private CONCEPT
Security Considerations
- No authentication by itself
2. Rivest Shamir Adleman (RSA)
The RSA algorithm was published by the best friends and pioneers of Cryptographers Ronald Rivest,Adi Shamir & Leonard Adleman. RSA Algorithm uses primes to encrypt data with is easy to generate primes but if want to turn back it will take million of years without the key primes.
RSA members are in following photo

Used for
- Key Exchange
- Data Confidentiality and Digital Signature
How it Works
- Uses two large prime integers
- It is easy to find the product of the two primes but hard to find the primes from the product
- 100 times slower than Data Encryption Standards(check my previous post about Cryptographic Concepts)
History
- Published in the late 1970s
Security Considerations
- Problems arise when using prime number that are too small
3. Elliptic Curve Cryptography(ECC)
Oh one more interesting topic, Now Cryptographers uses physical concepts to improve computer security and invent cryptographic systems like ECC,
Following drawing shows the short and sweet review for ECC
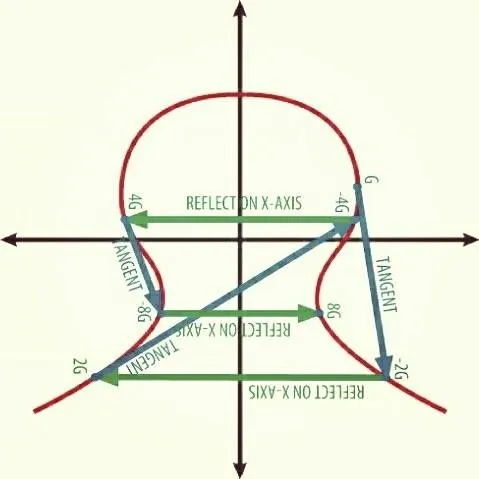
Used for
- Smaller less powerful devices like spycams
How it Works
- An elliptic curve & one point of the curve is chosen & made public
- Keys are calculated from that curve
- Easy to calculate hard to reverse! Same as RSA algorithm
History
- A cryptography concept with many implementations.
- Many companies have their own version of ECC.
Security Considerations
- Still being studied but currently considered strong if parameters are chosen properly.
Thank you so much my friend for reading my next post, I hope you liked it, And my next post will contain Cryptography Concept | Digital Signature & Non-repudiation which will published in next 24 hours, so check this out also,
Your Pal @sujityadav :)
If you want to about previous concepts then visit my page @sujityadav and see the more posts about cryptography. :) *Feel free to Flollow me: @sujityadav if you like my post*
Thank you for reading my posts & all of your responces.
@sujityadav