About Goldilock ?
Goldilock is an ultramodern storage system and is very safe wherever users are stored offline by means of physical air ventilation. Therefore, the wallet cannot be accessed from the internet. This means that reliable information from hackable digital (internet).

Goldilock devices will, therefore, always be outside the reach of the internet until users choose to access their data. Then, whether the device will be connected to the internet through special non-IP technology, and the data can be accessed through secure web login. The device is then physically disconnected after the client is finished. Wait what about the Goldilock Company? The Goldilock institution does not have access to user data stored on encrypted devices.
GoldilockToken LOCK
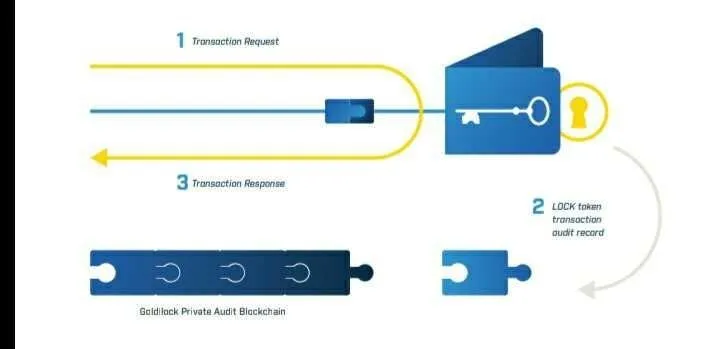
Goldilock will also register the token known as "LOCK". Users must purchase this KEY token that will allow them to store their private keys for their digital assets. Token LOCK will be required to access the Goldilock wallet. The science behind this is:
When a user enters the Goldilock Wallet, Wallet will ask the NEO public Blockchain to confirm the public key address the user has to the LOCK token. If the user's public key address has a LOCK token, then Goldilock Wallet will be launched in the user's browser. When a user is given access, Wallet will write audit information to our Personal Audit Blockchain. This audit entry will ensure that every time your private key is taken online, this access is written to unchanged storage that can be asked from the Goldilock Wallet. LOCK tokens allow Goldilock to provide users with a record of their node activity, while keeping users' data encrypted and locked even from everyone including the Goldilock team. In addition to,
Problem
Cryptocurrency investors and sensitive digital asset managers are currently forced to choose between cold hardware storage solutions held privately, which can be stolen, hacked, misplaced, destroyed or confiscated; and online wallet online, which is vulnerable to hacking, denial of service, and custodian trusteeship company. Without a safe, improved, and safe crypto key storage solution, both institutions and individuals continue to be plagued by financial losses that often occur due to their key mismanagement.
Traditional cold storage solutions are not the answer to providing investors with key management solutions that are appropriate for their cryptocurrency. The paper and USB buttons can be lost, stolen, or damaged. An encrypted cold storage solution offered by groups such as Xapo or Coinbase has very limited accessibility that does not handle most of the needs of institutional detention. Storing an encrypted key in an inaccessible bank safe may be appropriate security for individuals or institutions that do not want to trade, but getting access to USB takes days, which is not practical for handling active assets.
Heat storage solutions also prove unsuitable when it comes to key detainees. Simply put: everything that is connected to the internet can be hacked. Considering the 4 billion records that violate email, bank and credit card accounts affect over the past two years, and given that more than $1.2 billion in Cryptocurrency has been stolen in the same period, it is clear that the traditional digital asset storage industry is compromised.
** Goldilock SOLUTIONS**
Goldilock is built in three core locations:
USERS NEED ACCESS TO PERSONAL DATA QUICKLY, BUT ONLY OCCASIONIONY AND FOR A SHORT TIME. BEFORE, THE ONLINE DATA IS MORE USEFUL FOR HACKERS FROM THE RIGHTFUL OWNER.
PERSONAL DATA (INCLUDING PERSONAL KEY) MUST BE LICENSED, GUARANTEED FROM PHYSICAL CONTACT AND RELATED LEGAL ERRORS, AND FULLY CANCELED.
PERSONAL DATA AND PERSONAL KEYS MUST BE QUICKLY ACCESSABLE WHEN NEEDED.
SOLUTIONS FOR CONSUMERS
*Private Lock Storage
For individual consumers, Goldilock will consist of an encrypted storage device, which is stored in a safe inside a secure data center. This device is always offline and is physically disconnected from the Internet until the client chooses to access it. Through authorized non-IP orders by consumers through the Public Switch Telephony Network (PSTN), storage devices will be installed remotely and can be accessed online through secure web logins. Clients can directly access their data using encrypted channels to complete transactions. After the client completes each and all desired transactions, devices that securely manage the private key are physically disconnected from the Internet. Goldilock does not have access to keys or data stored on client encrypted storage devices.

SOLUTIONS FOR INSTITUTIONS
Cryptocurrency exchange
Public-based cryptocurrency exchanges often also act as key guards. In the past year alone, their dependence on contemporary security methods has generated billions of dollars in stolen cryptocurrency.
Instead of storing client keys in online hot wallets or leaving them disconnected and inaccessible in deep cold storage, Goldilock allows cryptocurrency exchange to depend on our online-on-demand environment, reducing transaction processing time and allowing better handling of past periods peak crossing as long as the market is inevitable.
For more information, watch this brief introduction:
Other Information & Resources:
Leadership

https://steemit.com/crypto/@originalworks/810-steem-sponsored-writing-contest-goldilock
Goldilock2018
