VI Relaed Aisa
This post was written with the pure intention of finding vulnerabilities in Bitcoin Core and the ecosystem, and did not attempt to damage or damage third parties by attempting actual hacking through virtual or physical operating systems. Advance notes.
Bitcoin's private key may only be known to you or stored in a wallet on your computer, or as an internet management program or paper wallet. If you know the corresponding private key, you can move Bitcoin stored in the corresponding public key.
The public key assigned to the Bitcoin private key is not created by the private key itself, uses the elliptic curve and the set of constants defined in the secp256k1 standard to compute the public key. After hashing using SHA-256 and RIPEMD-160 encryption method, Base58Check encoding process is used to generate the address. Since it is made by one-way operation method, finding the private key which is the pair of the public key by decrypting it using only the public key cannot be decrypted by the current computing performance of the personal desktop.
Therefore, most of the existing 'bitcoin hacking' methods hack the server or database of a centralized exchange to steal the user's or system's main information and steal Bitcoin.
Bitcoin network is composed of nodes divided into 4 types: wallet, miner, full blockchain, and network routing to build a decentralized system. In other words, the entire network is constructed and validated through the data exchange of each node, not centrally controlled, operated, and managed.
** i have one question came up here. "Can nodes in the Bitcoin network be safe from hacker attacks?
Is it really true that only Bitcoin in a centralized operations management system (eg exchange) is vulnerable to hacking? " **
Bitcoin nodes fall into four categories:
Reference Client [Form of complete network including all nodes. This is the case for Bitcoin Core.]
Full Blockchain Node [type with network routing function and full blockchain data]
Solo Miner [Full Blockchain, Network Routing Function and 10 Minutes of Effective Trading Block and Main Chain Connection]
SPV [Nodes for simple transactions and validation only]
Among the four nodes, the reference client and the SPV are 100% likely to have a physical operating system or a wallet in the system.
There is only one reference client connected to the full blockchain, but there is a possibility that other nodes can also store wallet applications or private keys as text data.
so, i assuming that all system have wallets exist, the following hacking techniques were conceived.
Session hijacking to the IP of the Bitcoin Core node. and then privileged attack to the node system and steals the private key.
Preparations : Bitcoin Core, Wire Shark, Moba X Term, VM
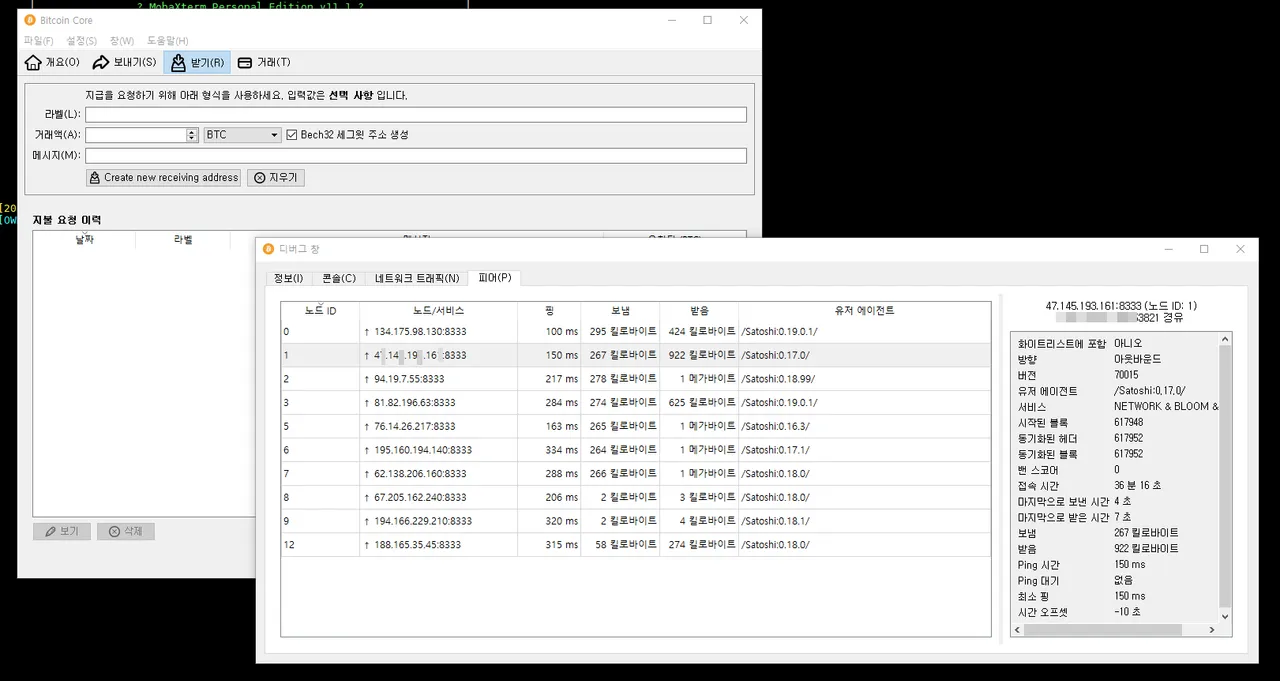
Identifying peer nodes through Bitcoin Core reveals the IPs of the nodes via block data. The first thing to note is that the IP ports of Bitcoin Core Full Nodes are open to port 8333 (P2P). A full node or SPV node target opened on port 8333 is very likely to have a Bitcoin wallet on the computer, and it targets these nodes.
Access Target (Node): 4x.14x.19x.16x: 8333 (Node ID: 1)
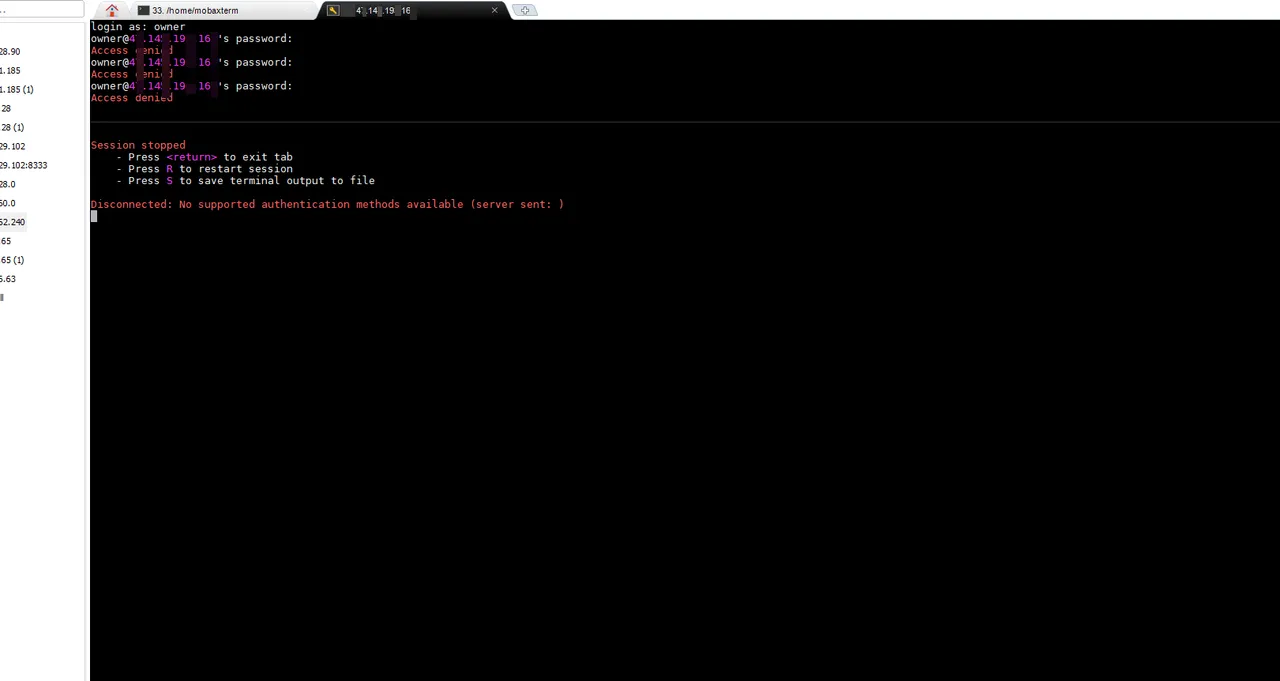
I tried to connect to an SSH session using Moba X Term. As a result of putting 'Owner' user name in the login ID, it was confirmed that the user exists. I tried to enter the password, but failed three times or more. This confirms that the node IP has an open port for SSH connection.
The peer automatically obtains the IPs of the active nodes through the dynamic DNS Seed server to broadcast with that node. The DNS seed node provides the peer with the addresses of other nodes that store the block database, that is, nodes such as 4x.14x.19x.16x: 8333.
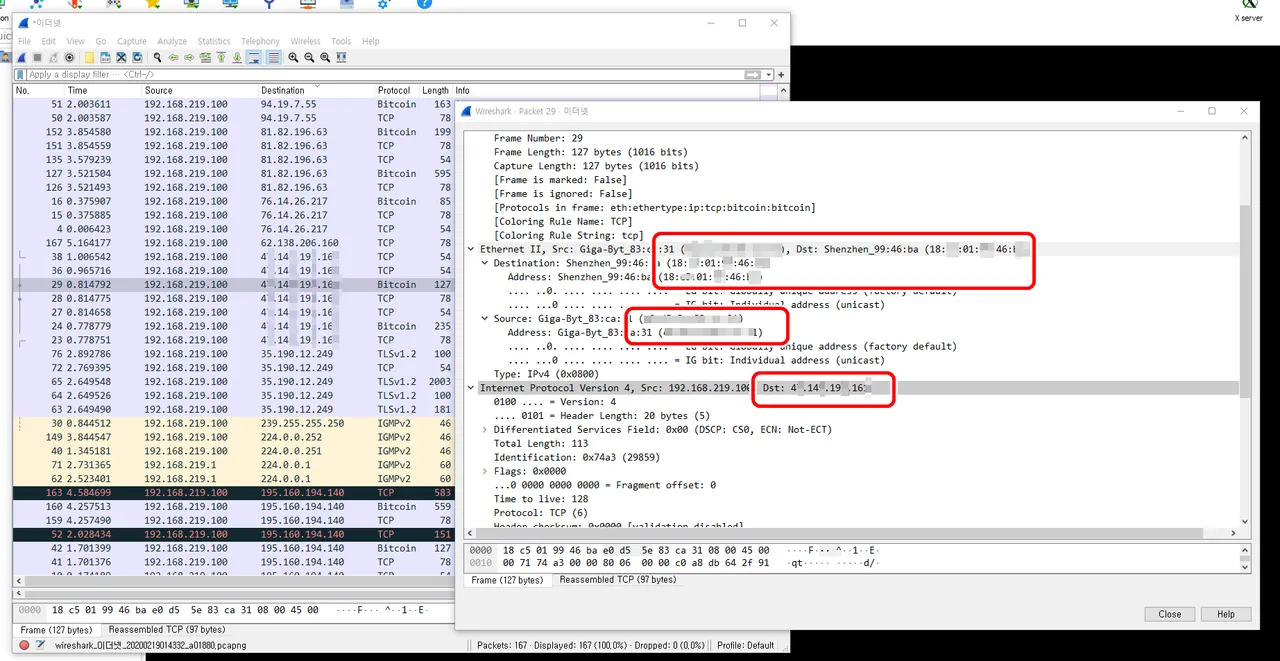
If all ports of the node IP above are open, man-in-the-middle attack (MITM) is possible.
The packet of the node IP is intercepted through the wireshark. Port 8333, a port of Bitcoin Node IP, is a peer-to-peer protocol configured over TCP that can query packets between peers and nodes on the wireshark.
After intercepting the packet of the node IP through the wireshark, accessing the server of the node IP through the browser confirmed that the Linux server was installed. In addition, Wireshark was able to collect data communication information of 4x.14x.19x.16x: 8333.
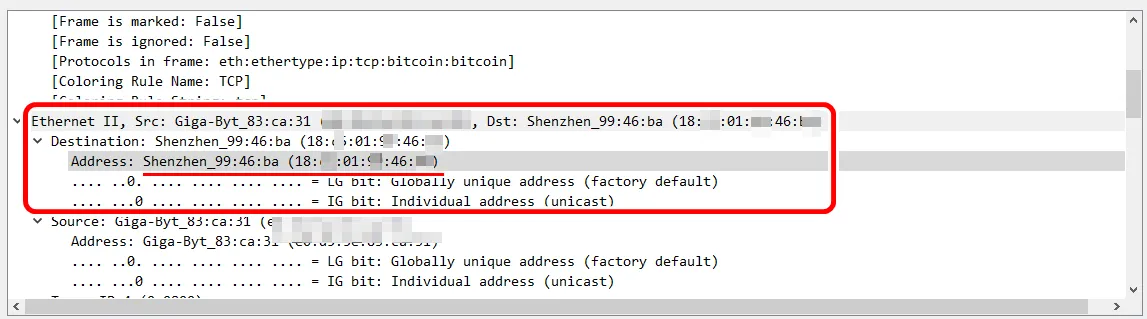
It's impossible to assume, but most Bitcoin mining pools run through Linux servers, so given that the node IP is a Linux server, there is a possibility that the node is a Reference Client, and if so, the wallet It is 100% in the physical operating system space of Node IP.
Conclusion: Yes, Bitcoin network, private keys, and the system itself cannot be hacked. BUT The value of "bitcoin" or "blockchain" depends on how many nodes make up the network and how many members build the community to create an ecosystem. Thus, if the 'nodes' that make up the Bitcoin network are smashed by hackers, the Bitcoin ecosystem will collapse and lose its value as a means of exchange regardless of its decentralized philosophy.
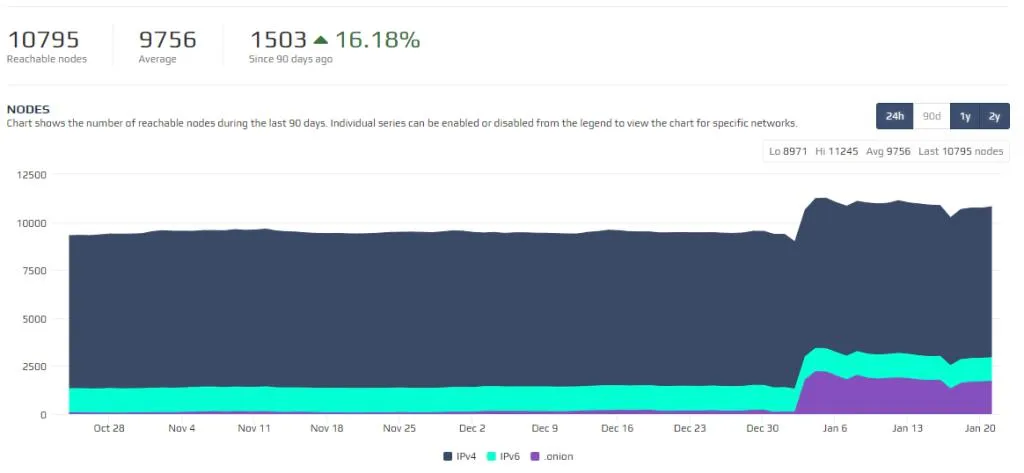
Since Bitcoin Core has been updated to version 19.0.1, anonymous nodes have soared, accounting for more than 17% of all nodes. The share before the update was 2%, which was much lower, but now the number of anonymous nodes has increased, contributing to the security of the entire network. However, many nodes still exist in the public network and are vulnerable to security.
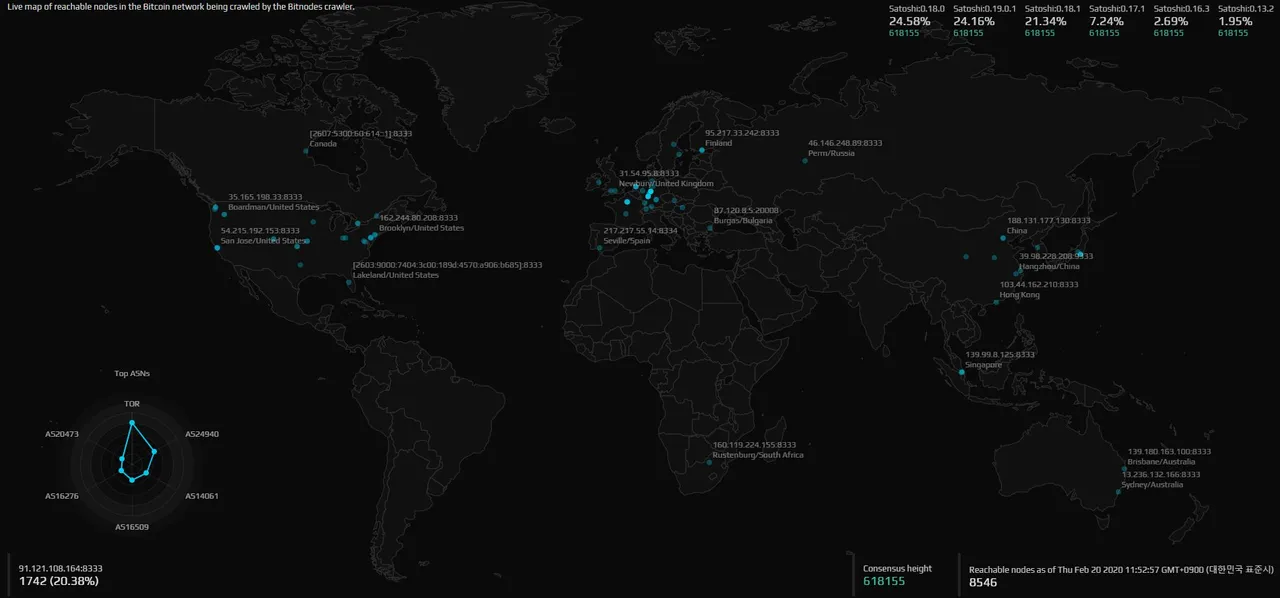
Bitcoin Core version 19.0.1 occupies 24.16% of the total market share, with more than 70% of the nodes still contributing to the network via older cores.
If there is no security for the node IP of the above attack target, it is also possible to take over the node system through the brute force attack or session hijacking the target node IP, take the private key, or transfer the mined Bitcoin to another wallet. Will arise. No, maybe it's happened so far.