
Background
I recently wrote about the no-brainer goodness that is Google Advanced Protection.
One of the drawbacks I mentioned was that getting it to work on mobile devices was a bit of a pain, especially iOS. The good news is Google has recently fixed this.
It use to be you had to use a Bluetooth based security for Google Advanced Protect to work with iOS. Apple's proprietary lightning port has had key support, but the support is very limited based on apps that decide to support it. iOS 13.3 has greatly expanded support, but developers either seem unaware or slow to support... or both.
iPhones have supported NFC for a few years, but again, app support on iOS has been largely lacking... mostly due to Apple's restrictions from what I understand.

iOS 13.3 FIDO2
iOS 13.3 chooses to support the FIDO2 protocol. What the hell is a FIDO2 you might ask, well, it's the successor to FIDO1... pretty simple right.
In the physical security key realm, there are many competing standards, some keys even support multiple standards. High level--- Common standards are: FIDO2, U2F, UAF, and WebAuthn (and others). I might write about all this in a more detailed post, but FIDO was the precursor to FIDO2.
Google didn't really support FIDO2 until recently, starting with Android 7.0 (yea, I know that's not super recent in tech time). What Google did, was (again high level) use chips in supported Android phones as well as software to essentially allow them to act as a trusted physical key. So instead of buying a Yubikey, you could use your Android as a trusted key.
I still recommend having at least two keys on each account, so if you lose one you're not completely locked out, but it was a great step toward security, especially for the average person. The problem was iOS wasn't supported.
*GASP*
This, I found quite odd at the time given Apple's inclusion of a Secure Enclave. This was a huge and giant leap forward for Apple and anyone that used an iOS device (at the time) and now anyone that uses a Mac with a T1 or T2 chip.
Is a hardware feature of the Apple A7 or later A-series processor. Only iOS devices with one of these processors or a MacBook Pro with the Touch Bar and Touch ID support this feature.
A high level, it's a special chip that can store and validate a password. It's basically impossible to hack (without physical access, and even then); I'll maybe cover this again in the future. The neat thing about this... it also provides a way to identify you. When you add your fingerprint or face to the system, the system essentially creates a hash of that. If an application wants to use that to authenticate you (aka you log in to an app with face or fingerprint) you're authenticated based on the chip saying yes or no. The application passed the info to the chip and the chip responds yes or no, this is much different from the standard password authentication as the password is never shared to the enclave nor does the enclave share a password back.
The weird thing was Google didn't support this... at least from the beginning. Recently Google changed that, and Google Smart Lock app now supports iOS natively, meaning you can use your iPhone as a physical security key... but it gets better!
When I first enabled Google Advanced Protection, it killed my ability to sign in to Google apps on my iOS devices. In theory, it should have worked, but I was never able to get it working... until Google supported iOS as a security key.
I'm A Little Lost

Ok, two things. Thing 1, you can use your iOS device as a key to enable physical 2FA on your google account without having to buy a hardware key. Thing 2, you're able to use Google Smart Lock to login into accounts on iOS devices without a specific Bluetooth key.
This makes your phone a great primary and/or back up key. How often do you not have your phone?
The key (😂) thing I've found is you need to install Google Smart Lock and sign in PRIOR to turning on Google Advanced Protection. I can't get it to work if I set up Google Advanced Protection first. The good news is, if you read my last blog and turned it on, you just need to disable it and quickly install smart lock and reenable.
The Process
- Install Google Smart Lock for iOS
- Add phone with Smart Lock as a key on your Google account
- Add at least one (other) "back up" key
- Enable Advanced Protection
- $profit
The other cool thing about Google Smart Lock is you can generate one-time use codes for other devices to log in that don't support keys well (like the iPad) or that don't already have Google Smart Lock installed. Simply try to login to a Google app and it'll prompt you for a code:
 Open the Smart Lock app on iOS
Open the Smart Lock app on iOS You should be prompted to choose your account associated to Smart Lock (blug?)
You should be prompted to choose your account associated to Smart Lock (blug?)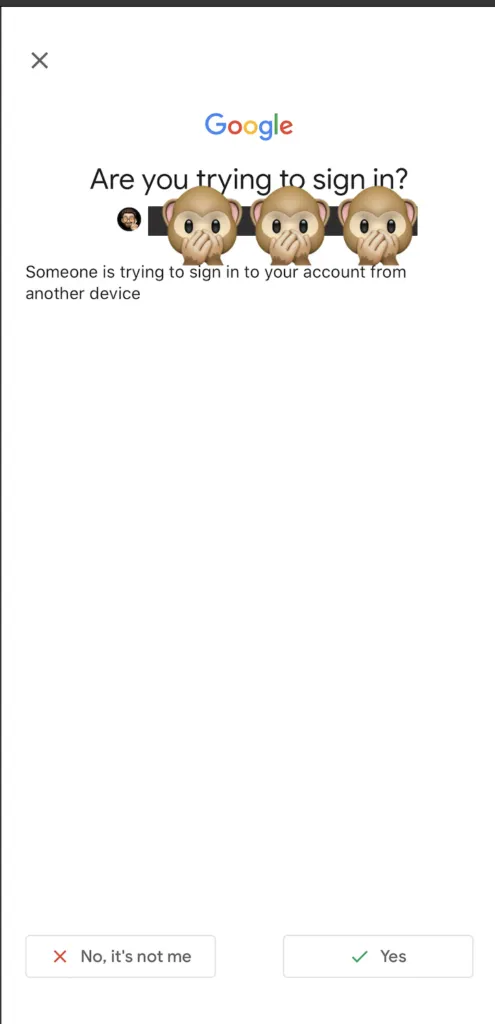 You might be prompted about a log in attempt
You might be prompted about a log in attempt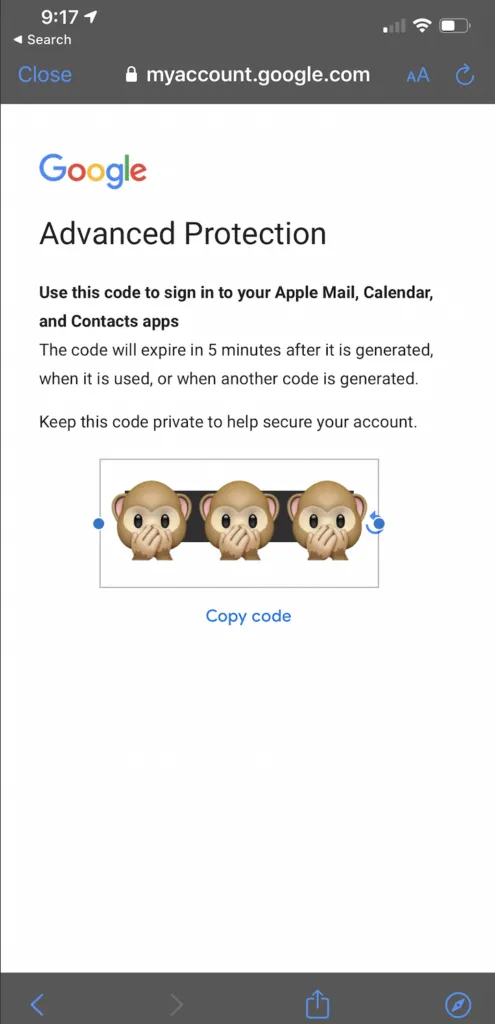 You'll get a code that's good for 5 min to use to authenticate you on the device you're trying to log into
You'll get a code that's good for 5 min to use to authenticate you on the device you're trying to log into
Final Thoughts & Opinions
Google solved my major complaint about using Google Advanced Protection on their platform. Though they don't support every device for this type of authenticate, iOS seems to be functioning well.
Even if you don't enable Google Advanced Protection, you should at the very least add two security keys to your account and disable 2FA text.
About the author:
 Andrew lives in Portland, OR and has worked in tech for over 15 years. With a foundation in philosophy, political theory, and communications, he is an avid thinker & tinkerer, constantly learning and exploring the world around us.
Andrew lives in Portland, OR and has worked in tech for over 15 years. With a foundation in philosophy, political theory, and communications, he is an avid thinker & tinkerer, constantly learning and exploring the world around us.
Originally published on andrewjneumann.com and is best viewed in person. Support | About Andrew | About Site | Feedback| Newsletter
 This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License © 2019.
This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License © 2019.
Posted from my blog with SteemPress : https://andrewjneumann.com/make-your-gmail-hacker-proof-google-advanced-protection-without-a-titan-security-key-on-ios/