These days there is more focus on security then ever before. One of the jobs that is getting more in demand is being a pentester (ethical hacker).
How did I become one
At a very young age I was interested in computers. My first computer was a Amstrad Schneider. For the older ones it maybe rings a bell. It is a XT personal computer from the late 80's. Creating my first personal menu under MS-DOS was a huge achievement. Even more fun of course was how to do things that where not allowed. Changing config files or finding the answers for in game questions by looking into the files. I always wanted to do something with that.
My first years in IT had nothing to do with hacking. I was a system administrator. But I took a new job a few years ago and I got the change to learn the skills of hacking and forensics. The forensics part helped me a lot when I was figuring out @timsaid crazy last puzzle in cryptochallenge #1.
Is it something for you?
Very different people are working as a ethical hacker, with different types of backgrounds and skills. The thing that we have in common is a love for technology and the challenge it provides us.
Some people become specialists in areas, like web applications (sql), network systems, social engineering, etc.
There is no special education you have to follow to become a hacker. This is partly true for ethical hacking. But employers and clients do look at certificates also. For example the Licensed Penetration Tester path from EC-Council is a nice to have.
I do not pretend to be a real hacker. For me personally that is someone who can find the big issues without the help of special tools. What I do is using my knowledge of systems and hacking methodologies.
How does it work
Before you hack anything you have to deal with one of the more boring parts of the job. You need to get permission. And that is more work then you think. You need to talk with the suits(yeh indeed) and make documents what you want to do. This can take away the freedom a little, but it is necessary. Specially for your own protection.
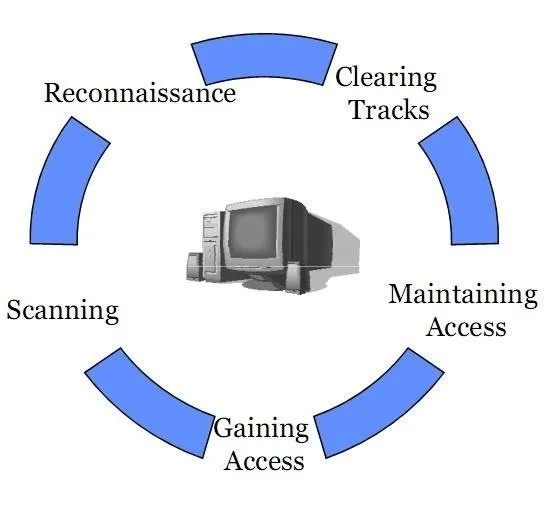
After the formalities we can start hacking. Basically we follow 5 steps. Counterclockwise.
There are special linux distro's like Kali and Backbox who follow these 5 steps. They have the tools needed for every phase sorted out for us. Of course using tools do not make us successful. We need to read and understand the results and make them to good use later in the process. There is no one click hack, and there is always some manual scripting and tuning involved.
So how does it look like
First a small disclaimer: Don't hack anyone without permission!
As a example I will use a web application issue we still see in the wild.
-
Phase 1—Reconnaissance
First we figure out as much as we can without ringing any alarm bells. Just use google, whois, shodan (internet of things search engine) etc.
-
Phase 2—Scanning
Here we start using tools like nmap, nessus (vulnerability scanner), ZAP (OWASP)
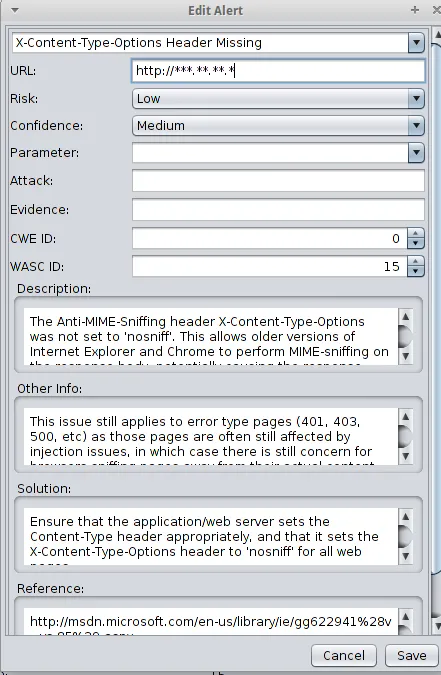
For a web application we will use ZAP. And after our scan we have found this interesting alert.
-
Phase 3—Gaining Access
Well this phase is a lot of fun. We did our home work and we found some issues. But now we need to get in. One of the tools to help us with that is Metasploit. It will provide us with a listener and creates a backdoor for us. We can choose between various types of backdoors. Like using TCP or DNS protocol for the communication. And it can create the backdoor in different languages like php. Because it is a webserver a php backdoor is a logical choice. So we will create one.
Now we have created a php backdoor we want to upload it. Normally we can not upload php files. We will get a nice message telling us the file type is not allowed. But often it is still possible. Sometimes by just changing the extensions. Even something as changing the extension from php to .php%00.jpg or .Php3 can work. But that is a little old school and most of the times it will not work.
So for this case we will use burp. Burp is a java application that has many features. One is being a Intercepting proxy. It let us read everything that is send and received between us and the web application.
So this is how a upload of a php file looks like.
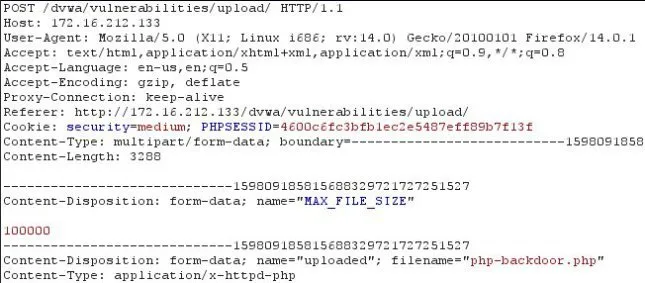
As we can see in the Content-Type there is the MIME value "application/x-httpd-php". If we ever want to get the file uploaded this value has to change. And the burp suite will also let us edit the post request before sending it back. So the value will be changed to image/jpeg (which is allowed).
Now the php file is uploaded we need to start it. We can do this by just typing the url http://steemit.com/uploads/php-backdoor.php ;-) in our browser. Now we will have a connection to our metasploit listener and have access to the server. From there we can try to escalate your rights if needed.
-
Phase 4—Maintaining Access
After we have gained access we want to keep it. So the idea is to make your backdoor persistent. There are many ways to do it. It all depends on the rights we have gained. Metasploit can also help us with that. Sometimes it as simple as typing: run persistence -X (so the backdoor starts after the reboot)
-
Phase 5—Clearing Tracks
And when we are done hacking we want to clear our tracks. Deleting log files or changing file attributes (date/time) etc.
This is of course a simplified version of doing a ethical hack. But it gives you a idea about how it works. It is a lot of fun.
After the hack we need to make a report. We need to state the facts and help the client by providing solutions they can implement.
What your client thinks
Sometimes they expect the ethical hacker to have superpowers. And that we can find everything. But we can not. There is no 100% change that we know about all issues. You can not prevent every attack from succeeding. But what you can do is take the easy attack factors out, mitigate risks and limit a possible hack.
As a ethical hacker you can scan and test all day long. But a big part of the problem and also the solution is the internal IT department. This is often overlooked by management. They do not want to spend more then is needed at security.
Want to know more?
If you want to know more just react to this post. I am also often in the chat room of the cryptochallenge. My account name is the same as on steemit @disofdis