A post on reddit triggered my will to explain this. TL;DR: some random person's bitcoins and ethers were stolen; he says he "never" provided his seed (I'll explain later) to anyone and he is not a victim of phishing. After answering a few comments, the truth is discovered: he downloaded a fake app that requested that he provide it with the seed, the seed was sent to hackers, all hope is gone.
So; how did this happen? in order for this to happen, several failures had to occur. The first is the seed. Now, what is a seed? A seed is a 24-word passphrase that is basically a backup of your bitcoin wallet. I wrote about it when explaining how to backup your wallet. In BIP-39 an improvement to the bitcoin protocol was implemented: each wallet has an "easy to store" seed, comprising of 24 words, that generate the private key. These words should be kept safe in storage, and only used to restore the wallet. I use cryptosteel (not an affiliate link) in order to backup my seed.
Now, the first thing that a hardware wallet tells you is to never put this seed on a computer. It should always be typed into the hardware wallet itself (there's something a bit different on Trezor One ). This is the first rule of recovering a wallet: never, but never, I mean never type your seed on a PC.
So, the poor chap that had his coins stolen broke this rule. Why did he break the rule? because he saw an error message that said "please restore your wallet". Now, this is one of the reasons that you always need to question authority. Even when software prompts for a password, you need to stop and think on what you're doing. Is this the right site or app? Why is it asking this.

I've just finished Ira Winkler's "You CAN stop stupid", a book about security, cybersecurity and the human factor. Ira keeps repeating a large percentage of people fall for phishing scams no matter what we do (and he's right ).
So; if we know that the vector is to make people type their seed into a PC, we know what we need to stop. When the first hardware wallets were planned, there were multiple vectors they envisioned, and had safeguards to stop them: the first was a man in the middle attack. Meaning, someone would gain control over the PC (or phone, but when I say PC I mean the device that is connected to the network) or the network connection and then, when I try to send my coins, it will send the hardware wallet a different transaction. This is why there's a double verification in these wallets. When you send a transaction (or receive, BTW), you're prompted twice: once on your PC and once on the device, and you need to verify the transaction.
The second vector was a keylogger; this means that someone has a listening device on your PC. This was neutralized by doing all the important stuff on your hardware wallet: the PIN is programmed there, the seed is programmed there and the transaction needs to verify there. This means that even if someone has control over your PC, without pushing the actual buttons on the hardware wallet, they can't take away your coins.
But the fact is, that having such a good device still has the STUPID vector: people giving away their seed backup. The seed is the central point of failure: if it gets lost, you lose access to your coins, if it gets stolen, you lose access to your coins, if someone corrupts your seed, you lose access to your coins.
Now, add to this that Ledger, one of the major players in the hardware wallet industry suffered a severe hack that exposed email addresses. This means that if you were on this list, you most likely receive a dozen phishing emails per day. This is how they act.
First, you receive a message which is meant to scare you: there is something wrong with your device; please log in.
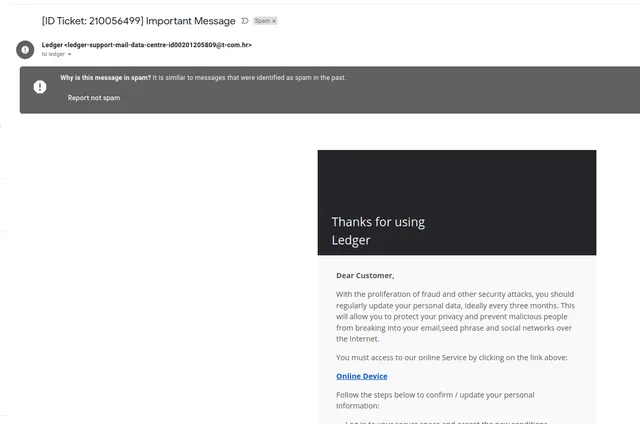
Then, when you click this link, you will be transferred to a page where fake software would be downloaded.
So what do you have to do in order to have better seed protection? the first is a backup; this means that you mitigate the risk of losing your seed. The new Trezor wallets have a Shamir Backup that provides excellent protection and recovery. The second is doing something in order to avoid having the seed written down on any PC.
But you want to mitigate the risk of people entering their seed on a computer. In order to do this, you need to make sure it would be extremely difficult to enter the seed on a PC, while it would be extremely easy to do so on a hardware wallet.
The BIP-39 mnemonic is extremely easy on a PC compared to a recovery on a hardware wallet. If we want to go from there to a new implementation, we need to use non-standard characters that are unique to the hardware wallet. Something like the Klingon alphabet or Ugarit. These are theoretically existent on a PC, but if some phishing software would request the 24-word seed, then a person typing it would need to install an Ugarit keyboard.
In this case, if we're a hardware wallet company, we can purchase ads on the Google search for Ugarit keyboard, saying something like "did a software ask for your 24-word seed and you're looking for an Ugarit keyboard? you're being scammed".
Adding this stage would increase security.
Now; the problem is that the 24-word vector is the most used one, and the one that most people fall to. It is increased due to the recent hack to the Ledger database that caused targeted phishing scams. So in order to mitigate this, you need to reduce both the motivation and the ability of hackers to target people. Google is doing a great job with identifying phishing emails; but that's not good enough. Some people still fall to this scam.
We, as a community need to better explain to people, again, how important is the 24 word seed; but we still need to understand that people will fall to this scam.
