1. What is an Information Security Assurance ?

- It is the administration and safeguarding of information, knowledge, and data. It is also a practice of preventing illegal access and use. It is a quality or state of being secure to be free from risk and it is for PPT (People Processes or Technology) and not only for equipment or devices. And data security has become more crucial as a result of information assurance. Information assurance is the process of ensuring data and managing risks associated with its use, processing, storage, and transfer.
Example: Security audits, database management .
2. Components Information Security Assurance?

- CONFIDENTIALITY - Ensuring that information is accesible only to those authorized to have access.
- INTEGRITY - Safeguarding the accuracy and completeness of information ang processing methods.
- AVAILABILITY - Ensuring that authorized users have access to information and associated assets when required .
3.Differentiate the certification programs to Common body language?
- A certification program is a training program provided by an organization or firm to its members in order for them to demonstrate that they have reached a certain level of expertise within a certain time frame. While Body Language is a type of nonverbal communication that includes physical behavior, expressions, and mannerisms, it is also utilized to communicate.
4. Differentiate the Governance and Risk management?
- Governance is the overall system of rules, practices, and standards that guides a business, whereas Risk Management is the process of evaluating the likelihood of loss or harm and then taking steps to mitigate the potential risk.
5. Different between Security Architecture to Design?
- A security architecture is a unified security design that covers the requirements and dangers associated with a certain scenario or environment. A design is either a plan or specification for the building of an object or system, or the output of that plan or specification in the form of a prototype, product, or process.
6. Different between Business Continuity Planning to D-i-s-a-s-t-e-r Recovery Planning?
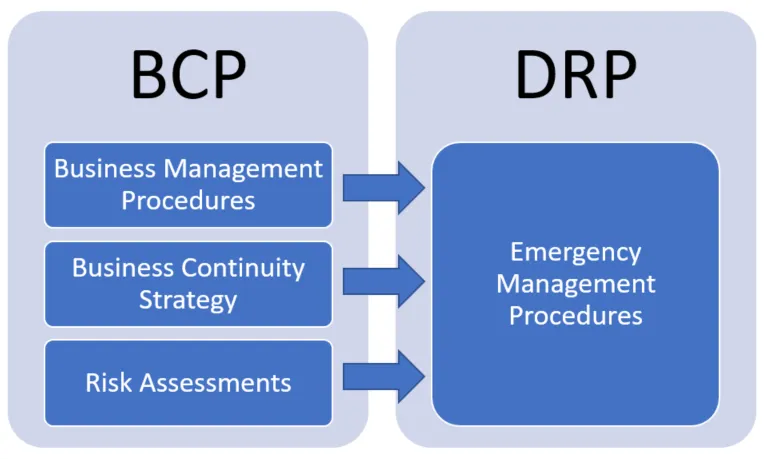
- Disaster recovery focuses on recovering data access and IT infrastructure after a disaster, whereas Business Continuity Planning focuses on keeping Businesses running during a disaster. Meanwhile, a Disaster Recovery Planning ensures that an organization may resume normal operations following a crisis.
7. What is Physical Security Control ?

- Physical control refers to the application of security measures inside a defined structure to dissuade or prohibit unwanted access to sensitive information. Closed-circuit surveillance cameras are one example of physical controls. Alarm systems based on motion or temperature.
8 What is Operations Security?

- is a process that identifies critical information to determine if enemy intelligence can observe friendly actions, determines if information obtained by adversaries can be interpreted to be useful to them, and then implements selected measures to eliminate or reduce adversary exploitation of friendly critical information.
9. What is Law?

- a set of norms that a country or society acknowledges as governing its citizens behavior and that it can enforce through the enforcement of punishments.
10. What is Investigation?

- It is a comprehensive search for facts, particularly those that are hidden or need to be sorted out in a complicated circumstance. An investigation's main purpose is to figure out how or why something happened. In most cases, investigations are formal and official.
11. What is Ethics ?

-Ethics is based on well-founded moral principles that dictate what people should do, usually in terms of rights, obligations, societal advantages, justice, or specific qualities.
12. What is Information Security?

- Information security refers to preventing unauthorized access, use, disclosure, disruption, alteration, or destruction of data and information systems.
