A few antivirus items are influenced by an outline blemish that permits malware or a nearby assailant to manhandle the "reestablish from isolate" highlight to send beforehand recognized malware to touchy territories of the client's working framework, helping the malware pick up boot ingenuity with hoisted benefits.
Florian Bogner, a security evaluator at Kapsch, an Austrian digital security organization, found the blemish, which he's holding track under the codename of AVGater.
Some antivirus sellers issued refreshes
Bogner says he advised all antivirus creators that he tried and discovered helpless. Today, the analyst distributed his discoveries after a few organizations issued refreshes.
The rundown incorporates Trend Micro, Emsisoft, Kaspersky Lab, Malwarebytes, Ikarus, and Zone Alarm with Check Point.
He says different organizations will discharge settles in the coming days, and that he doesn't decide out that other AV motors that he didn't test may likewise be powerless.
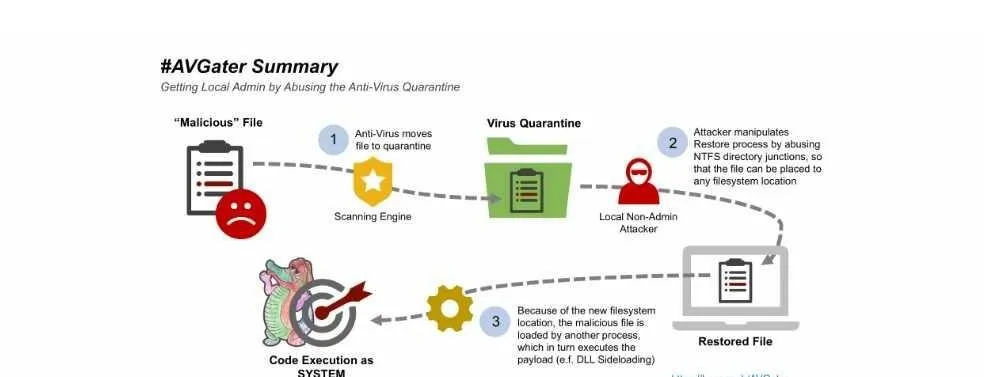
How AVGater functions
To better see how the blemish functions, it's less demanding to lay out an effective abuse situation:
Stage 1 - User gets contaminated with malware
Stage 2 - AV motor distinguishes malware
Stage 3 - AV motor moves malware to isolate
Stage 4 - A nearby aggressor with non-administrator get to runs an adventure on the influenced framework. This endeavor code utilizes NTFS catalog intersections to control the isolated example's unique record area.
Stage 5 - Attacker starts a "Reestablish from isolate" operation.
Stage 6 - Infected document is sent back to its area, yet the NTFS intersection transfers that record to a touchy organizer inside C:\Windows. A non-administrator client would not have the capacity to duplicate records inside this envelope, however antivirus programs work under SYSTEM benefits, which implies the document reestablished from isolate will be sent to that organizer without activating blunders or cautions.
Stage 7 - Because a few Windows administrations or center procedures are intended to stack/run all DLLs put away in particular Windows registries, when the client reboots his PC whenever, the beforehand isolated document will keep running at startup as a major aspect of a Windows benefit or whitelisted application.
The whole assault is wickedly astute, taking into account both boot constancy and benefit heightening, yet depends on assailants with physical access to the machine, a genuine impediment much of the time.
In any case, there are situations where AVGater can demonstrate valuable. For instance, in shared office, instructive, or government situations where clients share PCs, on Windows-based ATMs, and others.
Bogner, who distributed verification of-idea code for misusing the Emsisoft and Malwarebytes AVs, says that clients can avert AVGater by continually refreshing their antivirus items, and on account of big business situations, by not enabling clients to reestablish records from isolate.